13.1 Social implications: Email and internet safety
|
Previous
Chapter 12: Internet communication
|
Next
Chapter 14: Information management
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 13.1 | Social implications: Email and internet safety |
 At the end of this chapter, you should be able to:
At the end of this chapter, you should be able to:
- Identify email threats, issues and prevention methods.
- Use email and the internet safely.
INTRODUCTION
The email and internet are not always safe and secure. You might receive emails from scammers and cybercriminals who are looking to get information from you, such as your banking information and passwords. You should, therefore, avoid storing any sensitive information, such as credit card numbers and passwords on your computer, or sending details to anyone asking for them. In this section, we will look at email threats and what you can do to ensure safe email and internet use.
UNIT
13.1 Social implications: Email and internet safety
In 2015, a computer security firm called Kaspersky Inc. uncovered a computer attack by a group of Russian hackers against banks from around the world. These hackers used a “phishing attack” to infect computers on the bank’s internal network with a virus. Once they gained access to a bank employee’s computer, they used the computer to gain access to the security cameras inside the bank’s offices.

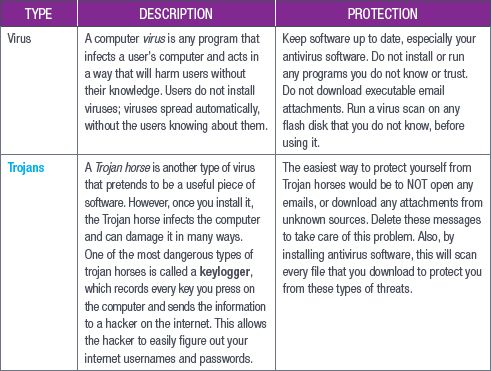
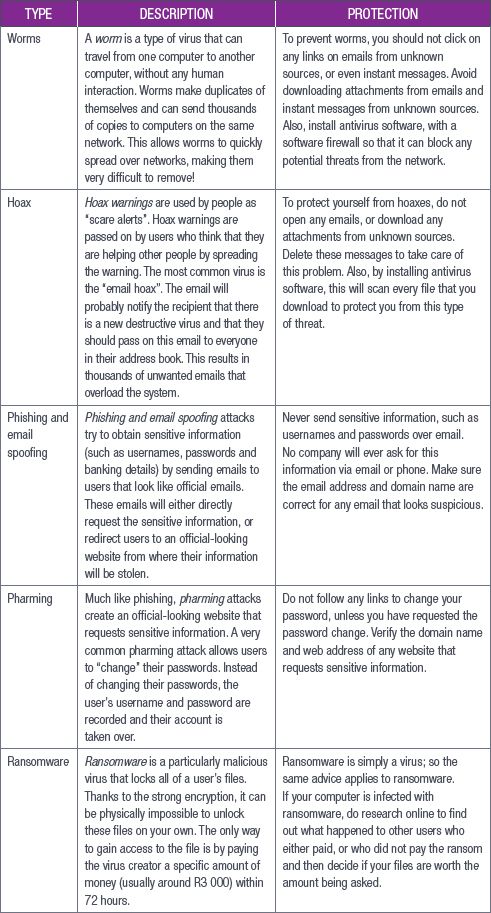
The following table shows the common email and internet threats, as well as what you can do to protect yourself from potential threats.
Table 13.1: The most common threats

UNDERSTANDING SPAM AND PHISHING
COMPUTER CRIMES
Although ICTs are useful, various computer crimes can take place if you are not careful enough. In this section, we will look at the following different types of computer crimes:
- Information theft
- Data theft
- Identity theft

Something to know
Computer crimes are also referred to as “cyber crimes” or “e-crimes”.
INFORMATION THEFT
Information is one of the most valuable resources available to people who are looking to exploit or cause others harm. These kinds of people commit fraudulent acts and can access personal information through hacking into someone’s computer files. We call them cybercriminals.
A cybercriminal can have access to the following types of information:
- Personal information: Personal information, such as your identity number, can be used to steal your identity. This allows the cybercriminal to open store accounts and apply for loans using your personal information.
- Financial information: Information about your banking details can give the cybercriminal access to your banking accounts, steal your money and do online purchasing.
- Social media information: If a cybercriminal has access to your social media accounts or information, the cybercriminal can exploit your friends and family by impersonating you. This can be done by sending a message to people asking them for money, or a message containing a virus that will allow the cybercriminal to exploit more people.
- Interests: Information, such as your likes and interests, can be very valuable as it can be sold to companies. The companies then use this information to tailor make advertisements and specials that are specifically aimed at you.
To avoid these problems, do not share your sensitive information unnecessarily and make sure to protect your information using a strong and secure password. While sharing information is part of using the internet, be selective about the websites with which you choose to share your information. If you use your email address for every website you visit, do not be surprised if you start receiving consistent spam emails.
IDENTITY THEFT
Identity theft is when someone else pretends to be you. This is very similar to information theft. Here, the criminal is illegally obtaining information about you. This type of criminal can use information, such as your full name, date of birth, passwords, email address and bank card details to gain access to your bank account or smartphone.
Cybercriminals can use this information to steal money from you, or even sell your information to others.
DATA THEFT
Data theft can refer to two different crimes. We will now take a look at each of these in some more detail.
The first is the theft of data caused due to a third-party gaining access and using your internet connection without your knowledge. To protect yourself against this form of data theft, you can do the following:
- Protect your network by using a username and password.
- Make sure to keep your username and password secret and do not share it with people you do not trust.
- If you suspect that someone has obtained access to your network, change your username and password.
The second type of data theft is hotlinking. Hotlinking is when someone takes a file or video from their website and links it to your website. This is problematic, as each time a user clicks on the link to download the file or view the video, your bandwidth will be used.
 Activity 13.1
Activity 13.1
Mrs Abrahams loves shopping online. She surfs the internet and every week, she purchases something new. One day she realised that there were purchases made that she did not make herself.
1.Explain how ICTs have benefited Mrs Abrahams in this context.
2.List one disadvantage of ICTs used in this context.
3.Briefly explain what Mrs Abrahams could possibly be the victim of.
4.Suggest what she can do to remedy the situation. Motivate your answer.
SAFE INTERNET AND EMAIL USE
To avoid most of these problems, computer experts suggest the following rules:
- Use a secure password: A good way to create a secure password is to use three or four randomly selected words as your password. Also, include numbers and symbols. “Correct!Horse2Battery&Staple” for example, is easy to remember and difficult to hack.
- Pay careful attention to the websites and links you open: Make sure you know where a link is taking you to and verify that the web address is the same as the website you expected to visit.
- Do not share sensitive information unnecessarily: While sharing information is part of using the internet, be selective about the websites with which you choose to share your information. If you use your email address for every website you visit, do not be surprised if you start receiving reams of spam emails!
- Do not open suspicious emails: You can identify suspicious emails when they are from unknown or suspicious email addresses, emails that seem too good to be true, emails that request sensitive information, emails with executable attachments and emails with poor spelling or grammar.
- Do not download suspicious programs or attachments: If you do not know who the sender of the email is, never download the attachment. Even if you know who the sender is, but you are not expecting an attachment, do not open it. Your friend may have been hacked and sending a virus!
- Keep antivirus applications up to date: The antivirus application is your last line of defence against viruses. By keeping it up to date, you make sure that it knows how to detect all the latest security threats.
- Keep other software up to date: Software weaknesses or vulnerabilities can be used by hackers to gain access to your computer. One of the main reasons that programmers release updates, is to fix these vulnerabilities.
- Use two-factor authentication whenever possible: Two-factor authentication prevents anyone from logging into your accounts using just your username and password. Instead, it needs a second factor (which is usually a physical device, such as your phone) to access your account. This means that your account can only be hacked by a small number of people with access to your phone.
 Activity 13.2
Activity 13.2
1.Define the following email terms:
a. Hoax
b. Spam
2.Study this example of phishing:
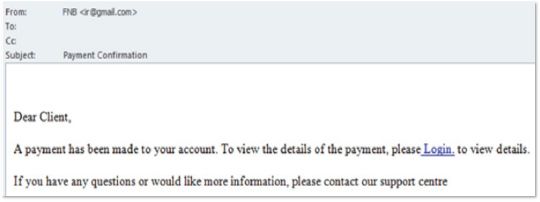
a. Describe two features in the email that confirm the email to be a phishing attempt.
b. Explain the main difference between phishing and pharming.
3.Study the following extract from a case and answer the questions that follow:
Mike was the head of a new division of End Corp., a small company with about 45 PCs. Mike was hired to reduce expenses for the company and so he would only authorise the purchase of one copy of each software program that the company uses. His rationale was, “we bought it, and we can do what we want to do with it”.
Adapted from: http://www.siia.net/index.php?option=com_content&view=article&id=338&Itemid=351
a. Identify the term that describes this extract.
b. State one possible consequence for the developers of the software programs.
c. State why the URL was provided in this extract.
REVISION ACTIVITY
1.Write down only the letter matching the correct or best answer.
a. A worm is a type of virus that does which of the following?
A. Locks your files and demands that you pay money to unlock them
B. Spreads itself without human intervention
C. Hides your files away
D. Pretends to be a legitimate program (1)
2.Bandile is a Standard Bank client. He received the following message from them:
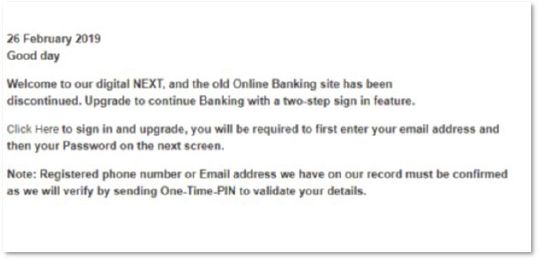
Gmail placed the message in a Spam folder and inserted the following message at the top of the email:

a. What is this type of email called? (1)
b. Gmail disabled all the hyperlinks in the message. Why was this done? (2)
c. Mention one way that Bandile could recognise that this email was not legitimate. (1)
d. What are spam emails? (1)
3.Explain what a hoax email is. Does this type of email normally pose a threat? (2)
4.Explain the difference between data theft and identity theft. (4)
5.You have been asked to create a short presentation for your class on how to stay safe when using the internet and email. Write down five points that you would include in your presentation. (5)
[TOTAL: 17]
AT THE END OF THE CHAPTER
Use the checklist to make sure that you worked through the following and that you understand it.

|
Previous
Chapter 12: Internet communication
|
Table of Contents |
Next
Chapter 14: Information management
|


