5.3 Security and safeguards
|
Previous
Chapter 4: Networks
|
Next
Chapter 6: System software and computer management
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 5.1 | Computer-related crimes |
| Unit 5.2 | Security issues |
| Unit 5.3 | Security and safeguards |
| Unit 5.4 | Impact of technology on the global community |
 By the end of this chapter, you will be able to:
By the end of this chapter, you will be able to:
- Discuss computer-related crimes, attacks and frauds.
- Describe security problems.
- Identify how to avoid security threats.
- List and describe safeguards against cyber attacks.
INTRODUCTION
The internet has made it easier than ever to obtain, share and store information on a platform that you can access from around the world. However, it has also created a new gateway for people with malicious intent to commit crimes against others.
In a world where your computer or smartphone can be used to transfer money with online banking, obtain ID documents and passports, it is important to ensure that you and your information are protected and secure. In this chapter, we will look at some examples of computer-related crimes, attacks and frauds. We will also discuss some security problems that you need to be aware of and how to avoid these threats. We will also give advice on how to protect yourself against cyber attacks.

UNIT
5.1 Computer-related crimes
Computer-related crimes, or cybercrimes, have become more frequent as new methods are discovered to infiltrate your computer. From using something as simple as a virus, to more complex attacks such as phishing, cybercriminals aim to access people’s computers and their passwords. These can then be used to access the users’ bank accounts, steal their identities, or obtain their personal information. Cybercriminals can also use their computers to send spam emails and add unwanted advertisements to every website that the user visits. It is for this reason that computer users need to understand the basics of computer crimes, as well as how to use computers and the internet safely.
TYPES OF COMPUTER-RELATED CRIMES
Computer-related crimes range from physical crimes to crimes committed over the internet. In the sections that follow, we will look at the different types of crime.
THEFT OF COMPUTER HARDWARE
Theft of computer hardware refers to the theft of physical hardware components, which includes internal components, such as RAM and graphics cards, external components such as a keyboard and mouse, as well as the theft of your laptop or smartphone.
Computer hardware is very expensive and is, therefore, very important that you protect yourself against hardware theft. Let’s take a look at some general guidelines on how to protect yourself:
- Never leave your laptop or mobile device unattended in a public place.
- Use passwords as a security method.
- Use a cable to lock your equipment to a table or desk in the office.

Something to know
Piracy is one of the most widespread computer-related crimes in modern society. This is due to the widespread illegal downloading of music, TV series and movies.
SOFTWARE THEFT
Software theft refers to the use and distribution of software obtained by illegal methods. This includes stealing a CD or DVD that contains software, as well as downloading illegal software from the internet (piracy).
Software theft and piracy are crimes in many countries, including South Africa. Therefore, it is important to make sure that you do not partake in these activities.
Let’s take a look at some guidelines to help you stay clear of software theft:
- Do not copy, duplicate or distribute any software without a copyright licence.
- Do not download and use illegal software from the internet.
- Do not lend your software so that an illegal copy can be made.
BANDWIDTH THEFT
Bandwith theft refers to the use of bandwidth without paying for it. People steal bandwith in many ways, which includes stealing usernames and passwords and connections that are not owned by them. Bandwith theft can also occur when one is connected to an unprotected network.
Precautions include:
- Having good password policies.
- Being careful when installing free software from the internet, as it might be malware.
The second type of bandwidth theft is hotlinking. Hotlinking is when someone takes a file or video from his or her website and links it to your website. This is problematic as each time a user clicks on the link in order to download the file or view the video, your bandwidth will be used.
IDENTITY THEFT
Identity theft refers to stealing data that can be used to pretend that a person is someone else. Identity theft can range from stealing any personal information such as your name, your address, your favourite food or more official information such as your ID number, telephone number, etc. The stolen information can be used to take over your accounts on websites like, Twitter, instagram, etc, so as to post messages or use these services whilst pretending to be you. Personal information, such as identity numbers, can be used to impersonate a person (i.e. steal his or her identity). This allows the thief to open accounts, take out loans and buy things in that person’s name.
To avoid these problems, do not share your sensitive information unnecessarily and protect your information using a secure password. While sharing information is part of using the internet, be selective with the websites on which you choose to share your information. If you use your email address for every website you visit, do not be surprised if you start receiving a lot of spam emails!

MISUSE OF PERSONAL INFORMATION
Information about you has value. For example, if you use Google to search for the rules of the computer game “Defence of the Ancients” (“Dota”) and then watch YouTube videos about how to play it, your web browser and search engine may record this information. Without you telling them, they have now learned that you like the game and might be interested in playing it. This information is very valuable to people who make games or gaming hardware. Google then takes this information (and all the information it records about the billions of people who use its software) and sells it to advertisers. The next time you open a website, you suddenly see an advertisement for a brand-new gaming mouse in your web browser!
THEFT OF TIME AND SERVICES
Theft of time refers to a person receiving payment from his or her employer for work that the employee did NOT do. This is usually because the person is busy with non-work-related activities during work time. Theft of services refers to the person using company equipment, such as a computer or the internet, for personal matters.
INTERNET-RELATED FRAUD
A scam is a fraudulent scheme used by a malicious person to obtain money or something of value from someone else.
Table 5.1: Examples of internet scams


CROWD FUNDING
Crowd funding is a way for individuals and organisations to raise money from a large number of people. It can be an alternative to using a bank or investment firm. Below are some examples of crowd funding:
DONATION CROWD FUNDING
Donation crowd funding is used to raise money for a cause. It’s not just charities who can do this – groups and individuals can also start crowd funding projects, for example to pay for a community centre or a child’s surgery.
REWARD CROWD FUNDING
This involves funding a project for a set reward. For example, you might give money to help a band record its music and get their album in return. The reward may vary depending on how much money you give. For example, if you gave R20 you might get the album, but if you gave R50 you might get the album and a t-shirt.
LOAN BASED CROWD FUNDING
This is also known as “peer-to-peer” (P2P) and “peer-to-business” (P2B) lending. You’ll lend a certain amount of money, which should be repaid to you with interest over time. So, the idea is you get back more than you lent.
INVESTMENT CROWD FUNDING
Investment crowd funding (also called “equity crowd funding”) typically involves buying part of a company. The part you own is called a “share”. You’ll usually be one of many shareholders, along with other crowd funders, investment firms and people working at the company.
 Activity 5.1
Activity 5.1
1.Write down the correct answer for each of the following questions.
a.When a thief knows and sells the information about what you like and do not like, or do and do not do, what do we call this type of identity theft?
A.Personal information
B.Financial information
C.Social media information
D.Interests
b.Which of the following is NOT an internet scam?
A.Phishing
B.Cryptocurrencies
C.“Nigerian letter”
D.“Congratulations, you have won”
c.You have received an email from your bank saying that the bank is converting to an electronic system and asks you to type in your banking details so that it can be saved onto their system. Which of the following scams fit this scenario?
A.Phishing
B.Cryptocurrencies
C.“Nigerian letter”
D.“Congratulations, you have won”
2.Choose a term or concept from Column B that matches the description in Column A. Write only the letter next to the question number.
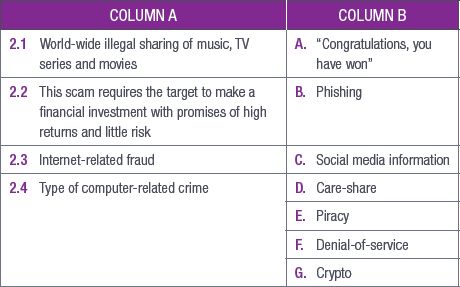
3.Answer the following questions:
a.What steps can you take to protect yourself from computer hardware theft?
b.Explain bandwidth theft.
c.What steps can you take to protect yourself from bandwidth theft where a third party gains access to your internet connection?
d.Explain how other people can misuse your personal information.
e.Describe two examples of internet scams.
UNIT
5.2 Security issues
One of the disadvantages of networks is that other people can sometimes get unauthorised access to computers via the network. Security breaches can occur in LANs, but there is a bigger threat in WANs, such as the internet.
INTERNET ATTACKS
Internet attacks or cyber attacks refers to an attack on the infrustracture of the web itself. Examples include the following:
- Denial-of-service (DOS/DDOS): The use of compromised computers to flood a server with requests for information. The attack can be regarded as successful if the server becomes so overwhelmed that normal users cannot connect to the system.
- Cyberterrorism: Attacks that only occurs in parts of a country’s IT infratructure.
- Spoofing attacks: Spoofing attacks work by masking the attacker and making it seem as if he or she is a legitimate user. This is done by using false data to connect to the network.
- Sniffer attacks: Sniffer attacks works by checking the data packets sent over the network. Hackers use sniffer applications to analyse the network and access all unencrypted data being transmitted.
MALWARE
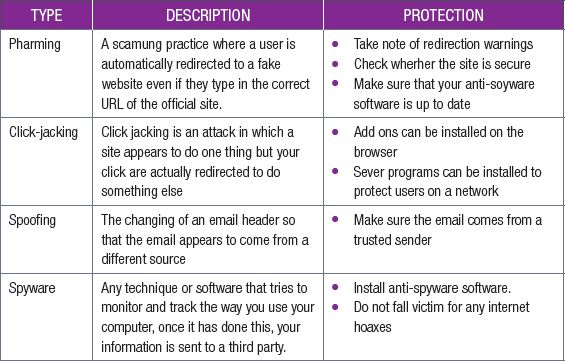
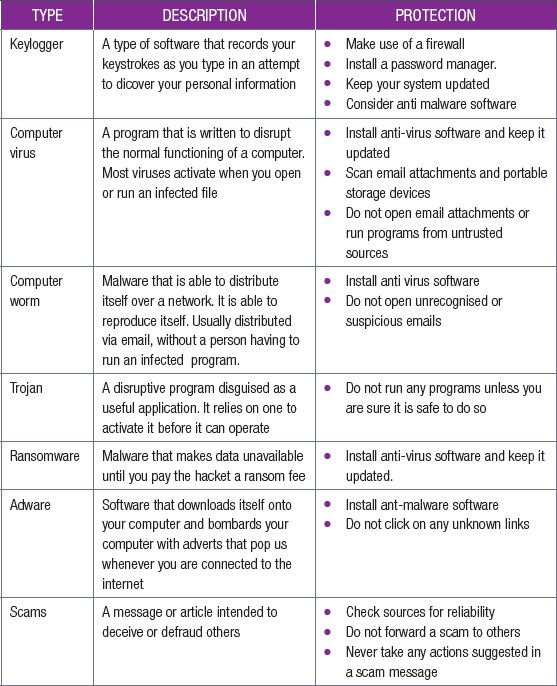
In our modern society, computers and smartphones are used to do everything; from transferring money with online banking, to storing personal information on the cloud. It is, therefore, very important that computer users understand the basics of computer malware, and know how to use computers and the internet safely. Table 5.2 gives some information on the most common threats and how best to avoid them.

Something to know
Malware is a term used to describe software that can be used to cause harm to the user’s computer or computer network, without the user’s knowledge. This includes viruses, Trojans, worms, bots and zombies. Malware programs normally function by causing your computer to perform unwanted actions, such as sending emails and messages to help spread the infection, giving the hacker personal information stored on your computer, or allowing the hacker to take control of your system.
Table 5.2: Common security threats

Something to know
A pop-up is a form of advertising normally found on the internet. The advertisement consists of a small window that suddenly appears (pops up) with a message asking the user to click, in order to claim a prize, gain information on a product, or go to a website for a special offer. Although some of the pop-ups are safe and will provide you with the promised information, there are many that are used in order to spread malware, such as spyware and adware.
BOTS
A bot (short for robot) is a software application that allows the user to automate tasks and actions. On the internet, they are normally used to analyse and gather file information. An example of this is web crawlers. These bots gather, analyse and index data that can be used by search engines, such as Google.
While bots can be used to make the user’s life easier, they often come in the form of malware. Malware bots function by infecting the user’s computer and automatically performing malicious actions, such as gathering keystrokes, obtaining financial information, gathering passwords, or opening back doors on the infected computer.
ZOMBIES
Malware bots also have the capability to completely take over the user’s computer, allowing the hacker to take control. When this happens it is known as a zombie. Hackers can use zombie computers for a wide variety of applications; including launching DoS attacks and sending spam emails in order to spread the malware.
RIGHT TO ACCESS VS RIGHT TO PRIVACY
We know by now that computer crimes depends on access to data. For one to prevent fraud and identity theft one needs to keep their data private and one needs to protect it.
The important part here is to know who has the right to access data, versus your right to keep your data private. Below are a few examples to look at when it comes to the right of access versus the right to privacy:
- If you do your work on a computer owned by someone else, they may have the right to claim access to your data files.
- If you use online services such as Facebook you should be aware that their End User License Agreement states that whatever you post belongs to them.
- If your school has an AUP for the computer lab that you have accepted, you may have allowed people other than yourself to access your data files.

Something to know
Hackers can infect multiple computers in order to create a “botnet”; better known as a “zombie army”.
 Activity 5.2
Activity 5.2
1.Computer viruses often get the blame when we experience problems with our computers. Briefly explain what a computer virus is.
2.How does a computer worm work?
3.Which one of the following is NOT anti-virus software?
A.Avast
B.AVG
C.Sharepoint
D.NOD32
E.Chrome
F.Microsoft Security Essentials
G.Microsoft Office
4.Why is spam a type of harassment?
UNIT
5.3 Security and safeguards
The computer operating system provides support software that provides security for applications. This includes preventing malicious applications, such as a keylogger, from finding out what password you enter on your banking website. Without these protections, malicious software can do incredible damage to your computer and to you as a person.
AVOIDING SECURITY THREATS
The first and best defence against security threats is to prevent them from occurring in the first place. Therefore, in order to help you avoid security threats, let’s take a look at some of the following suggestions:
- Use a secure password.
- Pay careful attention to the websites and links you open.
- Do not share your sensitive information unnecessarily: While sharing information is part of using the internet, be selective about the websites with which you choose to share your information. If you use your email address for every website you visit, do not be surprised if you start receiving a lot of spam emails!
- Do not open suspicious emails: Suspicious emails are emails from unknown or suspicious email addresses, emails that seem too good to be true, emails that request sensitive information, emails with executable attachments and emails with poor spelling or grammar.
- Do not download suspicious programs or attachments: If you do not know who the sender of the email is, never download the attachment. Even if you know who the sender is, but you are not expecting an attachment, do not open it. Your friend may have been hacked and sending you a virus!
- Keep your antivirus application up to date: Your antivirus application is your last line of defence against viruses. By keeping it up to date, you make sure that it knows how to detect all the newest security threats.
- Keep your other software up to date: Software weaknesses or vulnerabilities can be used by hackers to gain access to your computer. One of the main reasons that programmers release updates is to fix these vulnerabilities.
- Use two-factor authentication whenever possible: Two-factor authentication prevents anyone from logging into your accounts using just your username and password. Instead, they need a second factor (which is usually a physical device, such as your phone) to access your account. This means that your account can only be hacked by the small number of people with access to your phone.
SAFEGUARDS AGAINST CRIMINALS, VIRUSES AND THREATS
There are times that you are not able to avoid all the security risks that we have just discussed. Fortunately, there is a solution to this problem. Firewalls and software, such as antivirus and anti-spyware, help protect users against the threats that they cannot see.
FIREWALLS
The firewall is responsible for monitoring all incoming and outgoing traffic on a network. If the firewall detects any traffic that is not within the defined set of security rules, it is blocked. Through this action, the firewall prevents malware from spreading over a computer network.
Examples of firewall software include ZoneAlarm, Comodo and GlassWire. Windows 10 comes equipped with a basic firewall, but this might not be strong enough to protect your computer against powerful malware.

ANTIVIRUS PROGRAMS
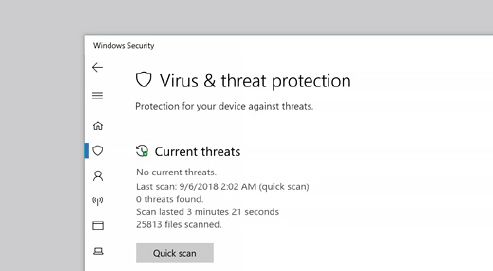
An antivirus or anti-malware is a computer program designed to detect, identify, prevent and remove malware from your computer. The program achieves this by running on your computer as a background process. This allows the program to scan the computer, as well as any external storage devices that are connected to the computer, for malicious software.
Examples of antivirus programs include Bitdefender, Norton and Webroot. Windows 10 comes equipped with a basic antivirus program, called “Windows Defender”. This program should be sufficient to protect you against most threats. However, an antivirus application with more features might be needed for more serious threats.

Something to know
Antivirus programs were first developed to protect users against viruses, hence the name “antivirus”.
ANTI-SPYWARE
Anti-spyware is a type of computer program designed to prevent, detect and remove spyware programs from your computer. The anti-spyware program does this by monitoring your emails, the websites you visit and files you download. If a malicious program is detected, the anti-spyware will prevent it from being transferred onto your computer. Examples of anti-spyware programs include Bitdefender, Kaspersky and AVG.
 Activity 5.3
Activity 5.3
1.Your anti-virus program reports that it has quarantined a virus. What does this mean?
2.ProvIde THREE measures you can take to avoid computer viruses, besides installing anti-virus software and keeping the software up to date.
3.Give TWO examples of firewall software.
4.Your father says that he makes a point of updating his anti-virus software twice a year. Explain to him why this approach is not sufficient
5.A pop-up appeared on your aunt’s computer saying that she should download an anti-virus program from the internet, as viruses had been detected on the computer. Why should she not respond to this warninf, if viruses are so dangerous?
6.Give the name of one popular anti-virus software package.

Something to know
Some anti-spyware programs are designed to only block spyware, while others are designed to block spyware, as well as other malicious programs, such as viruses.
UNIT
5.4 Impact of technology on the global community
With the invention and popularisation of the internet, the world is more connected than ever before. This connectivity has led to the creation of new technologies that have eliminated the problem of distance that we once faced. Not only have new technologies changed the way in which we find information; it has also changed the way in which we communicate, conduct business and meet new people.
COMMUNICATION
In the old days, we were limited to using landline phones to make calls and writing physical letters when communicating over a long distance. If you wanted to meet a person in another city, you had to travel to that city, or organise a meeting at a common location. Fortunately, that is no longer needed. Email, VoIP, video conferencing and smartphones have made communication much faster, cheaper and easier than ever before.
CONDUCTING BUSINESS
The internet has created a whole new platform that we can use to conduct business and to reach new customers. This includes the following:
- Creating online advertisements for products in order to reach more customers
- Creating and hosting online services, for example Netflix and Amazon
- Creating completely new business ideas, for example YouTube and Esports
MEETING NEW PEOPLE
For today’s teens, friendships can start digitally: 57% of teens have met a new friend online. Social media and online gameplay are the most common digital venues for meeting friends The most common spots for meeting friends online are social media sites like Facebook or Instagram, followed by playing networked video games. Girls who have met new friends online are more likely to meet them via social media, while boys are substantially more likely to meet new friends while playing games online.
Text messaging is a key component of day-to-day friend interactions: 55% of teens spend time every day texting with friends. Social media helps teens feel more connected to their friends’ feelings and daily lives, and also offers teens a place to receive support from others during challenging times. For many teens, texting is the dominant way that they communicate on a day-to-day basis with their friends.
DISTRIBUTED COMPUTING POWER
One of most important ways in which technology has impacted our daily lives, is through the invention of distributed computing power. Distributed computing power technologies, such as cloud and grid computing, allow users to store information on the internet, as well as increase their computing power, by using a network where one computer can use the computing power and resources of other computers. This saves users both time and money, as they do not have to invest in expensive processing equipment.
Revision Activity
QUESTION 1: MULTIPLE CHOICE
1.1Which of the following is NOT a computer-related crime? (1)
A.Downloading illegal software
B.Accessing hardware on a shared network
C.Stealing a network’s password
D.Hotlinking
1.2What does DoS stands for? (1)
A.Denial-of-service
B.Data on server
C.Delivery of services
D.Digital office software
1.3Which of the following can be used to launch DoS attacks? (1)
A.Spyware
B.Zombies
C.Worms
D.Phishing
1.4Which of the following is NOT a result of telecommunication technologies? (1)
A.Meeting new people
B.Conducting business
C.Reducing pollution
D.Distributing computer power
1.5What is the purpose of a firewall? (1)
A.Preventing other computers on a network from accessing your computer
B.Removing viruses on the computer
C.Detecting spyware programs
D.Installing anti-malware
[5]
QUESTION 2: TRUE OR FALSE
Indicate if the following statements are TRUE or FALSE. Correct the statement if it is false. Change the underlined word(s) to make the statement true.
a.Malware is software that can be used to cause harm to the user’s computer or computer network, without the user’s knowledge. (1)
b.Identity theft is when someone uses your credentials to access your personal information. (1)
c.You can prevent adware by being careful when installing new applications. (1)
d.All bots are malicious. (1)
[4]
QUESTION 3: MATCHING ITEMS
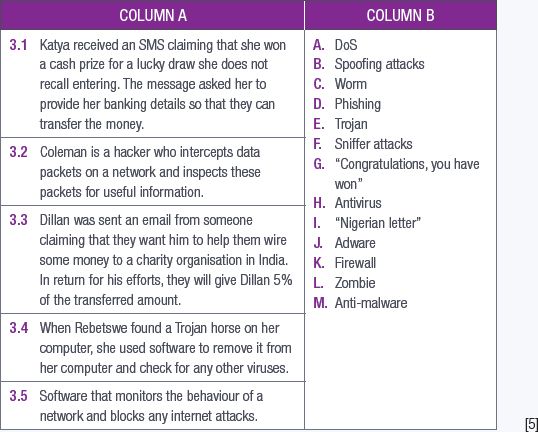
Choose a term or concept from Column B that matches a description in Column A. (5)
QUESTION 4: FILL IN THE MISSING WORDS
Fill in the missing word(s) in the following statements. Provide only ONE word for each space.
a.Businesses create _______ for products in order to reach more customers. (1)
b._______ technologies saves users both _______ and money, as they do not have to invest in buying expensive processing equipment. (2)
c.People can use _______ to meet new people from anywhere in the world. (1)
d.Cell phones allow people to communicate over _______ distances and, therefore, save people money. (1)
[5]
QUESTION 5: SHORT QUESTIONS
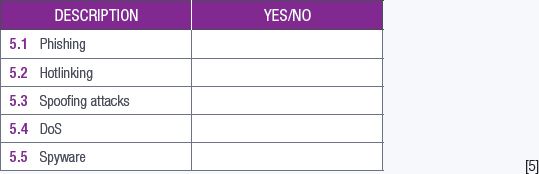
State if the following are internet attacks or not. (5)
PART 6: SCENARIO-BASED QUESTIONS
6.1Carlos recently downloaded a game online. Everything seemed fine at first, until he discovered a new hidden file on his computer. He soon started to notice that his hard-drive memory was starting to get used up, even though he was not installing any large files on his computer.
a.To what type of threat(s) has Carlos been exposed? (2)
b.What can Carlos use to get rid of this threat(s)? (1)
c.Suggest three precautionary measures Carlos could take to safeguard himself against internet attacks. (3)
d.Name five things Carlos could do in the future to protect himself from this type of threat(s). (5)
6.2 Mary downloads a lot of programs as a programmer and animator. Since Mary creates and maintains content for professional companies, she worries that her client’s private information could be at risk.
a.What would be the best safeguard for her current situation? (1)
b.Mention three benefits of the safeguard that you suggested. (3)
[15]
TOTAL: [40]
AT THE END OF THE CHAPTER

|
Previous
Chapter 4: Networks
|
Table of Contents |
Next
Chapter 6: System software and computer management
|

