2.4 File management
|
Previous
Chapter 1: Basic concepts of computing
|
Next
Chapter 3: Basic concepts of hardware
|
 CHAPTER OUTCOMES
CHAPTER OUTCOMES
| Unit 2.1 | The link between data, information and knowledge |
| Unit 2.2 | Number systems |
| Unit 2.3 | Digital character and primitive data types |
| Unit 2.4 | File management |
| Unit 2.5 | Common file types and extensions |
| Unit 2.6 | Social implications |
 Learning outcomes
Learning outcomes
At the end of this chapter, you should be able to:
- provide an overview and link between data, information and knowledge
- explain data representation and data storage?
- discuss bits and bytes
- provide an overview and convert between number systems: decimal, binary, hexadecimal
- provide an overview of digital character representation; ASCII/UTF-8, Unicode
- provide an overview of primitive data types and their storage
- provide an overview of data structures and collections of data storage
- explain computer file management processes
- explain the various software licence agreements
- discuss the social, ethical and legal issues pertaining to ICTs
- list the economic reasons for using computers
- explain the digital divide.
INTRODUCTION
Data, in principal, is stored in 1s and 0s. Computers make use of data structures that describe a specific sequence for data to be organised. This allows the computer to understand how the different bits of data are related and to interpret the data correctly.
UNIT
2.1 The link between data, information and knowledge
In the previous chapter, you learnt that data is unprocessed numbers, or facts.
In order to communicate data and instructions, data such as numbers, letters, characters, special symbols, sounds/phonics, and images are converted into computer-readable form (binary). Once the processing of this data is complete, it is then converted into a format that people can understand. The processed data becomes meaningful information. The information becomes knowledge when it is understood and used by people for different purposes.

EXPLAINING BINARY NUMBERS
DATA REPRESENTATION
Data representation refers to the form in which data is stored, processed and transmitted. Digital devices store data using the binary number system.
BITS AND BYTES
You can combine several bits (0s and 1s). If you combine 8 bits together, it is called a ‘‘byte’’. A byte can represent any number between 0 (represented in bits as 00000000) and 255 (represented in bits as 11111111).

Have you ever heard someone saying that a movie is 700 megabytes (MB) big? Basically, what they are saying is that, the movie consists of 700 million bytes of data.

HOW COMPUTERS WORK
Some of these bytes tell the computer the:
- specific colour every pixel on the screen should be for every frame
- order in which to show the frames
- frequency and the time each different sound is played.
Bits and bytes also store information about the types of data stored. For example, if you are creating your own program, when coding, you work in sections to create the program. In your program, a few bytes might instruct the computer which sections of your program are text, whole numbers, and decimal numbers.
 Activity 2.1
Activity 2.1
2.1.1Differentiate between data, information and knowledge. Use an example to support your answer.
2.1.2Explain data representation, in your own words.
2.1.3Explain data storage.
2.1.4Illustrate the difference between bits and bytes.
2.1.5Decide for each of the following whether it represents data, information or knowledge. Give a reason for your choice in each case.
a.The marks for each learner in a recent mathematics test.
b.The tabulated results of research into bus transport options for a school tour. The table includes records of the safety history of each bus company. The school is able to choose the safest option that is the cheapest.
c.A comparison of the IT marks per learner for terms 1, 2 and 3 of a year.
d.A comparison table of a number of smartphone options in terms of features, price and contract options per mobile service provider.
UNIT
2.2 Number systems
DECIMAL, BINARY AND HEXADECIMAL
In this unit, you will learn how computer number systems work, and how you can calculate the value of a byte using basic mathematics.
DECIMAL NUMBERING SYSTEM (BASE 10)
The numbering system we use is called the decimal system because the prefix ‘deci’ means 10, and there are 10 numbers in the decimal system: 0, 1, 2, 3, 4, 5, 6, 7, 8 and 9.
In the decimal system, each time the value of a number increases by 1, you increase the size of the digit by 1. This works well until you reach the largest digit possible that is 9. Once you are at 9, there are no larger digits left, so the next time you increase the value of your number by 1, you need to add a new digit to your number. The value of this digit increases from 0 to 1, and you restart the first digit at 0:
…
07
08
09
10
When you reach the number 19 and increase the value by 1, the second digit goes up again, and you start with 20. This means that the value of any digit in the second position is 10, with 20 equal to 2 × 10. As you continue counting, the value of your second digit eventually reaches 9 (for example in 90), and when you need to increase it again, (for example when adding 1 to 99) you find that impossible, so you reset both 9’s to 0 and add a third digit, that is 100.
The place value of the third digit is thus always a 100, or 10 × 10 or 102. If you need to know the value of the number 742, you can calculate it as follows:

As your number increases in value, the value of each digit is 10 times larger than the values of the previous digit. The fourth digit is thus worth 1 000 (or 103 ), the fifth digit is worth 10 000 (or 104 ), and so forth.

Take note
Any number raised to the power of zero, for example, 100, equals 1. It does not matter how big or small the number is. So even 1 0000 = 1.
So, to calculate the value of an eight digit number (for example, 51 240 887), you do the following:
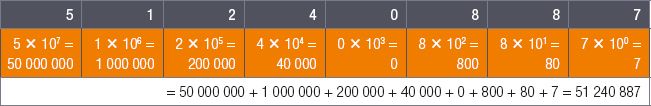
Once you understand that this is how counting works when you have ten unique numbers available, counting in any other numbering system is easy to grasp.
BINARY NUMBERING SYSTEM (BASE 2)
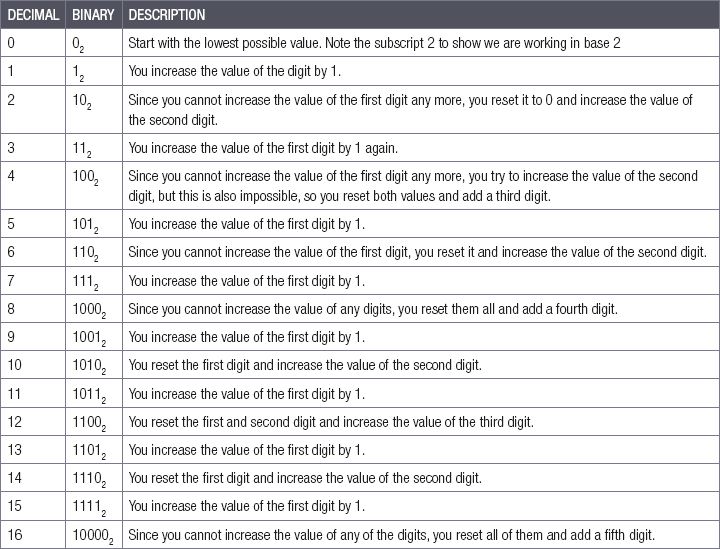
The prefix bi- means two (as in bicycle, biplane, or bilingual), so the binary numbering system is a numbering system in which there are only two unique values: 0 and 1. To count in binary, you use the same logic you use to count in the decimal system. You increase the value of a digit until it reaches the largest digit possible (1), then add a new digit and restart the previous digit.
To see how this works, try to count from 0 to 16 in binary.
Table 2.1: Counting in binary
CONVERTING FROM BINARY TO DECIMAL
How can you calculate the decimal (Base 10) value of an existing binary number? Although one could count to any number in this way, it is not very efficient and would take a long time with large binary numbers. A better way is to use the same technique you used with the decimal system and find out what the place value of each digit is before adding them all together.
To see how we do this, let us look at what the value of each of the digits is on their own.
Table 2.2: The place value of binary digits
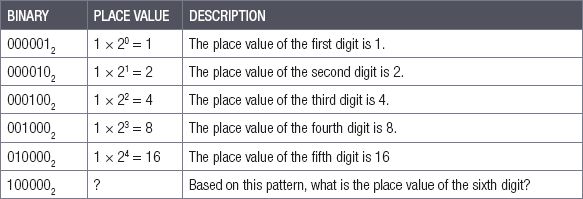
In the decimal numbering system, each digit can hold ten unique values and each new digit has a place value that is ten times as large as the previous digit. In the binary system, each digit can only hold two unique values, so each new digit has a place value that is twice as large as the previous digit!
Just as with the decimal numbering system, you can calculate the value of a binary number by calculating the value of the individual digits and adding them together. Let’s work through the following examples to ensure you understand how to do this.
Example 2.1
Convert the binary number 001011012 to a decimal number.
To convert this binary number to a decimal number, you can use the following steps:
- Step 1: Start by calculating the place value of each position of the binary number.
- Step 2: Add the place values of the digits that are 1 together.
- Step 3: Ignore the place value of the digits that are 0.

Did you know
Remember that multiplying any number with 0 is 0.
You can lay your working out in this manner:
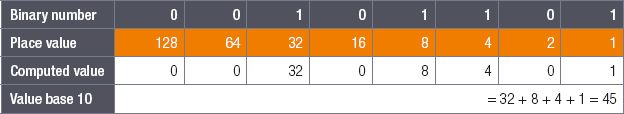
The binary number 001011012 is therefore 0 + 0 + 32 + 0 + 8 + 4 + 0 + 1 = 45.
Example 2.2
Convert the binary number 110000112 to a decimal number.
Using the same technique as in the previous example:
- Step 1: Start by finding the place value of each digit.
- Step 2: Add those place values together for the digits equal to 1.
- Step 3: Ignore the place value of the digits that are 0.
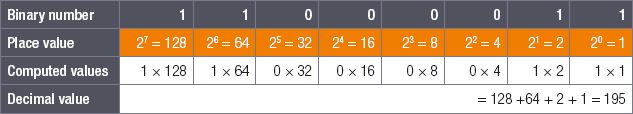
The binary number 110000112 is therefore equal to 195.
Example 2.3
Convert the binary number 111111112 to a decimal number.
In this example, all the digits are equal to 1. This means, you add the value of all the digits together.
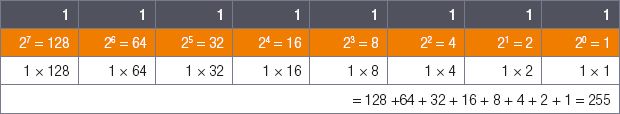
The binary number 111111112 is therefore equal to 255.
CONVERTING FROM DECIMAL TO BINARY
To convert a decimal number into binary, you can use the following steps:
Step 1: Find the largest power of 2 that is smaller than or equal to the decimal number.
Step 2: Divide the decimal number by this power.
Step 3: Write down the answer of the division (1) underneath the power.
Step 4: Rewrite the decimal number in terms of the division and its remainder.
Step 5: Repeat this process with the remainder until there is no remainder left.
Step 6: Write down 0 under all the powers that were not used.
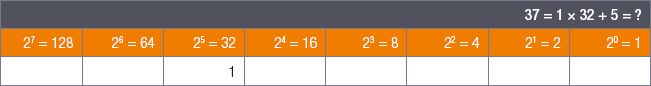
For example, to convert 37 into binary, start by writing down the factors of 2:
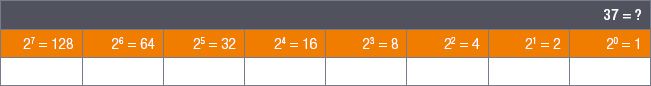
1.Find the largest power of 2 that is smaller than or equal to 37.
2.The answer is 32, since 37 ÷ 32 = 1 with a remainder of 5.
3.Write the number 1 under 32 and rewrite 37 as 1 × 32 + 5:
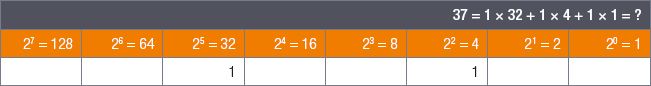
1.Find the largest power of 2 that is smaller than or equal to 5.
2.The answer is 4, where 5 ÷ 4 = 1 with a remainder of 1.
3.This means you can write a 1 under the number 4, and rewrite 5 as 1 × 4 + 1:
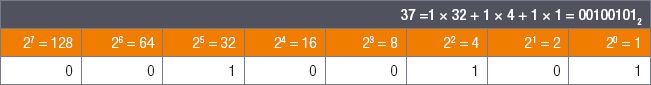
The final remainder is 1, and the power of 2 smaller than or equal to 1 is also 1.
Since 1 ÷ 1 = 1 with no remainder, you can write the number 1 under the 1 in the table.
You should also add 0 under all the powers of 2 you did not use.
The 1s and 0s you have written in your table gives you your binary number:
Work through the following examples to make sure you understand how to convert a number from decimal to binary.
Example 2.4
Convert the decimal number 71 into a binary number.
Step 1: To convert the decimal number into binary, start by drawing the power of 2 table.
Step 2: Work your way from the left of the table until you find the first power of 2 that is smaller than or equal to 71.
Step 3: Once you have this power, write a 1 under it, and rewrite the decimal value as the sum of this power and a remainder.
Step 4: Next, you need to find the largest power of 2 that is smaller than or equal to the remainder.
Continue this process until there is no remainder left.
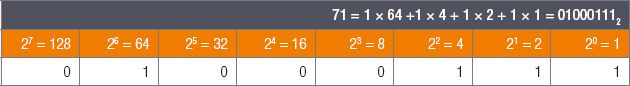
Example 2.5
Convert the decimal number 168 into a binary number.
Step 1: Using the same process as in the previous example, you will that find that the first power smaller than 168 is 128, which leaves a remainder of 40.
Step 2: The largest power that goes into 40 is 32, which leaves a remainder of 8.
Step 3: Since 8 is a power of 2, you know what the value of all the binary digits are and can thus find the binary number.
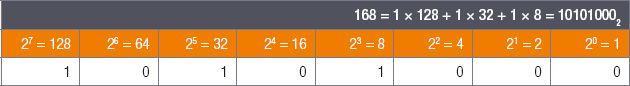
Example 2.6
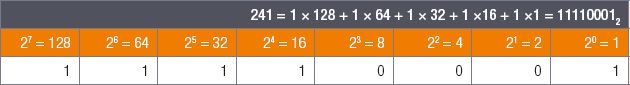
Convert the decimal number 241 into a binary number.
Step 1: Any decimal number between 0 and 255 can be represented using 8 binary digits.
Step 2: Since 241 is smaller than 255, you know that it can be represented using the powers you have been using until now.
Step 3: If it was larger than 255, you would have needed to include more digits in your binary number.
Step 4: Working through the powers from the left-hand side, you will find that the value of the binary digits is 128, 64, 32, 16, and 1.
 Activity 2.2
Activity 2.2
2.2.1Explain in your own words what the decimal numbering system is.
2.2.2Explain in your own words what the binary numbering system is.
Work on your own to complete the following two activities, then review your work with a partner. Compare your answers and if they differ, try to find out where the mistake occurred and correct it.
2.2.3Convert the following binary numbers to decimal numbers:
a.000010012
b.100010112
c.010011102
d.100010002
d.000100012
f.111011112
g.010101002
h.100110012
i.110000012
j.000101002
2.2.4Convert the following decimal numbers to binary numbers:
a.9
b.17
c.93
d.128
e.127
f.254
g.144
h.58
i.210
j.237
HEXADECIMAL NUMBERING SYSTEM
The last numbering system you will learn about in this unit is the hexadecimal numbering system. The suffix -decimal means ten while the prefix hexa- means 6 (as in hexagon, which is a shape with six sides). The hexadecimal numbering system thus has 16 unique numbers.
Table 2.3: The hexadecimal numbering system
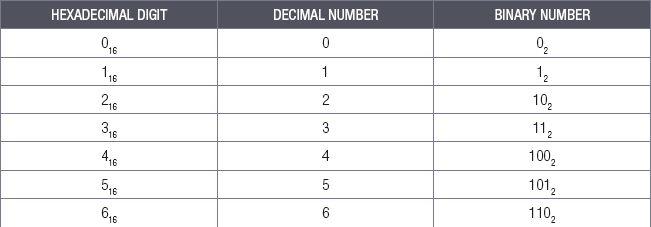
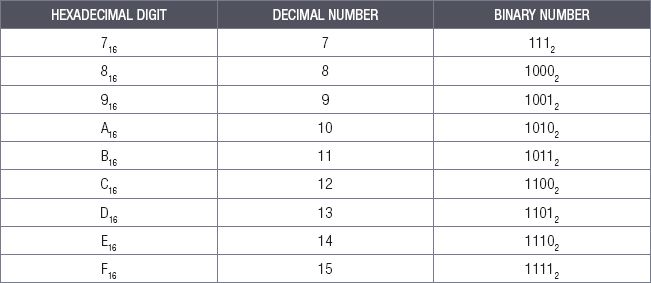
The hexadecimal system uses the first six letters of the alphabet in its numbering system, with A equal to 10, B equal to 11, C equal to 12, D equal to 13, E equal to 14 and F equal to 15.
To count using hexadecimal, you follow the same rules as you do when counting in the decimal or the binary numbering systems. You continue increasing the value until you reach the largest possible digit (F), then reset this digit back to 0 and add a second digit.
Every time you pass the maximum of the first digit, you increase the value of the second digit until both the first digits are equal to F, in which case you reset both digits and add a third digit.
 Case Study Why do we use the hexadecimal system?
Case Study Why do we use the hexadecimal system?
The reason programmers need to understand the binary system is clear: computers represent all data using binary. However, when programmers need to speak to computers, giving instructions in binary would be incredibly time consuming. Imagine trying to write an essay, but for every letter you wanted to write, you needed to write down a binary code that is 8 digits long! Even a short essay would be multiple pages long.
Instead of writing in binary, programmers have taught computers to understand the hexadecimal system. This works incredibly well, since any byte of data (a binary number made up of 8 bits) can be represented using exactly 2 hexadecimal digits. In mathematical terms, 28 = 162. As a result, a large binary number like 11110001 can be written as F1 in hexadecimal.
For example, if you wanted to tell a computer to show you a specific colour, you need to tell it how much red, green and blue there is in the colour. To show a light pink colour in binary, you would tell the computer that the colour is equal to 11110010 10011110 10110001. In hexadecimal, the colour is equal to F2 9E B1. If you wanted to show the colour white, the binary would be 11111111 11111111 11111111 or FF FF FF in hexadecimal.
CONVERTING FROM HEXADECIMAL TO DECIMAL
To convert a number from hexadecimal to decimal, you need to know what the place value of each digit is. Since there are 16 unique numbers in the hexadecimal system, the place value of each new digit in a hexadecimal number increases by 16. The place value of the first digit is thus 1 (160), while the place value of the second digit is 16 (161), and the place value of the third digit is 256 (162).
Table 2.4: The place value of hexadecimal digits
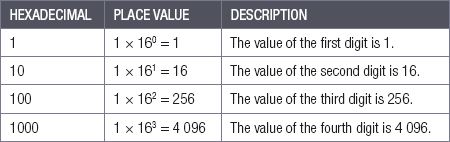
To find the decimal value of a hexadecimal number, we multiply each digit by their position/place value and add all the values together.

Take note
Don’t get confused between decimal numbers and hexadecimal numbers. Even though they look the same, 2216 in hexadecimal and 22 in decimal do not have the same value. Note the base indicator subscript 16

Take note
A = 10 in the hexadecimal numbering system. Refer to the hexadecimal table.
For example, to find the value of the hexadecimal number 3A16:
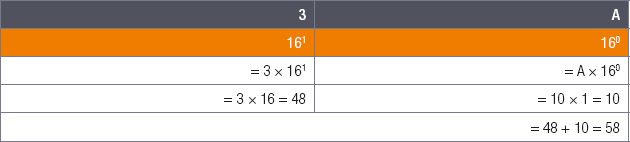
To make sure you understand how to convert from hexadecimal to decimal, work through the following examples:
Example 2.7
Convert the hexadecimal number 65 to a decimal number:
1.Since both digits in the hexadecimal number are less than 10 (6 and 5), we know what their values are.
2.All that is left to do is thus multiplying the two digits with their positional values (16 and 1, respectively) and adding the values together:
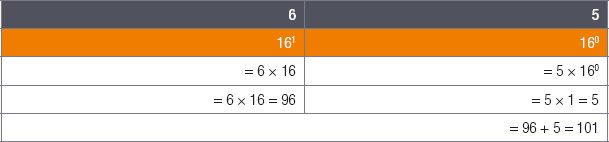
The hexadecimal number 6516 is thus equal to the decimal number 101.
Example 2.8
Convert the hexadecimal number F916 to a decimal number.
1.To convert the hexadecimal number F916 to a decimal number, you first need to find the value of F as a decimal number.
2.According to the table showing the 16 hexadecimal numbers, F is equal to 15.
3.Now that we know the value of F, we can multiply the two hexadecimal digits by their position values and add them together:
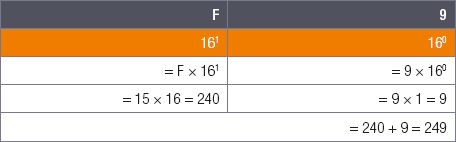
The hexadecimal number F916 is thus equal to the decimal number 249.
Example 2.9
Convert the hexadecimal number 2BC16 to a decimal number.
1.In this example, there are three hexadecimal digits.
2.According to the previous table, the decimal values of 2, B and C are 2, 11 and 12, respectively.
3.Their position values are 256, 16 and 1.
4.Multiplying the hexadecimal digits by their position values, you find:
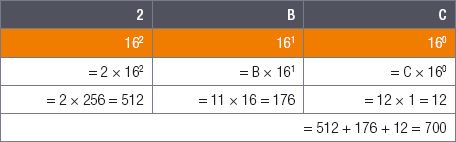
The hexadecimal number 2BC16 is thus equal to the decimal number 700.
CONVERTING FROM DECIMAL TO HEXADECIMAL
To convert a decimal number into a hexadecimal number, you can use the following steps:
Step 1: Find the largest power of 16 that is smaller than or equal to the decimal number.
Step 2: Divide the decimal number by this power.
Step 3: Write down the answer of the division underneath the power. If the answer is larger than 9, write it down using the appropriate hexadecimal digit.
Step 4: Rewrite the decimal number in terms of the division and its remainder.
Step 5: Repeat this process with the remainder until there is no remainder left.
Step 6: Write down 0 under all the powers that were not used.
For example, to convert 94 into hexadecimal, you can start by writing down the factors of 16:

The largest power of 16 that is smaller than 94 is 16. Since 94 ÷ 16 = 5 with a remainder of 14, you can write a 5 under 16, and rewrite the decimal in terms of the division and remainder.

The largest power of 16 that is smaller than 14 is 1. Since 14 ÷ 1 = 14, and 14 is larger than 9, you need to look at the hexadecimal table to find the hexadecimal value that is equal to 14. This is E. You can thus write down E under the 1 in the table and rewrite the decimal number in terms of the division.

Since there is no remainder left, you know that the decimal number 94 can be written as 5E16 in hexadecimal.
Example 2.10
Convert the decimal number 37 to a hexadecimal number.
Step 1: The largest power of 16 that is smaller than 37 is 16, and 37 ÷ 16 = 2 with a remainder of 5.
Step 2: The largest power of 16 that is smaller than 5 is 1, so 5 ÷ 1 = 5 with no remainder.
Step 3: The decimal number 37 is therefore equal to 2516 in hexadecimal.

Example 2.11
Convert the decimal number 222 to a hexadecimal number.
Step 1: 16 is the largest power of 16 that is smaller than 222.
Step 2: Since 222 ÷ 16 = 13 with a remainder of 14, you first need to convert 13 to a hexadecimal digit before writing it into the table.
Step 3: Once this is done, the next largest power of 16 is 1: 14 ÷ 1 = 14 with no remainder.
Step 4: Converting 14 to hexadecimal, you will find that it is equal to E.
Step 5: Therefore, the decimal 222 is equal to DE16 in hexadecimal.

Example 2.12
Convert the decimal number 2 060 to a hexadecimal number.
Step 1: The largest power of 16 smaller than 2 060 is 256, therefore, 2 060 ÷ 256 = 8 with a remainder of 12.
Step 2: Since 16 is larger than 12, you should write a 0 under the 16 in the table.
Step 3: The largest power of 16 that is smaller than 12 is therefore 1, so: 12 ÷ 1 = 12 with no remainder.
Step 4: Since 12 is equal to C in hexadecimal, the decimal 2 060 is equal to 80C16 in hexadecimal.

 Activity 2.3
Activity 2.3
Complete the following activities on your own, then work with a partner to verify your answers. If your answers differ, try to find out where the mistake occurred and correct it.
2.3.5Convert the following hexadecimal numbers to decimal numbers:
a.DB16
b.29C16
c.4816
d.F016
e.C9F16
f.8A16
g.5516
h.7316
i.10116
j.AC216
2.3.6Convert the following decimal numbers to hexadecimal numbers:
a.15
b.16
c.81
d.49
e.172
f.252
g.391
h.77
i.200
j.3751
2.3.7Convert the following hexadecimal numbers to binary numbers, and binary numbers to hexadecimal numbers:
a.1716
b.A2C16
c.001100112
d.100000102
Hint: First convert the numbers to decimal and then to the appropriate number.
UNIT
2.3 Digital character and primitive data types
In 1963, the American Standards Association published a table that linked 127 different letters and symbols to numbers. The table is known as the American Standard Code for Information Interchange (or ASCII) table.

New words
ASCII – American Standard Code for Information Interchange. The ASCII originally used seven bits to encode each character; the modern version uses 8 bits that assign numeric values to letters, digits, punctuation marks, and other characters
In the previous unit, you observed how computers could represent numbers using binary systems. But what about letters? Fortunately, no mathematics is required to convert numbers into letters.
If a computer knows that the information stored in a byte is a letter rather than a number, it can simply search for the character assigned to that number in the table and display the character, with ASCII, the first 32 characters in the table are programming characters that cannot be shown on the screen. These include characters like a carriage return character (which shows where a new line should start) and a horizontal tab character (which adds some horizontal space).
The ASCII value 65 is equal to the uppercase character ‘A’ whereas the ASCII value 122 is the lowercase character ‘z’. ASCII has a limitation of 128 characters.
Universal Code Character Set (Unicode) was created to unify all the encoding schemes so that confusion between computers could be limited as much as possible.
Unicode Transformation 8-bits (UTF-8) is another format to take a value and represent it as a character.
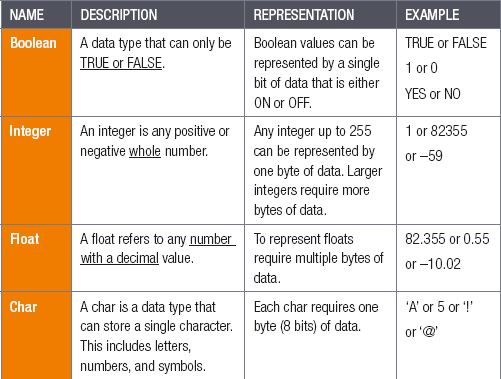
PRIMITIVE DATA TYPES AND THEIR STORAGE
The primitive data types used when programming are described in the table below.
Table 2.5: The primitive data type
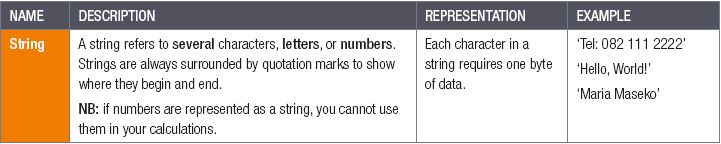
ADDITIONAL DATA TYPES
 Activity 2.4
Activity 2.4
2.4.1Boolean refers to:
a.A data type that can only be TRUE or FALSE.
b.Any positive or negative whole number.
c.A data type that can store a single character.
2.4.2A float is represented by:
a.A single bit of data
b.One byte of data
c.Multiple bytes of data
2.4.3Which data types refer to several characters, letters, or numbers?
a.Char
b.String
c.Float
2.4.4Which of the following is an example of a Char?
a.‘!’
b.True/False
c.‘Hello World!’
2.4.5The terms ‘information’ and ‘data’ are often used in IT. Which description best fits these terms?
a.Information is understood by non-technological people, on the other hand ASCII code is data that can only be read and understood by IT professionals.
b.Information is the result of data that has been processed into something that is meaningful.
c.Data is the result of information supplied by the user.
d.Data and information are the same; it only depends on the device that it is created for.
2.4.6Write down the data type that would be used to store each of the following items:
a.‘1’
b.FALSE
c.‘Perhaps’
d.85
e.75,299
f.‘43,0’
g.‘True’
h.‘a’
i.0,851
j.4951327
2.4.7Write down the correct primitive data type for each item described:
a.The average of the marks that a class of 21 learners obtained in a test.
b.The answer to the question: Do you like chocolates?
c.The millilitres of milk required in a cake recipe.
d.A cell phone number.
e.The price of oil per litre.
f.The name of your pet dog.
g.The number of eggs in a tray.
2.4.8Research and write your own name and your partner’s name using the ASCII value and binary. Once complete, compare your answer with your partner’s answer, and fix any mistakes.
UNIT
2.4 File management
In this unit, you will learn about the requirements needed for a computer to store and organise data.
Computers store data for a number of reasons. The data:
- contains the instructions that a computer uses to function and run applications
- is loaded into memory, RAM, that the computer is currently using in its applications
- storage allows users to keep information that they would like to access on the computer (be it short-term or long-term).
Two structures are commonly used to store data. These are databases and files.
DATABASES AND FILES
The manner in which data is represented on the computer can be seen as a hierarchy. In this unit, we will discuss databases and files.
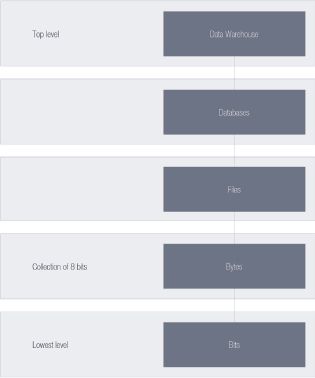
Data is saved in memory while in use by an application. Information needed for later access is stored in a database or file. These are saved on the more permanent storage devices.
WINDOWS REGISTRY (HIERARCHICAL DATABASE)
Anybody who has ever used a computer to create something – an image, a spreadsheet, a text document – has saved their data as a file on their local hard drive. Each file type has its own unique data structure that records all the information in a format only the software can understand. FAT, or the file allocation table, is a database that keeps track of every file on your hard disk.
The Registry is a hierarchical database that stores low-level settings for the operating system and for applications. The Registry is used to store much of the information and settings for software programs, hardware devices, user preferences, operating system configurations, and much more.
A Database is a collection of organised data that can be accessed electronically and is designed for rapid search and retrieval by a computer. Databases are structured to facilitate the storage, retrieval, modification, and deletion of data in conjunction with various data-processing operations.
FILES
On a computing device it is common for data to be grouped into files and folders, with each file being a single collection of data. A document stored on your computer is an example of a file. For example, in the ‘My documents’ folder on your computer, a number of files (of many different types) are saved. The operating system can save data on all of the available storage devices connected to the computer. These storage devices are called drives. On each drive, files are grouped in separate containers called folders.
It is important to place files in folders and label (name) them accordingly. When a file is created, it is saved on a storage device. It remains on the device until the user decides to remove it. Files will remain on the storage device after the computer is turned off, or the storage device is removed from the computer.
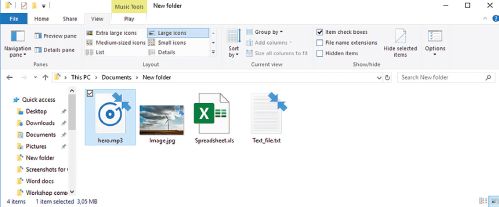
In the next section, you will learn more about how files work and how they can be organised on a computer.
COMPUTER FILE MANAGEMENT
ORGANISING FILES
Files are stored on a computing device in folders or directories. These folders are used to help organise the computer’s files so that they can be easy to search and locate. Each folder can contain either files or different subfolders each containing files.
Figure 2.5 shows a music folder containing music files created by a user.
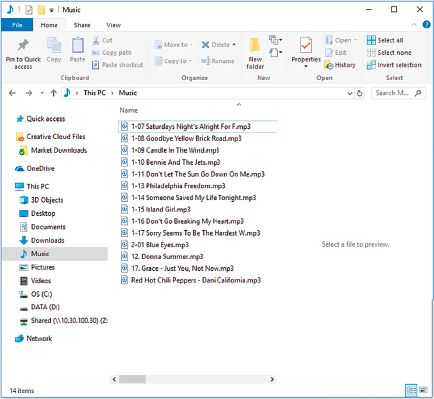
Figure 2.6 shows a more organised way of storing files. A user might have a music folder as the first folder, and then sub-folders for each artist.
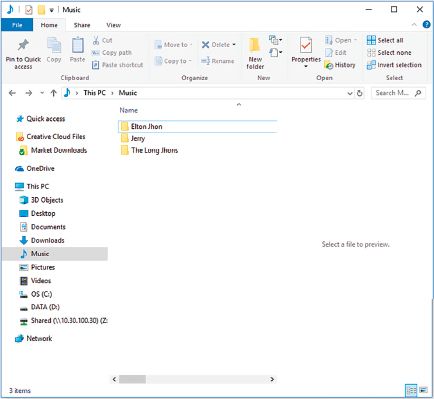
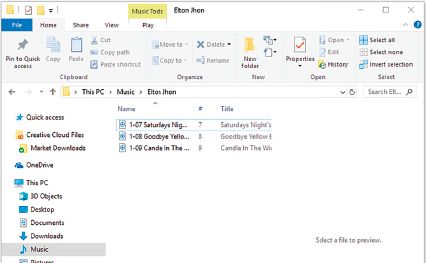
FILES, FOLDERS, AND DRIVES
A similar strategy can be used on all storage devices to make it easier to find important files and folders.
FILE SPECIFICATIONS
The location that a file is saved in is recorded in the file path for that file. This file path tells you on which storage device the file is saved (the drive letter), in which folder and subfolders the file is saved, the name of the file, and finally, the type of file (given by the file extension).
Figure 2.7 below shows an example of a file path.

Each file has a unique file path that starts with the storage device’s drive letter (C: or D: drive). After the drive letter is the name of the file’s folders and subfolders. A backslash (‘\’) is used to separate the drive letter and the different folders and files. Finally, the file path ends with the name and extension of the file (for example, .mp3, .PDF, .JPEG). The extension in these examples consist of a full stop followed by a combination of letters and numbers (you will learn more about this later in this chapter).
You can find the file path of a folder by clicking on the Address bar in File Explorer. To do this:
- open the Computer window from the Start menu
- browse to the folder you want the file path for
- click on the address bar to see the folder’s address.
MANAGING FILES AND FOLDERS
In order to make sure your computer is organised and that you can easily locate the files you are searching for, it is important that you save files in folders and give them useful names. In Microsoft Windows, this can be done in several ways.
The following section will describe the easiest ways in which files can be renamed, deleted, copied or moved between folders.

Take note
The shortcut key to open File Explorer window: Press the Windows key on your keyboard and the letter ‘E’ at the same time.
To see how your computer is currently organised inside Microsoft Windows:
- Press the Windows key on your keyboard.

- Type the word ‘explorer’ and you should see a File Explorer option appear in the start menu.
- Click on the File Explorer option and your computer’s File Explorer should now open.
- Click on the This PC option in the left panel. This will take you to the very lowest folder in your computer’s folder hierarchy. From here, you can explore your computer’s organisational system by browsing through the folder structure.
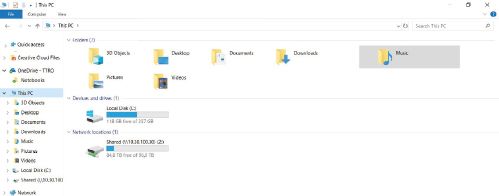
In the screenshot above, there are two storage devices: Computer (C:) and DVD RW Drive (D:). By double-clicking on any of these devices, you can open it and examine the files and folders stored on this device.
Once you are comfortable with exploring your computer, you are now ready to begin organising the files on it.
HIERARCHICAL STRUCTURE: REASONS FOR A FILE STRUCTURE
In the following example, we will explain a directory comparing it to a tree. The structure is the shape of a pyramid, where each row of items is linked to the items beneath it. Because of this pyramidal structure, this hierarchical structure is also known as an inverted tree.
A Windows operating system organises its drives, folders, and files in a hierarchical tree structure. Files are stored on a drive within directories; also known as folders in Microsoft Windows. Folders organise files on a drive so that they can be found more easily. A folder can contain many levels of subfolders.
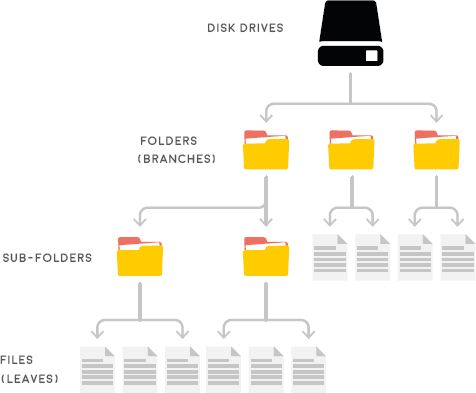
In the diagram above the root of the tree is not at the bottom but at the top, and hanging from the root there will be the drives, folders, sub-folders, and files. The folders linked to the specific drives are the root folders.
Any sub-folders and files found in the folder appear in the next row. This pattern continues until the final row only contains files. All files in a hierarchical tree are known as leaves because they are found at the bottom of the tree, without any rows below them.
The highest level of the tree structure of a drive is the root directory. The root directory of the main drive is usually named the C:drive, written as C:\.
REASONS FOR HAVING A FILE STRUCTURE
A file structure:
- increases efficiency when retrieving files and data
- guarantees high levels of productivity
- helps user to organise data
- helps user to easily identify files
- ensures that related data are organised and grouped together.
MANIPULATING FILES AND FOLDERS
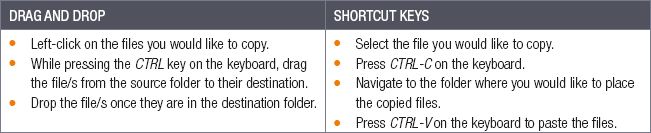
COPYING FILES
When a file is copied, a duplicate of the file is created, it is archived and stored in the computer’s clipboard. This duplicate file can then be placed on any storage device connected to the computer using the paste command. There are numerous ways you can copy and paste files, here are two examples.
Table 2.6: How to copy and paste files
MOVING FILES
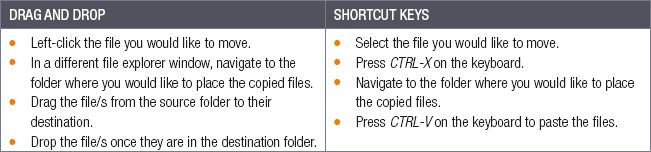
When you move files, the selected files are copied to the new destination and then deleted from their original destination. This means that you have not created a duplicate file, but instead moved a file from one folder to a different folder. To move files, you need to cut and paste them rather than copy and paste them.
Table 2.7: How to move files
RENAMING FILES
This command allows you to change the name of files.
- Left-click on the file you would like to rename
- Using the mouse, click on the name of the selected file
- Enter a new name for your file and press the ENTER key.
When naming files it is important that you choose clear, descriptive names for files. You can use the following tips to make your files easier to find:
- never use a complicated structure
- ensure that you can distinguish between similar files based on the file names
- use the dash symbol to separate different elements in a file name (for example, the name, and date)
- files are usually organised alphabetically, so carefully consider with which letter or number to start a file name.
DELETING FILES
The Delete command allows you to remove files from your storage device. This can be used to remove files you no longer need or to make space on your storage device to store new files.
In Microsoft Windows, all deleted files are first moved to the Recycle Bin. The Recycle Bin is a temporary folder where files are stored, until such time you decide to permanently remove them from your computer. However, files that you delete from flash drives or network drives are permanently deleted and are not moved to the Recycle Bin.

Did you know
Even ‘permanently’ deleted files are not necessarily gone forever. If you have not stored too many new files on the storage device, it is often possible to recover the deleted files using specialised recovery (or un-deleting) software.

RECOVERING DELETED FILES
SEND FILES TO THE RECYCLING BIN
- Left-click on the file you would like to remove.
- Press the DELETE key on the keyboard.
EMPTY THE RECYCLING BIN
- Right click on the Recycle Bin icon and select the ‘Empty’ Recycle Bin option.
- Click on the Yes button to remove the files.
FILE NAMING CONVENTION
Individuals and organisations may decide on a naming convention for their files, for example, Tuckshop January final and Tuckshop Report ver. 2. If used consistently it makes it easier to find the files when needed.
A File Naming Convention (FNC) helps keep the computer clutter-free and allows you to:
- know the contents of a file before you open it
- navigate through long lists of files for the one that you are looking for
- store different versions of the same document by naming them according to date.
GUIDELINES TO DEVELOP GOOD FILE NAMING CONVENTIONS
- Keep file names short but meaningful.
- Include useful information such as the name of the project or document you are working on.
- Include the version number (e.g. V1 or -v1) and the date if there is more than one version.
- Dates should always be in the format yyyy-mm-dd so that the files will be organised in date order.
THINGS TO AVOID WITH FILE NAMING CONVENTIONS
- Symbol characters such as ‘\ / < > | ‘ ? [ ] ; = + & $ a b’
- Abbreviations that are not easy to understand
- Non- specific words such as ‘draft, current or document.’
 Activity 2.5
Activity 2.5
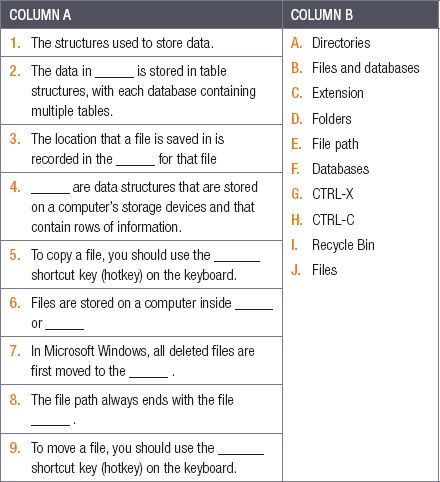
2.5.1Choose a concept from COLUMN B that matches a description in COLUMN A. Write only the letter next to the question number (e.g. 1– A). There can be more than one answer to a question.
2.5.2Rasheed can never find any of the files and folders he is looking for; as a result, he has sent you the incorrect files more than once when working together on group projects. When you had a chance to work on Rasheed’s computer, you realised that most of the files on his computer had never been organised and are simply in the Downloads folder. This included television series and movies, music, games, school projects from the current and previous years, and his programming projects from this year.
To help Rasheed solve this problem, answer the following questions.
a.Suggest a system Rasheed could use to better organise his files.
b.Write down the file paths you would use to organise Rasheed’s files.
c.What drive letter would you use and why?
d.What is the purpose of the backslash (\) in the file path?
e.Explain how to move a file from one folder to another.
2.5.3Complete the following tasks on a computer, using the folder and files given to you.
a.Create a new folder. The folder name should be your name followed by the date.
b.Copy all the files you have received into this folder.
c.Inside your new folder, create a folder called ‘Duplicates’.
d.Look at the pictures you have received and move any duplicated pictures to the ‘Duplicates’ folder.
e.Delete the ‘Duplicates’ folder to the Recycle Bin.
f.Write down how many pictures there are left in your folder.
UNIT
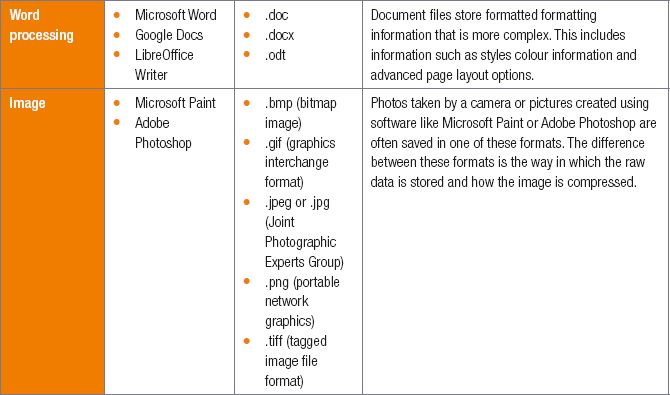
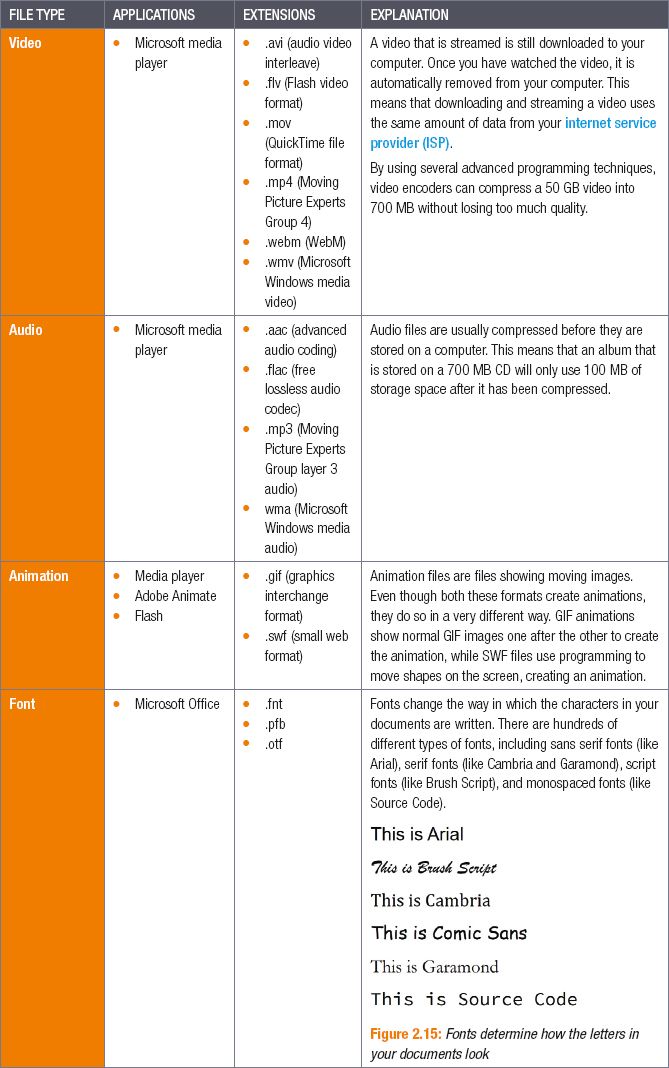
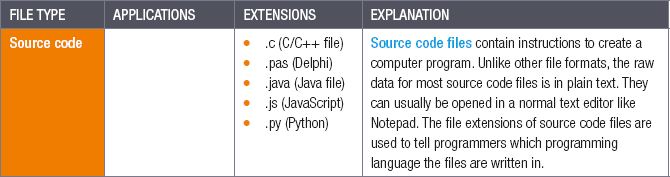
2.5 Common file types and extensions
Files do not only store data, they also contain information on how the data should be interpreted by a computing device. Every file contains a file extension that determines the type of file it is and how the operating system should interpret it.
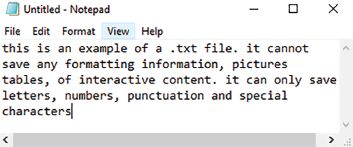
A .text file, for example, is a basic text document that only contains words without any formatting, while the .doc type allows for more complex documents that include different fonts and images.
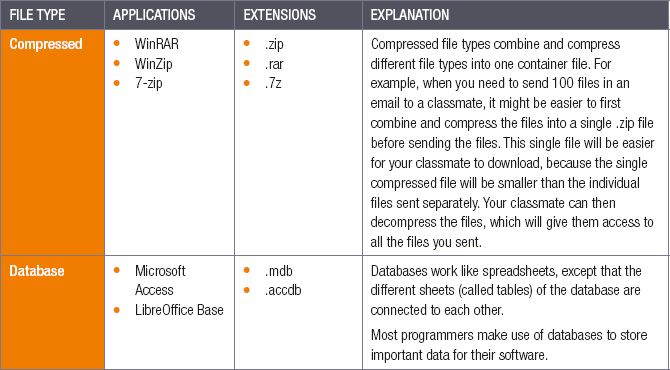
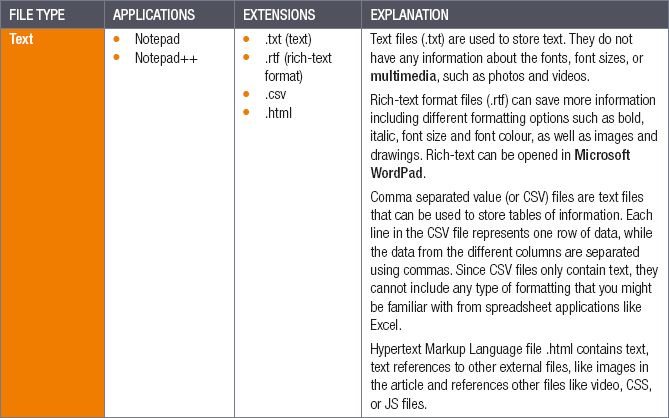
In this unit, we will look at the following types of files:
- compressed
- text
- databases
- spreadsheets
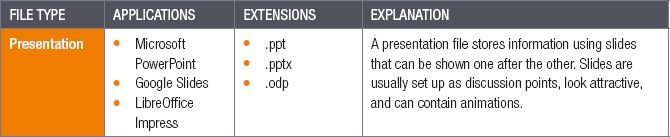
- presentations
- word processing
- images
- videos
- audio
- animations
- fonts
- source code
- object code
- executables
- shared libraries

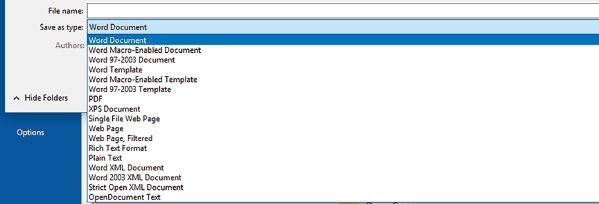
CONVERTING TO RICH TEXT FORMAT


Take note
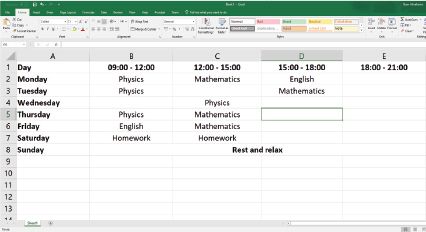
A single spreadsheet file can contain many sheets. Each of these sheets is a separate page that contains its own information. These sheets can be linked to one another, as well as to other spreadsheets.
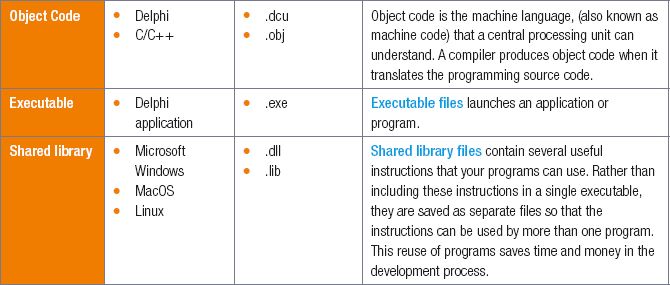
Converting between file types consists of saving the file in a format that can be read by other types of programs. This is often done to share data, access the data with another program or access data with an older version of the software program.
 Activity 2.6
Activity 2.6
2.6.1List five types of image files. Give the name and extension for each file.
2.6.2Give an example of an animation file extension. How does an animation differ from an image?
2.6.3What is a source code file? Give two examples of a source code file type.
2.6.4How are shared library files used?
2.6.5What is the difference between text files and document files?
2.6.6How can CSV files be used to store tabular information?
2.6.7Nosipho has been organising her computer. Unfortunately, after moving some of her files to new folders, she can no longer find them! See if you can help Nosipho by answering the following questions.
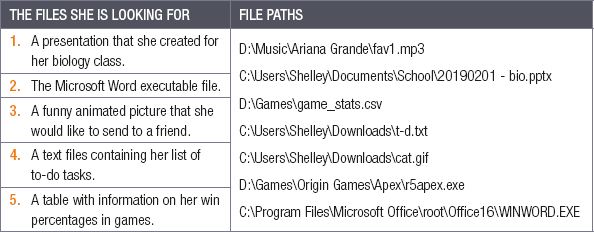
a.Match the files Nosipho is looking for with the file paths.
b.Give the file extension and file type for each of the file paths above.
c.Based on the file paths above, do you think Nosipho has finished organising her computer? Give reasons for your answer.
d.Nosipho used a CSV file to store tabular data. What is the difference between a CSV file and an XLS file?
e.Can you think of any reasons why Nosipho’s games and music would be on her D:\ drive?
f.Why is it not a good idea to change the file extension?
2.6.8Give two advantages of DLL files.
2.6.9Explain the difference between source code and machine code.
2.6.10Describe a situation where you would find it necessary to convert from one file type to another. For example from a Word document to a text file or from a spreadsheet to a CSV file.
UNIT
2.6 Social implications
The introduction of computers in our daily lives has created various issues in our society. These include, legal, ethical, economical and the digital divide issues. In this unit, we will look at each of these social issues. This will include:
- license agreements, copyright, piracy and copyleft
- social, ethical and legal issues on ICT
- economic reasons for using computers
- the digital divide.
SOFTWARE LICENSE AGREEMENTS
When a user pays for proprietary software, they pay the rights to use it while the software still belongs to the developer. When you install proprietary software, you have to agree to terms and conditions in the license agreement. This is an actual agreement and can contain information such as:
- No changes or modifications can be made to the software.
- No copies of the software can be distributed.
- The software can only be installed and used on a specified device.
The license agreement is better as the EULA (end user license agreement) and has three types of agreements:
- Single-user license means that the software is for a single-user/device
- Multi-user license means that the software is for multi-users/multi devices or computers
- Site license means that use of the software is unlimited, however, it is usually installed on a common group of users/devices belonging to an entity, for example, a company, school, etc.
PIRACY
Piracy is the illegal copying, distribution or use of software. These illegal copies are sold at a low price, which is normally a fraction of the price of the original legal copies.
There are different types of software piracy, for example:
- Softlifting: When a software program with a legal license is copied with the main purpose of providing it to multiple users, rather than to sell copies for profit.
- Client-server overuse: When more users than stipulated in the licensing agreement are using a central copy of a program at the same time.
- Hard disk loading happens when illegal copies of software are loaded onto the hard disks of new computers to make the purchase more attractive.
- Counterfeiting is the illegal duplication, distribution, and/or sale of copyright material with the intent of imitating the copyright product.
- Online piracy: When proprietary software is illegally downloaded from the internet.

Did you know
According to the Business Software Alliance (BSA) in South Africa, about 36% of software that is used is pirated. Software piracy causes monetary loss for developers and this makes the legal copies more expensive.
COPYRIGHT
Copyright is the legal right granted to duplicate and make copies of intellectual property. Creators decide on whom and under what circumstances interested users may copy their invention.
For example, if you create a new music album, you can sign a contract with a music label that allows them to copy and sell the album, as long as they pay you for every album they sell. The primary goal of copyright is to give people a reason to create and invent new things, since it allows creators to make money from their creations.
Unfortunately, the internet has complicated questions of copyright. Anyone can copy, for example, music from an album loaded on to the internet to their computer and share it with thousands of people from around the world. This is called copyright infringement or piracy and is a crime in many countries (including South Africa). Unfortunately, this crime is so easy to commit that hundreds of millions of people commit it each year! Piracy is not limited to music either, every day people illegally download, stream or copy television shows, movies, games and software from around the world.
COPYLEFT
Many creators are no longer licensing their creations using copyright. Instead, they are using licenses such as Creative Commons and Copy left to protect their works. These licenses allow other people to copy and use the creation, as long as they follow certain rules. This can include one or more of the following rules:
- Attribution: Whenever the creation is used, you must give credit to the original creator.
- Non-commercial: The creation can be used for any purpose not aimed at making money (that is, non-commercial use).
- Share-alike or copy left: The creation can be used for any purpose, but the new work must be shared with the exact same license as the original work. This ensures that the creation stays free for anyone to use.
- Non-derivative: The creation can be copied and used as it is but cannot be changed in any way.
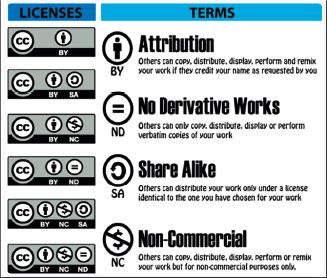
These licenses have become more popular recently, with websites like Wikipedia offering all their information using a Creative Commons license.
SOCIAL, ETHICAL, AND LEGAL ISSUES PERTAINING TO ICTS
There are also difficult ethical questions to answer about piracy:
- Piracy is often seen as theft, but with theft, the original owner loses the item that was stolen. With piracy, however, the original owner still has the item that was pirated, and other people now have it. Is piracy, therefore, the same as theft?
- Since people are supposed to pay for music and movies, many people have argued that piracy steals this money from the creator’s hands. However, if someone never intended to pay for the stolen item or was unable to pay for it, does the creator still lose this money?
- Many studies have shown that rather than decreasing the sales of music and games, piracy can increase the games and music sold, therefore directly helping the creator. How does this affect the ethics of piracy?
- Other studies have found that pirates spend considerably more money on music than normal consumers do. What does this mean for piracy?
- If you believe that people have the right to good and happy lives, then piracy can give billions of people access to high quality entertainment that only the richest people could previously afford, is this not morally or ethically good?
These questions are incredibly complex and difficult to answer. Rather than directly combating piracy and trying to arrest the hundreds of millions of people committing piracy, many companies have realised that providing an easy, fair, and legal alternative to piracy is their best option. Streaming services like Spotify (for music), Netflix (for movies and television series) and YouTube, have allowed creators to make money from their creations while giving people free or affordable access to their sources of entertainment.
PRIVACY
In many countries (including South Africa), people have the right to privacy, which means they can choose what they tell people about themselves. This right becomes incredibly complex because of the use of computers and the internet, computers can record and analyse everything you do. For example, if you use Google to research the rules of netball and then watch YouTube videos about how to play netball, your web browser, and search engine may record this information. Without you telling them, they have now learned that you like netball and might be interested in playing it. This information is very valuable to people who make netball equipment, so Google takes this information (and all the information it records about the billions of people who use their software) and sells it to advertisers. The next time you open a website, you will suddenly see an advertisement for brand new netball balls in your web browser!

WHY THERE’S NO STOPPING PIRACY

INTERNET PIRACY

Did you know
Today, unless you are told differently, it is safe to assume that most websites you visit and internet tools you use will collect some information about you.
With this scenario in mind, try to think about the following ethical questions:
- Should the average person be concerned about privacy?
- By entering your interests on a search engine, do you give a company the right to sell that information?
- By entering your private information on a social network, does that give the company the right to sell your information?
- What about the information entered on a smartphone?
- Should companies be allowed to sell this information if they inform you?
- Is it good or bad that you receive advertisements that match your browser history?
- Would you allow data collection if it allowed complex services (such as Google Maps) to remain free?
These are just some of the many privacy questions that using the internet raises.
 Case Study Google Maps in Germany
Case Study Google Maps in Germany
One of the greatest features of the Google Maps navigation tool is called Street View. It allows you to see 360° photos of most towns or cities, so that you can see exactly what the place you are travelling to will look like. However, for five years, this feature was not available in Germany (one of the world’s most technological countries). Why?

Germany is more concerned with privacy than many other countries in the world. When the Germans heard that Google would be driving through their cities, taking photos of all their houses, many people were outraged. While not technically against the law (the photos are taken from the streets, which are public property), the people felt that Google was invading their privacy. This issue became so serious that, when asked about it, the German Foreign Minister said, ‘I will do all I can to prevent it’.
To solve the problem, Google gave German households the option to have their houses ‘blurred-out’ on Street View, before it was released to the public. Almost 250 000 households decided to do this, which forced Google to blur the houses every time they updated their pictures. In 2011, Google decided to remove the Street View feature from Germany due to the costs of repeatedly blurring the houses. The Street View function was only re-introduced in 2016.

A STREET VIEW OF THE BERLIN WALL

Did you know
Google’s software automatically detects and blurs people’s faces and number plates on Google Street View. This is fortunate for the people who have been caught in compromising positions by the Street View cameras!
FREEDOM OF EXPRESSION
In a famous cartoon from The New Yorker magazine in 1993, one dog is sitting in front of a computer and says to another dog ‘On the Internet, nobody knows you’re a dog.’ This cartoon perfectly captured the way in which the internet allows people to recreate themselves. On the internet, no one knows who you are, so you can be, or say, almost anything.
This can be incredibly empowering for people across the world. It allows people to express their opinions and find communities in which they feel safe. It can even be used to organise a rebellion and eventually overthrow a corrupt government and dictator, as occurred in Egypt in 2011.
Unfortunately, these same freedoms allow people to speak without fear of consequences. This can result in people saying all the hateful, racist, homophobic, and sexist things they normally keep to themselves. It can also result in cyberbullying and it has been directly linked to the suicide of teenagers who experienced severe cyberbullying.

ON THE INTERNET, NOBODY KNOWS YOU’RE A DOG

Did you know
While it is generally considered ethically wrong to make offensive comments, under certain circumstances, it may even be illegal. People from all over the world have been jailed for their comments on social media, including threats and bomb threats, sexual harassment and racist comments. Consider the following questions:
1.Do you think people’s personal details such as names, identity number, address, etc., should be linked to their internet use, or should the internet stay anonymous?
2.If the internet is anonymous, how should racist, sexist, and homophobic messages be treated?
3.How can online bullying (cyber-bullying) be reduced?
4.Are there any situations in which people should be sent to jail for their social media messages?
ECONOMIC REASONS FOR USING COMPUTERS
Computers have offered people many significant advantages, including:
- Saving paper: Previously all documentation was paper-based but with the use of computers, paper has (in most cases) been replaced by electronic versions.
- Labour: The use of computers has increased the production of all goods and many large factories today only need a few workers to manage operations. Unfortunately, it also resulted in unemployment because machines have replaced workers. However, the inclusion of computers in our daily lives has also created many new jobs but at a higher skill level.
- Communications costs: As you learned in Chapter 1, ICT has dramatically changed the way in which people can communicate. Thanks to the ease of electronic communication, it is now possible to sit in Limpopo developing websites for clients from all over the world. This ease of communication has also allowed businesses to expand and open new offices around the world – something that was previously very difficult or expensive. Can you imagine trying to send the newest technical designs or financial statements to your company’s office in a different country before email existed?
- Efficiency: Computers dramatically increased the information available to companies and people, which simplified their jobs and allowed for better decision making.
- Accuracy: One of the advantages of computers is that they increase accuracy for both people and machines. For example, computer-guided equipment can make cuts that are accurate to the nearest nanometre. Similarly, people who are guided by the information on computers can find problems more quickly, make decisions that are more accurate and obtain the training they need to improve their own accuracy.
- Reliability: Thanks to computers, businesses have become more reliable in several ways, this includes, producing products that are more reliable, becoming more responsive to customer complaints and adhering to rules and regulations more stringently. Because of ICT, machines have also become more reliable, with detailed sensors and computers informing maintenance staff whenever a problem is detected. Because of these improvements, consumers can expect higher quality products from companies.

New words
nanometre – one thousand-millionth of a metre
DIGITAL DIVIDE
Digital divide refers to the growing gap between those people with access to and knowledge of using digital technology (“haves”) and those people without access or knowledge to digital technology (“have-nots”). The digital divide is believed to reinforce social inequalities and to cause a persisting information or knowledge gap.
Factors attributing to the digital divide include:
- Education – Households with higher levels of education are increasingly more likely to use computers and the internet.
- Income – Due to lower income levels, disadvantaged neighbourhoods lack the infrastructure available in wealthier areas.
- Location – Households that are in rural areas may have very little access, exposure or need for technology.
 Activity 2.7
Activity 2.7
2.7.1As a young, up-and-coming musician, Bibi has just released his first album. While the album is regularly played on the radio and Bibi often hears taxi drivers playing his music, he has sold very few copies of the album to date. While working in Johannesburg, Bibi sees a street vendor selling a copy of his album for R30. Based on this information, answer the following questions.
a.Why do you think Bibi’s music is played everywhere without any albums being sold?
b.Do you think the street vendor has the legal right to sell Bibi’s album? Give reasons for your answer.
c.What are the possible legal consequences for the street vendor if he is committing copyright infringement?
2.7.2One of the big trends in online computing is called the Internet of Things (or IoT). This refers to the increasing number of appliances and gadgets that are now connecting to the internet, including alarms, fridges, lights, air conditioning, televisions, security cameras, baby monitors, and even doorbells. However, one of the main concerns regarding the Internet of Things is that the data sent and received by these appliances may not be private.
Based on this information, answer the following questions.
a.What is the right to privacy?
b.In your own words, how have computers and the internet affected privacy? Give an example to support your answer.
c.What do you think the advantages are of having security cameras or baby monitors that are connected to the internet?
d.Why do you think people are concerned about privacy about the IoT?
2.7.3In a group, discuss how you feel about the following topics, paying careful attention to the questions posed in the chapter.
a.Copyright and piracy
b.Privacy
c.Freedom of expression
If group members disagree with your opinion, try to find out why they disagree and why they see things differently.
CONSOLIDATION ACTIVITY Chapter 2: Data representation and storage
Answer the following questions by choosing the correct answer for each one.
1.Computers have offered people many significant advantages. Which of the following is not an advantage?
a.saving time
b.automating non-repetitive tasks
c.connecting people
2.Automation refers to …
a.the use of automatic equipment to complete a job.
b.the use of computers to complete a job.
c.increasing economic competition.
3.One of the advantages of computers is that they increase the accuracy for …
a.people
b.machines
c.both people and machines.
4.How has the internet increased economic competition?
a.Shops can now charge more for their products.
b.Buyers must now compete with other buyers for the same product.
c.Consumers can now compare a shop’s prices to other prices.
5.Thanks to computers, businesses have become more reliable. This statement is …
a.True
b.False, because computers are unreliable and often crash.
c.False, because most businesses do not use computers.
6.Thanks to the internet, it is possible for anyone to teach themselves new skills. This includes …
a.creating a website.
b.becoming a plumber.
c.studying medicine.
d.all the above.
7.What is a single switch in a computer known as?
a.Bit
b.Byte
c.Megabyte
d.None of the above
8.Which one of the following is the correct data type that can store a single character? This includes letters, numbers, and symbols.
a.Float
b.Char
c.String
d.Integer
9.Which one of the following is the correct answer when converting the decimal number 921 to hexadecimal?
a.450
b.126
c.399
d.349
10.In the file name: C:\Documents\School\MathsAssignment.docx. What does .docx tell you?
a.File name
b.Folder
c.Extension
d.Drive letter
11.Which ONE of the following options describes the type of devices used to keep an electronic record of work done on a computer?
a.Input
b.Output
c.Processing
d.Storage
12.Ricky grew up in a poor area and his family did not own a personal computer. His parents also did not believe that children or teenagers should have personal phones. As a result, Ricky’s only interaction with computers and the internet was at school. After completing school, Ricky received a bursary to study engineering at University. He moved in to a room at residence and lived on his own. Based on this information, answer the following questions.
a.What is the digital divide?
b.How do you think Ricky’s lack of computer experience and knowledge will affect his studies? Give reasons for your answer.
c.Ricky wants to purchase a computer for his studies. In your opinion, what device do you think he should purchase: a smartphone, a tablet, a desktop, or a notebook? Give at least three reasons for your answer.
d.How do you think access to the internet will help Ricky in his studies?
e.Do you think Ricky has a disadvantage at university compared to students who have more experience with computers and the internet? Motivate your answer.
f.In small groups, discuss the impact or the potential impact of computers on your life and that of your family. You can include improvements that computers have made, improvements that you hope computers will make, problems that you have experienced, or you can simply describe the factors above in relation to yourself.
13.Choose the answer and write TRUE or FALSE next to the question number. Correct the statement if it is FALSE. Change the word(s) in bold print to make the statement TRUE if necessary. (You may not simply use the word ‘NOT’ to change the statement.)
a.Computers use billions of tiny ON and OFF switches called transistors.
b.Å oat refers to several characters, letters, or numbers.
c.Files are data structures that are stored on a computer’s storage devices.
d.A presentation file is a file that stores information in a large table.
d.A single switch (called a byte) can represent the value 1 (when it is switched ON) and 0 (when it is switched OFF).
14.Answer the following questions.
a.What is a float?
b.List TWO reasons why computers store data.
c.What are folders used for?
d.List ONE difference between a bit and a byte.
e.What window should you use to find out what a file’s unique path is?
f.What is a source code file?
g.Give TWO extensions for a source code file.
h.Differentiate between files and folders.
i.Briefly explain how data is stored in a database.
j.Describe what compressed documents are.
k.Give TWO examples of a text file.
l.Draw a diagram to indicate the following folders and sub-folders in a structure (use these names to create folders and subfolders): You have files for school, sports, entertainment (series, music), and personal files.
15.In the figure below, identify the five the different parts of a file path.
D:\Movies\Superheroes\Blackpanther.mp4
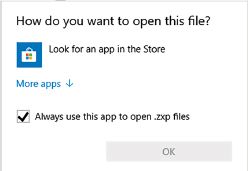
16.You created a document in Word for your father and saved it as ‘benefits.dox’. When he wanted to open it, Windows displayed the following message.
a.Explain the importance of file extensions by referring to the scenario described here.
b.What file extension did you use to save the file?
c.What file extensions should be used to save document files?
d.Why does Windows sometimes ask you how to open the file?
17.Your brother usually downloads movies and music from the internet without paying for them; this can be considered as unethical.
a.Explain the concept, Ethics.
b.What crime is your brother committing?
c.Briefly explain your answer in (b).
d.If your brother copies work from a non-commercial CC licence. What does it mean?
e.Give your brother ONE tip on how to practice ethics when using the internet.
18.In 2017, the People’s Republic of China banned all websites containing images of Winnie-the-Pooh after Chinese internet users compared the Chinese president to Pooh Bear. As a result, Chinese internet users would receive an error message whenever they tried to visit webpages showing Winnie-the-Pooh. Based on this information, answer the following questions:
a.What is freedom of expression?
b.In general, how has the internet given people more freedom of expression?
c.Do you think freedom of expression is important for people?
d.What are some of the disadvantages of freedom of expression on the internet?
e.Do you think governments (like China) should limit freedom of expression on the internet? Give reasons for your answer.
19.Convert the given numbers:
a.1001111002 to decimal.
b.5E816 to binary
c.Convert the decimal number 100 to hexadecimal.
|
Previous
Chapter 1: Basic concepts of computing
|
Table of Contents |
Next
Chapter 3: Basic concepts of hardware
|









