6.3 Use of wireless technology
|
Previous
Chapter 5: Computer management
|
Next
Chapter 7: Social implications
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 6.1 | Mobile/wireless e-communication |
| Unit 6.2 | Use of mobile technology |
| Unit 6.3 | Use of wireless technologies |
| Unvcit 6.4 | Data security |
 Learning outcomes
Learning outcomes
At the end of this chapter you should be able to:
- explain the purpose, writing style and audience for e-communication
- list and describe uses of mobile technology
- describe the uses of wireless technologies
- describe how communication protocols are used to control data
- provide methods of practising data security.
INTRODUCTION
Today, young people from around the world have realised that money can be made if you have a large enough online following.
Many brands are working with internet personalities and influencers to market their products. YouTubers, streamers and social media celebrities are becoming more professional every day, and what used to be something that anyone with a webcam and microphone could do, has suddenly turned into big business.
In this chapter, you will learn more about modern electronic communications, specifically, mobile communications. This will include classic forms of communication like email and SMS, as well as modern forms like vlogging, podcasting and streaming. You will also learn more about mobile devices and the protocols used to transfer data between these devices.

New words
social media – a form of electronic communication through which users create online communities to share information, ideas, personal messages, and other content
influencers – people who have built a reputation for their knowledge and expertise on a particular topic
vlogging – a blog in which the postings are mostly in video form
podcasting – a digital recording of music, news or other media that can be downloaded from the internet to a portable media player
streaming – when a multimedia file can be viewed without being completely downloaded

Did you know
Becoming an online celebrity sounds like a great idea. As a result, there are millions of people around the world hoping to make easy money as a professional gamer or social media celebrity. Only a very, very, very small percentage of these people can survive, much less get rich, from their online income.
ELECTRONIC COMMUNICATIONS IN A NUTSHELL
Electronic communication refers to any data, information, words, photos or symbols that are sent electronically to communicate with one or more people. Thanks to computers and the internet, there are thousands of different ways to communicate today – from uploading videos on YouTube to posting a 140-character tweet on Twitter.
Some of the most popular forms of electronic communication include:
- emails
- websites
- File transfer protocol
- Instant messages
- VOIP
- Video calls
- Vlogs
- Blogs
- Webinars
Whenever you communicate on the internet, whether it is via e-mail, instant messaging or by posting a blog, it is important that you follow proper netiquette. This will not only make the internet a more pleasant place for everyone else, it will also save you from potential embarrassment in the future!
The following are some guidelines you can follow when communicating on the internet:
- Show people on the internet the same respect you would show to them in person.
- Do not say things to people you would not say to them in person.
- Do not post things on the internet that you would not want your mother or future boss to see.
- Things posted on the internet often last forever. This means that things you post as a teenager or young adult can negatively affect the rest of your life.
- Make sure your messages are clearly written and easy to understand.
- When joining an existing conversation, speak about subjects relevant to the topic.
- Try to make useful contributions and help people out on the internet.
- If you need help from the internet, do not expect other people to do all the work for you. Do as much work as you can before asking your question.
- See if there are existing conversations about your topic before starting new conversations.
- Do not spam people! Do not post the same advertisement repeatedly.
While the tips covered in this section are generally good guidelines, it is important to note that netiquette differs from site to site and changes over time. When joining a new website, spend some time figuring out what acceptable behaviour is for that website before sending your own messages.
Activity 6.1 Revision activity
1. Define the followiDefine the following terms:
a. Electronic communication
b. Blog
c. VOIP
2. A friend of yours visits many download sites and starts receiving lots of unwanted mail.
a. What is this unwanted mail called?
b. Is it right to send out mail to people you do not know? Motivate your answer.
3. Study the following words that Jenny usually uses in an email to her colleagues at work.

a. Consider the context of the words she uses in her email messages and list TWO e-mail etiquette (netiquette) rules that have been violated.
b. Which other e-communication medium are these words best used for?
c. Briefly explain to Jenny how she is supposed to send emails to colleagues at work.
UNIT
6.1 Mobile/wireless e-communication
In this unit, you will learn more about different communication methods and how they can be applied using wireless technology. For each technology, you will look at what it is, how it is used, what its advantages and disadvantages are, and a few popular examples of the tool. Let’s start with the most commonly used technology: E-mail.
Email is short for “electronic mail,” and is one of the most popular uses of the Internet. It allows you to send and receive messages containing text, images, or other attachments to and from anyone with an email address, anywhere in the world.
Email allows us to:
- Contact people all over the world for free
- Share files with one or more people at a time
- Communicate with more than one person at a time
- Keep documented evidence of our communication with someone
- Send messages any time of day without disturbing people
- Advertise to multiple people
When typing an email message, it is vital that you use good netiquette. You should always include a subject that summarizes the topic of the email. Begin each message with the recipient’s name and end the message with your name or “signature”.
- communication
- sending files
- marketing
As one of the first internet services, there are millions of different email providers today with most large web services offering a free email service. Some examples common include::
- Gmail
- Yahoo Mail
- Outlook.com
BLOGGING
The first form of one-way conversation is blogging, in which a website creator posts short, informal stories or articles on their website. It is a discussion or informational website published on world wide web consisting of discrete, often informal diary style text entries.
The Audience is generally people who are interested in the content of that specific blog.
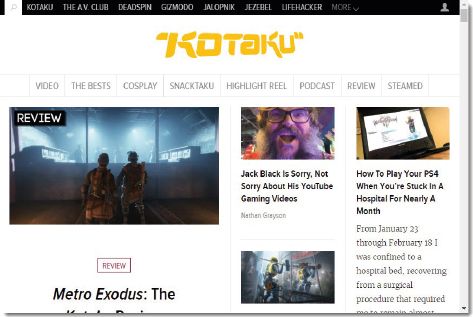
Whenever a new story is posted, it is automatically moved to the top of the website where it will be seen first while all the older stories move down one position. For example, in the screenshot from the blog Kotaku, the newest story is about a professional Magic player, and this is followed by three older stories related to gaming. Clicking on any of these stories will open an informally written article about the topic.
MICROBLOG
Microblogging is a combination of blogging and instant messaging that allows users of social platforms such as Twitter to conveniently create short messages to be posted and shared with an audience online. Microblogs are usually limited to 280 characters, so messages must be short and to the point.
Microblogs come in a variety of content formats including text, images, video, audio, and hyperlinks. They can be seen as short conversations where people can share ideas with their followers.
SMS
The second oldest form of electronic communication is SMS (or short message service). The first SMS was sent in 1992. Since the early 90s, any mobile phone could send a short message (or SMS) to another mobile phone. These messages had a maximum length of 140 characters (including spaces), cost a small amount per message and were asynchronous. This made them an excellent tool for sending small amounts of information to someone or for having short conversations.
Today, SMSs are rarely used for personal communication since instant messaging and social media applications can send the same short messages for free. Instead, the only situations in which SMSs are commonly used are:
- the sender does not know the message receiver
- the sender does not have internet access needed for instant messaging applications
- the sender does not have a phone capable of using instant messaging applications.
- Some banks also use SMSs to notify customers of transactions on their bank accounts.

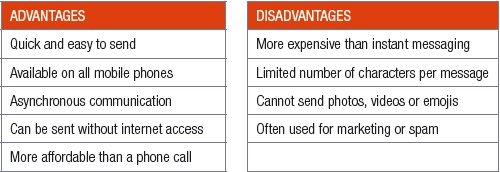
The table below summarises the advantages and disadvantages of SMS.
Table 6.1: Advantages and disadvantages of SMS
The picture in the margin shows a typical example of a spam SMS.

Animation
Animation from Grade 10 showing how a message is converted to data and sent to another person’s phone.

INSTANT MESSAGING
Instant messaging is a service, like SMS, that allows people to send short messages using their mobiles phones (or computers). However, unlike SMSs, instant messages are sent for free over the internet and can contain multimedia items like emojis, pictures, videos and voice recordings. In 2018, the most popular instant messaging applications are WhatsApp, Facebook Messenger and WeChat, although newer instant messaging applications like Snapchat and Telegram have gained many users very quickly.
Together with voice calls, instant messaging is the most popular method for people to have electronic conversations in 2018. It is used to communicate with friends and acquaintances, have group conversations, organise events and share multimedia with people. In fact, it has become so popular that many businesses are using instant messaging applications to communicate directly with customers such as Absa’s ChatBanking and Afrihost’s WhatsApp Assistant.
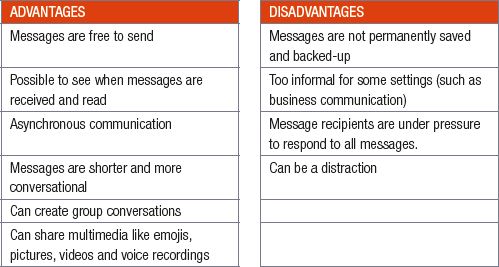
The table below summarises the advantages and disadvantages of instant messaging.

Did you know
In 2017, more than 29 million WhatsApp messages were sent per minute. This is equal to more than 40 billion WhatsApp messages per day!
Table 6.2: Advantages and disadvantages of instant messaging (IM)
The picture in the margin shows a typical example of a WhatsApp conversation.

VIDEOCASTING
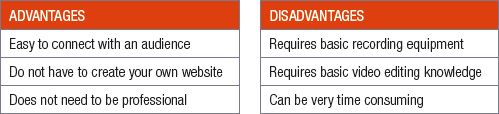
Videocasting refers to a form of communication where videos are broadcast over the internet. Videos can first be created and then uploaded to a website (like YouTube), or they can be streamed live, allowing people to watch the video as it is created. One very popular form of videocasting is vlogging. The word vlogging is a combination of two words: Video and blogging. Vlogging (or a vlog) is like blogging but with videos. As with blogs, vlogs show several informal, conversational videos with the most popular video appearing first. These videos can be on any topic and are generally not professionally made. Most channels you will find on YouTube are examples of vlogs.
The advantages and disadvantages of video casting are shown in the table below.
Table 6.3: Advantages and disadvantages of video casting
PODCASTING
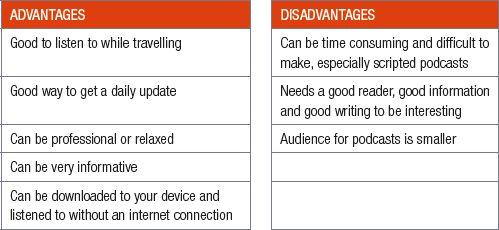
The final type of electronic communication discussed in this chapter is podcasting. Podcasting (or a podcast) refers to an audio only broadcast released on the internet. It is a free service that allows Internet users to download audio files from a podcasting Web site to listen to on their computers or personal digital audio players. As with blogging and vlogging, there are thousands of different types of podcasts, from novels and dramas, to news and talk show podcasts to popular culture and documentary podcasts, which means that there is a podcast for every type of audience.
The advantages and disadvantages of podcasting are listed in the table below.
There is a really common misconception that starndard audio files available on the internet are postcasts. Anyone can just take a recording of themselves or someone on a dictaphone or on their mobile phone and then that audio file can then be uploaded on a website and then most people think that it’s a podcast. One thing that separetes a podcast from simple audio file is the act of allowing subscriptions as soon as you upload an audio file to a podcast hosting site then that podcast hosting website produces a RSS feed and its the fact that the RSS feed allows peolple to subscribe to the podcast. That is what turns into from an audio file to a podcast.
As soon as people start subscribing to that audio file or your CDs of Audio files through RSS feeds, that is what turns it into a Podcast or episodes of a podcast. When you have podcasts that talk about a certain topic then you would have a podcast series.

Did you know
Videocasting is like podcasting, but with videos and audios. While videocasts may be more informative than vlogs, there is significant overlap between the two types of videos.
Table 6.4: Advantages and disadvantages of podcasting
VOICE OVER INTERNET PROTOCOL (VOIP)
VOIP is a service to make telephone calls over the internet rather than through the traditional telephone or cell phone networks. It allows voice and mutimedia data to be transferred across a data network.To use VOIP, the signal from an old, analogue phone system can either be converted to a digital signal or a digital phone system must be installed.
Although VOIP is much cheaper than analogue phones, VOIP systems initially suffered from many technical problems. These days VOIP is widely used and, together with cell phones, has caused the analogue phone system to shrink to a fraction of its original size. As you will see in the next section, VOIP is often combined with video conferencing tools and included in smartphone applications. This gives users the convenience of making a call from their phone, without the cost normally associated with a call.

VIDEO CONFERENCING
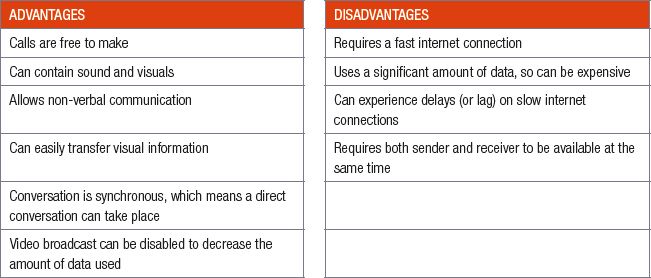
Video conferencing refers to a set of technologies that allow a person to make a video call to one or more people at the same time. These calls are like phone calls but can also include a video broadcast of the people in the call. Popular examples of video call applications include Skype, FaceTime and Discord.
Video calls are mostly used by people who want to have a comfortable conversation. Since more than half of what people say is nonverbal (that is, body language), being able to see the person you are speaking to helps to avoid confusion and misunderstandings.
However, video calls and video conferences also have different uses. For example, video calls are sometimes used to broadcast a live event to people (such as a sporting event, childbirth or home viewing). Video conferences are also often used in business environments, where they allow people from across the world to attend a meeting or view a presentation.
The table below summarises the advantages and disadvantages of video conferences.
Table 6.5: Advantages and disadvantages of video conferencing
 Activity 6.2
Activity 6.2
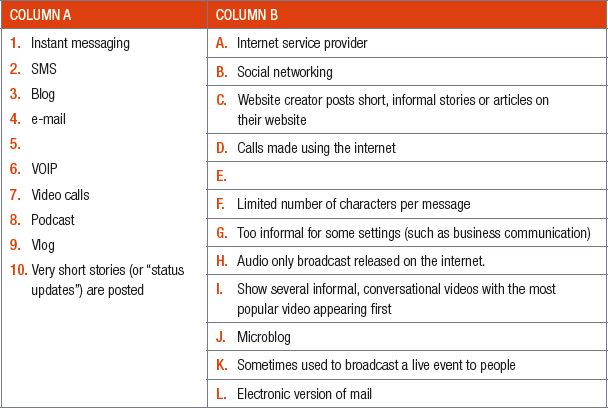
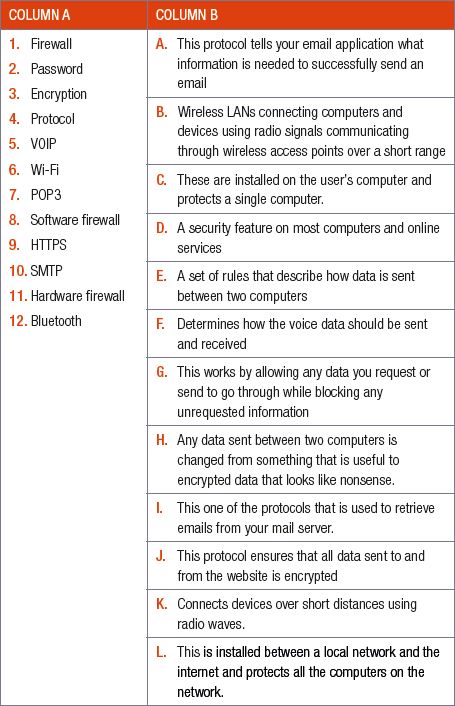
6.2.1 Match the COLUMN A (1.1 – 1.12) with the correct answer in COLUMN B. Write down only the question number and the matching letter in COLUMN B (A – L).
6.2.2 Briefly describe how e-mail is a form of e-communication.
a. List TWO uses e-mails have.
b. List THREE advantages to sending mail over the internet compared to sending it via the postal service.
6.2.3 The second oldest form of electronic communication is SMS (or short message service). The first SMS was sent in 1992. Today, SMSs are rarely used for personal communication.
a. List TWO situations where SMSs are still used.
b. List TWO advantages of SMSs.
c. List TWO disadvantages of SMSs.
6.2.4 Instant messaging is a service, like SMS, that allows people to send short messages using their mobiles phones (or computers).
a. Give THREE advantages of instant messaging.
b. Give TWO disadvantages of instant messaging.
6.2.5 a.What is podcasting?
b. Give ONE difference between podcasting and blogging.
UNIT
6.2 Use of mobile technology
In this unit, you will learn more about the use of mobile technology. The section will look specifically at mobile phones, feature phones and smartphones.
MOBILE PHONES
Mobile phones were designed specifically to make calls and send SMSs. Occasionally, the phones had a few additional features like a calculator or timer, but these features were not as important as the phone’s ability to make calls and send SMSs.

FEATURE PHONES
Feature phones could send multimedia messages, play music, take photos, read emails and browse the internet. While these features are like smartphone features, they differ in two important ways:
- feature phones had a very weak processor, low quality screen and poor camera
- applications had to be designed specifically for each feature phone and there was no App store.
Because of these limitations, feature phones were more like “dumb phones” with a few extra features, while smartphones are more like computers that can run any program designed for the operating system.

SMARTPHONES
A smartphone has advanced features, including a high-resolution touch screen display, WiFiconnectivity, web browsing, software applications and a mobile Operating System.
One of the most important features of a smartphone is its connection to an app store. An app store is a centralized portal where users can search for and download software applications to run on their phones.

MOBILE BROWSERS
One of the biggest advantages of smartphones is that they provide access to high speed internet and the world-wide web. To access the internet through a smartphone, you need to use a mobile browser app such as Chrome (for Android) or Safari (for iOS). Like a web browser on your computer, mobile browsers allow you to visit webpages and browse the internet.
While visiting websites from your smartphone, you may notice that they look slightly different from what you are used to. This is because mobile websites are changed to make them easier to read from a mobile device. In general, mobile web pages differ from their desktop pages in the following ways:
- Mobile phones are smaller, so less information can be shown per screen.
- Mobile phones can be rotated, so pages need to automatically adapt to the width of the screen.
- Mobile phones are slower, so mobile pages can be less interactive.
- Mobile data is expensive, so images and videos are compressed to use less data.
- Mobile phones use touch input (which is less accurate), so interactive elements need to be larger and easier to click.
The purposes of these apps range from productivity and navigation to entertainment, sports, fitness, and communication. Social media is one of the most popular fields of mobile app development.

Did you know
A mobile application, most commonly referred to as an app, is a type of software designed to run on a mobile device, such as a smartphone or tablet. Mobile applications provide users with features similar to those installed on computers. Apps are generally small, individual software units with limited function. A mobile application is also known as a web app, online app, iPhone app or smartphone app.
MOBILE DEVICES
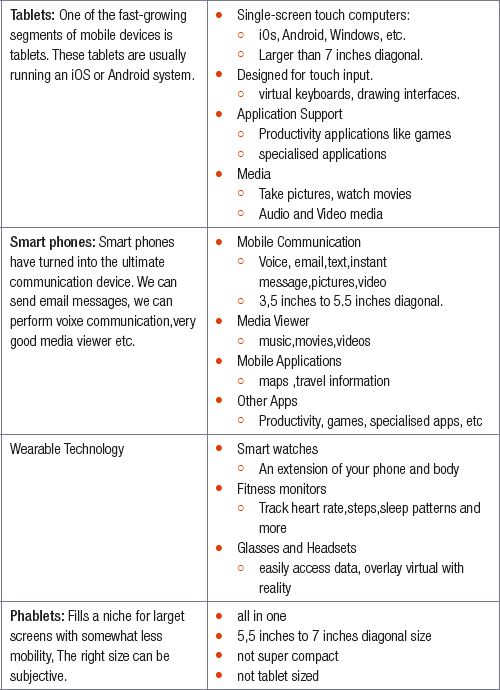
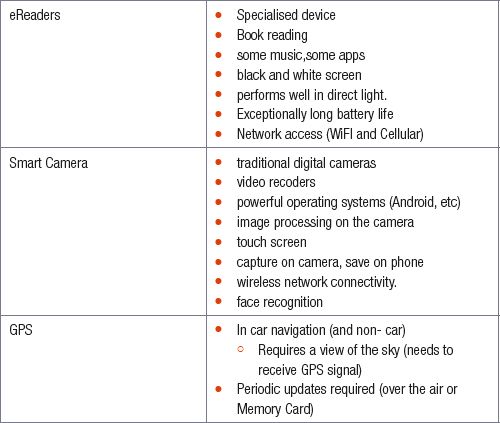
 Activity 6.3
Activity 6.3
6.3.1 Give ONE word/term for each of the following descriptions:
a. This type of mobile technology was small, affordable and had a battery life that could last for weeks.
b. This type of phone could send multimedia messages, play music, take photos, read emails and browse the internet.
c. This type of mobile technology can do the tasks most desktop computers can do.
d. This allows you to visit web pages and access the internet.
e. This is a service to make telephone calls over the internet rather than through the traditional telephone or cell phone networks.
6.3.2 Give ONE difference between a cell phone and a feature phone.
6.3.3 You have also decided to use a smartphone and a web browser to conduct business in the shop that you own.
a. Discuss TWO main hardware differences between a smartphone and a conventional phone.
b. List THREE commonly used smartphone operating systems.
c. Give TWO advantages of using a smartphone in your business.
d. Define a web browser.
e. Explain TWO differences between web pages on a desktop and mobile web pages.
f. Describe ONE type of threat you could be exposed to when using a smartphone.
UNIT
6.3 Use of wireless technologies
In this unit, you will learn more about the different wireless network technologies, as well as a few of the most common protocols used to send and receive data over these wireless networks.
WIRELESS TECHNOLOGIES
- Access points: a networking hardware device that allows other Wi-Fi devices to connect to a wired network
- Difference in range and bandwidth: range refers to the measurement of how far data or a signal can be transmitted and received, while bandwidth refers to how much data you can send through the network
- Connection speed (shaping and throttling): refers to the speed that data is transferred between a device and the internet. Throttling occurs when your ISP intentionally slows down your internet speed, while shaping is the lowering of available bandwidth by your ISP once you have exceeded your monthly limit
- Blockchain: refers to a growing list of records, called blocks, that are linked using cryptography.
Wireless networks do not require cables or wires. Instead, wireless network connections send data across a specific wireless frequency. They form wireless local-area networks (WLANs).
Wireless access points (WAPs) are networking devices that allow Wi-Fidevices to connect to a wired network. An access point acts as a central transmitter and receiver of wireless radio signals. If you use a tablet or laptop to get online, you are going through an access point, either hardware or built in, to access the internet without connecting to it using a cable. Due to differences in the wireless frequencies, range, bandwidth as well as technological differences, different wireless technologies have different uses. For example, bandwidth throttling is an intentional slowing of available bandwidth, lowering of the “speed” that’s typically available over an internet connection. Bandwidth throttling can happen at various places between your device (like your computer or smartphone) and the website or service that you’re using over the internet. Another example is Internet shaping, this is the lowering of available bandwidth by the Internet Service Provider (ISP) to a customer when that customer has exceeded their monthly limit.
The table below summarises the most commonly used wireless network technologies:
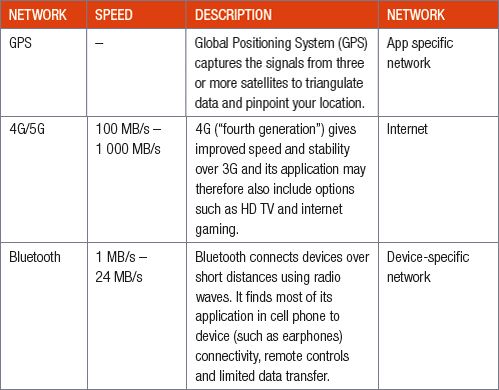
Another type of network is blockchain, see the image below:
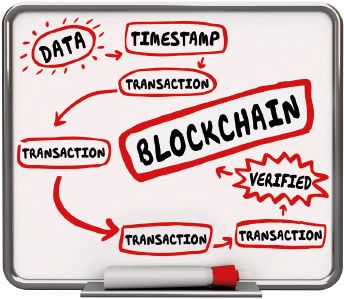
By the end of 2018, 99% of all people in South Africa live in areas with access to 3G and more than 90% of people live in areas with access to 4G.
PROTOCOLS
In Grade 10 you learned that a protocol is a set of rules that describe how data is sent between two computers. For two computers to understand the information that is being sent between them, they need to use the same protocol. This tells the computer that is sending the data how to package the data while also telling the computer that receives the data how to understand and interpret the data it receives.

New words
protocol – a set of rules that describe how data is sent between two computers
To see how protocols are used, you can look at four different protocols: POP3, SMTP, IMAP and VoIP.
- POP3: POP3 (Post Office Protocol version 3) is one of the protocols that is used to retrieve emails from your mail server. POP3 tells your email application how to communicate with this server, find out if any emails were sent to your address and download the emails to your computer.

QR CODE
- SMTP: SMTP (short for Simple Mail Transfer Protocol) is a protocol that is used to send emails. This means that the SMTP protocol tells your email application what information is needed to successfully send an email. This includes your own email address, the email address you are sending the message to, and the message itself. Once you send an email, SMTP makes sure that the email is sent to the correct mail server on the internet where it waits for the email recipient to download their emails.
- IMAP: IMAP allows you to access your email messages wherever you are if you have data or wireless connection to the Internet. IMAP allows you to access, organise, read and sort your email messages without having to download them first, so it is very fast and efficient.
- VoIP: VoIP (or Voice over Internet Protocol) is a protocol that is used to make voice calls over the internet. With VoIP, a phone call is made from a VoIP-enabled telephone or computer. This call is connected to a VoIP service provider, who then connects you to either another VoIP user or to a traditional telephone. Popular services like WhatsApp voice calls and Skype make use of VoIP to allow you to make voice calls to other WhatsApp or Skype users for free.
As these examples show, the different network protocols determine how computers communicate with each other over the internet. Other popular network protocols include HTTP and HTTPS (which determines how web pages are viewed), FTP (which allows files to be transferred over the internet), and IMAP (which also allows emails to be downloaded).
 Activity 6.4
Activity 6.4
6.4.1 Indicate whether the following statements are TRUE or FALSE. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word ‘NOT’ to change the statement.)
a. SMTP is the protocol used to receive emails.
b. Services like WhatsApp or Skype use VoIP to allow users to make free voice calls to other WhatsApp or Skype users.
c. SMTP stands for Short Message Transfer Protocol and is used to send emails.
d. POP3 is the only protocol that can be used to receive email messages.
e. HTTP and HTTPS are used to transfer files over the internet.
6.4.2 You have decided to place 3G connectivity instead of ADSL connectivity in your living room. A wireless router will be used to connect all your mobile devices and computers to the internet
a. What is wireless technology?
b. 3G/LTE connectivity is becoming popular in many homes. Explain what 3G is.
c. What type of network category does 3G fall in?
d. List ONE advantage 4G/LTE has over 3G.
e. What medium of data transmission is used in 3G/LTE?
6.4.3 Protocols are necessary to enable transmission across a network or the Internet. Briefly describe where each of the following will be used.
a. VOIP
b. POP3
UNIT
6.4 Data security
To keep users’ computers and data safe, computers include several security features. In this unit, you will learn about three safety and security features, namely:
PASSWORDS
The first security feature on most computers and online services is a password. By adding a password to a computer, only people who know the password can access the computer and its files.. If you create a secure password that you do not share with other people, you should be the only person who is able to access your computer.
For online services, anyone from anywhere in the world can try to login to your account, the only thing stopping them is your password. To make sure your password is as secure as possible, you should use the following guidelines:
- Choose a password that is long (at least 8 characters).
- Include uppercase and lowercase letters, as well as numbers, in your password.
- Never use personal information such as a birthdate or the name of your favourite sports team as a password.
- Create different passwords for different websites. In this way, if someone hacks your social media account, they cannot use the same password for your online banking.
- Do not share your passwords with other people and do not write your passwords down.

QR CODE
ENCRYPTION
The final security tool used on computers is encryption. With encryption, any data sent between two computers is changed from something that is useful to encrypted data that is difficult to decrypt and use by unauthorised people. The only way to turn the encrypted data back into useful data is to know the encryption key, which is only known by the receiving computer.
Today, most websites use the HTTPS (HyperText Transfer Protocol Secure) protocol which ensures that all data sent to and from the website is encrypted. Most online services today also encrypt personal user information in their databases, which means that, even if a hacker gets access to the database, they cannot just read all the user’s usernames and passwords.
MULTI-LAYER VERIFICATION
Multi-layer authentication is an authentication method, much like a password, in which a computer user is granted access only after successfully giving two or more pieces of evidence to an authentication mechanism:
- knowledge (something the user and only the user knows) e.g. your ID number or mother’s middle name
- possession (something the user and only the user has) e.g. accept verification on another device
- and inherence (something the user and only the user is) e.g. voice or fingerprint verification
 Activity 6.5
Activity 6.5
6.5.1 Match the COLUMN A (1.1 – 1.12) with the correct answer in COLUMN B. Write down only the question number and the matching letter in COLUMN B (A – L).
6.5.2 A password is used to protect your computer from others accessing it. Answer the following questions regarding security of a computer.
a. Explain how using a password for online services can protect you.
b. List THREE ways to make your password secure.
c. What is encryption?
d. What do most websites use to enable encryption?
CONSOLIDATION ACTIVITY Chapter 6: Electronic communications
1. Choose the correct answer.
a. Which one of the following best describes a blog?
A. A website creator posts short, informal stories or articles on their website
B. A website where the creator posts informal video stories on their website
C. A website where the creator posts photos on their website
D. None of the above
b. Which one of the following is NOT an advantage of a podcast.
A. Can be very informative
B. Conversation is synchronous, which means a direct conversation can take place
C. Can be professional or relaxed
D. Good way to get a daily update
2. Match the COLUMN A with the correct answer in COLUMN B. Write down only the question number (1.1 –1.10) and the matching letter (A–L) in COLUMN B, for example 1.11 K.

3. Define electronic communication.
4. What is email used for?
5. List TWO netiquette rules that you should apply when sending an email.
6. What is blogging? List TWO disadvantages of blogging.
7. Give TWO differences between a smartphone and a feature phone.
8. An important part of a network is a firewall.
A. What is a firewall?
B. Name TWO ways that a firewall protects your computer.
C. Briefly explain how a firewall works.
9. Your uncle is considering publicising his business on the internet and has heard that he can use either a microblog or a vlog service.
a. Differentiate between a microblog AND a vlog service
b. Provide an example of a microblog AND a vlog service.
10. Briefly explain what encryption is.
11. Give an example of how a bank uses encryption.
12. List TWO advantages of vlogging.
13. List TWO disadvantages of video conferencing.
14. To be able to buy tickets for transport online, a user must complete the online form shown below.
When purchasing tickets online, users need to provide personal information.
a. State TWO precautions to prevent identity theft, which could take place during this process.
The following error message appears when the ‘Confirm Registration’ button is clicked:
b. Suggest TWO ways to ensure that a password is strong.
15. Your brother knows that one of the biggest advantages of smartphones is that they provide access to high speed internet and the world-wide web.
a. List TWO disadvantages of smartphones.
b. Give TWO threats your brother’s phone can be exposed to.
c. Discuss THREE ways mobile web pages differ from their desktop pages.

|
Previous
Chapter 5: Computer management
|
Table of Contents |
Next
Chapter 7: Social implications
|



