7.4 Computer crimes
|
Previous
Chapter 6: Software
|
Next
Chapter 8: Internet services technologies
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 7.1 | Computer criminals: hackers, crackers, cyber gangs, virus authors |
| Unit 7.2 | Types of cyber crimes |
| Unit 7.3 | Effects of cyber crimes |
| Unit 7.4 | Computer crimes: hardware, software, Information, Identity theft, bandwidth theft, theft of time and services |
| Unit 7.5 | Safeguards against computer crimes, threats and criminals |
 Learning outcomes
Learning outcomes
At the end of this chapter you should be able to:
- discuss different types of computer criminals and cyber crimes.
- protect yourself from online threats
INTRODUCTION
With the increased use of computers and technology, it is Important to be aware of safety and security when online. This chapter will discuss computer criminals and cybercrimes and safeguards against computer crimes, threats and criminals.
UNIT
7.1 Computer criminals
You have already learned how to keep your computer safe from malicious software. You have also seen the techniques websites use to help keep you safe. So, in this final section on computer security, you will look at the different types of computer criminals and the targets of their attacks in greater detail.

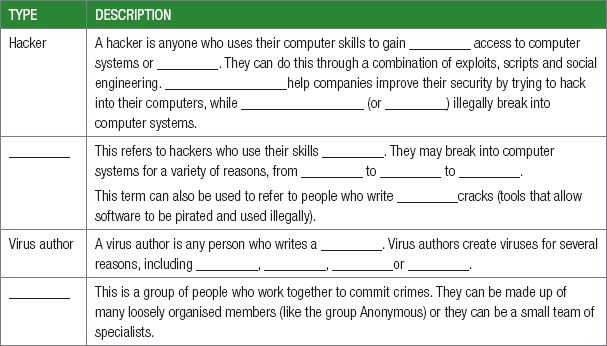
HACKERS
A hacker is anyone who uses their computer skills to gain unauthorised access to computer systems or data. They can do this through a combination of exploits, scripts and social engineering.
TYPES OF HACKERS
White hat hackers help companies improve their security by trying to hack into their computers.
Black hat hackers illegally break into computer systems.
CRACKERS
Cracker refers to Individuals who use their skills illegally. They may break into computer systems for a variety of reasons, from stealing data to testing their skills to making political statements.
The word cracker can also be used to refer to people who write software cracks (tools that allow software to be pirated and used illegally).
CER GANGS
A cyber gang, much like a gang in real life, is a group of people who work together to commit computer crimes. Just like in real life gangs, these gangs can be made up of many loosely organised members.
VIRUS AUTHOR
A virus author is any person who writes a computer virus. Virus authors create viruses for several reasons, including causing damage, showing off their skills, gaining information or money or taking over computers and using them to send spam emails.
Many security experts will argue that calling a hacker a criminal is also incorrect since many hackers do not use their computer skills for illegal purposes but are instead paid by companies to test their security systems.
UNIT
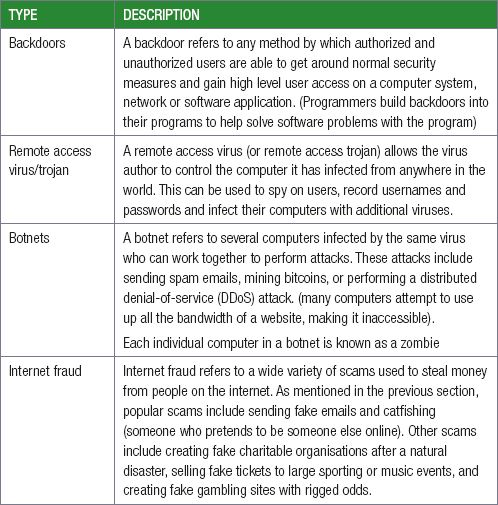
7.2 Types of cyber crimes
In Grade 10 and 11 you learned about different types of computer viruses and malware attacks. The table below describes five new types of attacks that you should be aware of:
 Activity 7.1
Activity 7.1
7.1.1In small groups discuss the types of crimes, the criminals’ reasons for committing the crimes and the consequences.
7.1.2Choose one type of cybercrime and research a case study on the crime. Ask your peers questions on the case study in order to gain further knowledge.
UNIT
7.3 Effects of cyber crime
Cybercrimes can have long lasting effects on the people targeted by it.

Cyber crime is being committed every day. Thieves commit cyber crimes to steal people’s money and their identity. With your identity, the cyber criminal:
can take out loans, incur credit, accumulate debt and, then flee without a trace. It can take years to rehabilitate your identity. A virus can destroy someone’s files and a lost database can result in receiving unwanted sales calls.
The list below includes some of the most immediate effects:
- lost money due to online theft
- expenses incurred to fix problems and prevent future cybercrimes
- loss of reputation due to personal information that is revealed
- corrupted files due to viruses
- long-term debt created resulting in poor credit rating due to online identity theft
 Activity 7.2
Activity 7.2
Revisit the case study and questions that you discussed in your small group about a type of cybercrime. After reading this information, revise your answers and share them with the class.
UNIT
7.4 Computer crimes
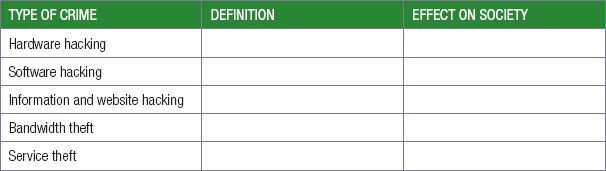
Just like you have different types of cyber criminals, you also have different targets with different goals. In the following section, you will learn about the following types of targets:
- Hardware hacking
- Software hacking
- Information and website hacking
- Bandwidth theft
- Service theft
HARDWARE HACKING
Hardware hacking refers to attacks aimed at specific pieces of hardware. The goal of these attacks is to unlock the hardware in order to give the owner access to features that are normally locked.
SOFTWARE HACKING
Software hacking Is achieved by finding software exploits and breaking software protection
When finding software exploits, hackers look for weaknesses in an application’s security. These exploits are used to gain unauthorised access to the software itself, or gain remote access to the computer.
When breaking software protection, the goal of hackers is to remove the protection which ensures that the software was purchased and is used legally. This allows people to play pirated games or use pirated software.
WEBSITE AND INFORMATION HACKING
Hacking a website is ilegally getting the password to add, edit, delete data stored in that website. After hacking, the hacker will insert harmful programs by inserting malicious codes into the website.
Website and information hacking is used for several different reasons:
- Steal users’ personal (email addresses, passwords, credit card information, information) for identity theft
- Build a database of common usernames and passwords
- Deface the website or place political messages on the website
- Reroute traffic from the website to a phishing website
IDENTITY THEFT
Identity theft happens when a criminal gains access to your personal information and uses that information to gain some benefit. This can include taking out loans in your name, taking control of your existing bank or service accounts, creating a phone number in your name, or using your name to commit other illegal activities.
BANDWIDTH THEFT
Bandwidth theft, occurs when someone links to a file on your website or server from their website. This video will use your bandwidth for all users viewing the video.
SERVICE THEFT
Service theft occurs on the Internet whenever someone illegally uses a username and password to access an online service.
INTERNET RELATED FRAUD SCHEMES
Internet fraud is the use of Internet services or software to defraud victims or to otherwise take advantage of them. Some examples of Internet related fraud schemes are: business fraud, credit card fraud, fraudulent investment schemes, non-delivery of merchandise etc.
INTERNET ATTACKS (WORMS, MALWARE, DENIAL OF SERVICE, BACK DOORS)
An attack targeting an enterprise’s use of cyberspace for the purpose of disrupting or maliciously controlling a computing environment or destroying the integrity of the data or stealing controlled information. Some types of Internet attacks are: worms, malware, denial-of-service (DoS) attacks, Phishing, back doors, drive by attacks, SQL injection attacks, and so on.
PHISHING
Phishing is an attempt by cybercriminals to obtain sensitive information (usernames, passwords and credit card details) by posing as legitimate institutions, usually via an electronic communication.
UNAUTHORISED REMOTE CONTROL AND ADMINISTRATION, FOR EXAMPLE, BOTNETS, ZOMBIES
Remote administration refers to any method of controlling a computer from a remote location. Bot programs allow attackers to remotely control vulnerable computers and form virtual networks of zombies – botnets.
RIGHT TO ACCESS VS RIGHT TO PRIVACY, MISUSE OF PERSONAL INFORMATION
Individuals and coporate have the right to know where the data originated, the right to have inaccurate data rectified, a right of recourse in the event of unlawful processing and the right to withhold permission to use data in some circumstances. For example, individuals will have the right to opt-out free of charge from being sent direct marketing material, without providing any specific reason.
Online services require users to provide personal information in order to use their service. Personal information may include your full name, address, phone numbers, date of birth, email address, username and password and banking details. Although personal information is used responsibly online by many businesses for legitimate communication, it is not always the case and some personal information can be misused by criminals (used to commit fraud and identity theft).
 Activity 7.3 Cybercrime targets
Activity 7.3 Cybercrime targets
7.3.1Choose the correct answer.
a.Any person who writes a computer virus is called a _____
A.Hacker
B.Cracker
C.Virus author
D.Cyber gang or hacker group
b.Anyone who uses their computer skills to gain unauthorised access to computer systems or data.
A.Hacker
B.Cracker
C.Virus author
D.Cyber gang or hacker group
c.They may break into computer systems for a variety of reasons, from stealing data to testing their skills to making political statements.
A.Hacker
B.Cracker
C.Virus author
D.Cyber gang or hacker group
d.A group of people who work together to commit crimes
A.Hacker
B.Cracker
C.Virus author
D.Cyber gang or hacker group
e.This virus allows the virus author to control the computer it has infected from anywhere in the world.
A.Backdoors
B.Remote control
C.Botnets
D.Internet fraud
f.It refers to a wide variety of scams used to steal money from people on the Internet.
A.Backdoors
B.Remote control
C.Botnets
D.Internet fraud
g.It refers to several computers infected by the same virus who can work together to perform attacks.
A.Backdoors
B.Remote control
C.Botnets
D.Internet fraud
h.A secret entrance that computer programmers build into their programs
A.Backdoors
B.Remote control
C.Botnets
D.Internet fraud
i.This type of hacking is used to steal users’ personal information for identity fraud.
A.Hardware hacking
B.Software hacking
C.Information and website hacking
D.Bandwidth theft
E.Service theft
j.When one website uses the images stored on and hosted by another website.
A.Hardware hacking
B.Software hacking
C.Information and website hacking
D.Bandwidth theft
E.Service theft
k.This occurs when employees spend their time not doing work but instead browse Facebook or watch videos on YouTube.
A.Hardware hacking
B.Software hacking
C.Information and website hacking
D.Bandwidth theft
E.Service theft
l.When someone illegally uses a username and password to access an online service.
A.Hardware hacking
B.Software hacking
C.Information and website hacking
D.Bandwidth theft
E.Service theft
m.When finding software exploits, hackers look for weaknesses in an application’s security.
A.Hardware hacking
B.Software hacking
C.Information and website hacking
D.Bandwidth theft
E.Service theft
7.3.2One of the most famous hacking groups in the world is Anonymous. According to Anonymous, they are a hacktivist group which means that they hack websites and organisations for political reasons. Since the start of 2010, their attacks have included:
- Organisations responsible for stopping online piracy like the RIAA, the MPAA and the Copyright Alliance.
- Government websites in countries where they disagree with the government (such as Tunisia and Thailand).
- Organisations and churches accused of homophobia.
- The website and Twitter account of the racist organisation the Ku Klux Klan.
- South African websites owned by the Gupta family (including the websites of ANN7, The New Age and Sahara).
With this information in mind, answer the following questions.
a.List and describe four different types of computer criminals.
b.Which type of criminal is anonymous?
c.Anonymous often uses botnets and remote control in their attacks. Describe what these terms mean.
d.According to the scenario, what is the target of Anonymous’ attacks. Give examples to support your answer.
e.While Anonymous usually targets large organisations that they disagree with, it is most often individuals who are hurt by cybercrime. What are the most immediate effects of cybercrime?
7.3.3Has your online security improved since the start of Grade 10? Are you using a secure password?
7.3.4How many people, on average, do you think use a secure password?
7.3.5Do you think the average Internet user should worry about online security?
7.3.6Do you think South Africans are likely to be the victims of online scams?
UNIT
7.5 Safeguards against computer crimes, threats and criminals
Cyber/Computer crime cannot be stopped completely. But sometimes it can be prevented with practicing good online safety habits. Several methods can be used to safeguard against computer crimes, threats and criminals.
- Make sure your security software is current – and update it regularly for protection from malware, viruses and other online threats.
- Lock or log off your computer when you step away to ensure that no one else will have access to all your information.
- Go offline when you don’t need an internet connection to reduce the chances of hackers and virus scans Invading your computer.
- Take advantage of security settings by using PINs or passcodes to protect someone from easily accessing all your information.
- Consider sharing less online. Your birthdate and the city where you live on your social media profiles can give criminals a more complete picture and make it easier for them to steal your identity.
- Think twice about using public Wi-Fi. Avoid entering private information and using apps that have passwords when you are on public Wi-Fi.
- Delete tweets, posts and online advertising, in addition to emails, if it looks suspicious.
CONSOLIDATION ACTIVITY Chapter 7: Social implications
1.Without looking at your notes, complete the sentences on the different type of computer criminals.
2.Complete the table on the types of cybercrimes.
Which type of crime do you think is the worst and why?
3.Explain three safeguards you can put in place to protect your device. Do you follow these safeguards? Explain.
|
Previous
Chapter 6: Software
|
Table of Contents |
Next
Chapter 8: Internet services technologies
|

