5.2 Threats
|
Previous
Chapter 4: Social implications
|
Next
Chapter 6: Electronic communications
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
 Learning outcomes
Learning outcomes
At the end of this chapter you should be able to:
- discuss computer management issues regarding safeguarding against threats
- provide remedies for safety and security issues.
INTRODUCTION
When talking about computer criminals, it is easy to call all computer criminals hackers. This is an oversimplification, with the word hacker referring to a specific type of computer criminal who uses his or her computer skills to gain unauthorised access to data. In fact, many security experts will argue that calling a hacker a criminal is also incorrect since many hackers do not use their computer skills for illegal purposes but are instead paid by companies to test their security systems. Hackers can also use their skills to expose or prevent criminal activities. This Chapter will look at the various cybercrimes and remedies for safety and security.
COMPUTER MANAGEMENT IN A NUTSHELL
In grade 10 we learned that computer users need to understand the basics of malicious software and know how to use computers and the internet safely because it is possible for computer criminals to infect your computer or gain access to your personal details and use them to steal from you.
A cyber gang, much like a gang in real life, is a group of people who work together to commit crimes. Just like in real life gangs, these gangs can be made up of many loosely organised members (like the group Anonymous) or they can be a small team of specialists.
UNIT
5.1 Safety and security
In this unit, you will learn more about the different computer threats and how to best protect yourself from them. Where Grade 10 looked mostly at digital computer threats, this unit will look at computer threats more broadly, including problems caused by human error, hardware failure, physical computer threats (such as theft), and finally digital computer threats (such as viruses and malware).
For each threat, you will learn what the threat is and how you can prevent it from affecting you.
HUMAN ERROR
The biggest threat to your computer and your data is always you!
Common errors made by people include:
- Giving sensitive information to the wrong people
- Writing down your passwords
- Using the same password for all your accounts
- Choosing an insecure password
- Clicking on links provided in emails without first verifying them.
Another common error made by humans is capturing incorrect information. This is more commonly called GIGO, which stands for “Garbage In, Garbage Out”. According to GIGO, if you capture inaccurate, unreliable or nonsense information on your computer then you can expect any program that uses this information to provide you with inaccurate, unreliable or nonsense information. For example, If you enter someone’s email address or phone number incorrectly then you will not be able to contact that person.
You have got to be aware of accidentally exposing sensitive information due to lack of vigilance or negligence such as leaving your computer logged in or your cellphone unlocked. For example, if you store a scanned copy of your Identity document on an flash drive and then you leave it lying around, a person could gain access to this document and use it to steal your identity.
 Activity 5.1
Activity 5.1
5.1.1 In small groups discuss when you made a human error, the consequences and how you can remedy it in the future.
5.1.2 Explain GIGO and human accidents in your own words.
5.1.3 Design the strongest password activity.
Write a sentence that is easy to remember. This might be a line from a song or movie, a story about a place you have been, or any other phrase you can remember. e.g Avengers
Take the first letter from each word to make your password (including capitalisation).
e.g. AveNgerS
Change the letters to numbers and symbols where possible.
e.g. Av3N93r5
Can also add a symbol on the end for extra length and complexity.
e.g. @v3N93r5!
Now try and make at least 3 diffrent passwords with varried complexity. Try and expore other creative ways to make strongest passphrase.
UNIT
5.2 Threats
PHYSICAL ACCESS
One way in which data can be lost is through theft. This can be the theft of a smartphone, notebook or computer, or simply the theft of an external hard drive or flash disk.
- Do not leave your storage devices unattended in public spaces such as in school computers.
- Make regular backups of your data.
Never store critical information only on a portable storage device.
HARDWARE FAILURE
While most hardware can simply be replaced, losing a storage device means you also lose all the data stored on the device, which could represent the loss of many years of work.
Data loss like this occurs for two reasons:
- mechanical damages of hard drive: There are many moving parts inside hard drives that can break down easily.
- power failures: Sudden changes in voltage may damage hard drives and other parts which are very sensitive to changes in voltage and strong magnetic fields
- spilling coffee, and other water damages: Liquids cause short circuit of important electronic components and they are really hard to recover/repair afterwards.
NETWORK VULNERABILITY
The final threat you will learn about are network-based threats. Since you already know about viruses, spoofing and phishing, this section will look at these types of network threats. The table below describes each of these threats in greater detail.
Table 5.1: Security threats
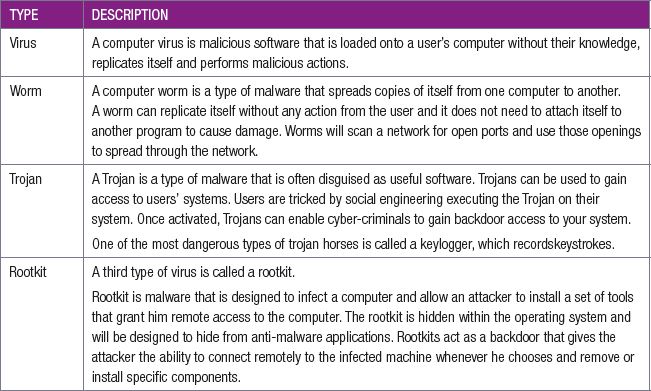

 Activity 5.1
Activity 5.1
5.2.1 In small groups, mind map the three types of threats, their definitions and examples.
5.2.2 For each threat try to list or research remedies.
5.2.3 Match the COLUMN A with the correct answer in COLUMN B. Write down only the question number (1.1 –1.10) and the matching letter (A – H) in COLUMN B in your Theory writing book, for example 1.1 – M.

5.2.4 Study the following phishing example:
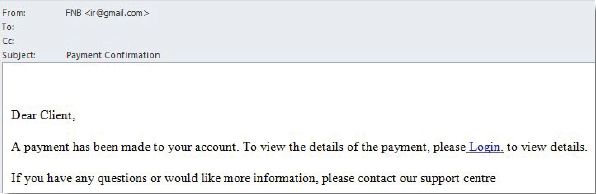
a. Describe TWO features in the e-mail that confirms the e-mail to be a phishing attempt.
b. Explain the main difference between phishing and pharming.
UNIT
5.3 Remedies
For each threat that was discuss in the previous unit we will look at remedies so that your system can be secure.
CREATING A BACKUP
Creating a backup is the process of making copies of your computer’s data to use in the event that the original data or are lost or destroyed.
A backup is a copy of your computer’s data.
TYPES OF BACKUPS
FULL BACKUP
A full backup is when a copy is made of every single file and folder in the system. A full backup takes longer and uses more storage space than other types of backups but restoring data from the backup is faster.
DIFFERENTIAL BACKUP
Differential backups start with a full backup and after that copies those files that have been changed since the full backup took place. So if a full backup was done on Day 1, Day 2s differential will copy all of the files that have changed since Day 1s backup. Day 3s backup will also copy all of the files that have changed since Day 1.
Because a full backup was taken and the differentials copied everything that changed after that, only the full backup and the latest differential need to be restored.
The size of the differential copy increases each time a backup is taken until the next full version is made.
INCREMENTAL BACKUP
Incremental backups also start with a full backup. After that, a copy of the files that have changed since the last backup is made, whether it was a full or incremental copy. If a full backup was done on Day 1, Day 2s incremental will back up all the files that have changed since Day 1. Day 3s incremental backup will only copy those files that have changed since Day 2s incremental backup.
A disadvantage is that when you want to carry out a complete restore, the most recent full backup and all of the subsequent incremental copies must be restored. This can make the restore process a lengthier one than when using a full backup plus the most recent differential copies only.
BACKUP LOCATIONS
Backups can be stored in many different locations. These are discussed below.
LOCAL BACKUP
Local backups are made on a storage medium that is kept in the same location as the original data. It could be on an external hard drive or Network Attached Storage (NAS). Local backups can protect data from hard drive failures, accidental deletion and virus attacks.
OFFSITE BACKUP
When the backup storage media is kept at a different location from the source, this is known as an offsite backup. The backup can be done locally and then the storage medium is moved to another place. Offsite backups provide extra protection from theft, fire and natural disasters.
ONLINE/CLOUD BACKUP
Online backups are done frequently to a storage medium that is always connected to the source being backed up via an internet connection. Many commercial data centres offer this as a subscription service to customers. This offers the same protection as an offsite backup.
UNINTERRUPTIBLE POWER SOURCE (UPS)
An uninterruptible power supply (UPS) is a device that allows a computer to keep running for a short time when power is lost due to a power failure. UPS devices also provide protection from power surges.
A UPS contains a battery that takes over when the device detects a power failure. If a user is working on the computer when the power fails, they have enough time to save what they are working on and shut the computer down before the battery runs out. A UPS will also regulate any power surges so that the power surges do not damage the computer and you do not lose any data when a power failure occurs.
PASSWORDS
The following guidelines will help you to set a strong password. This will stop hackers from finding out your password and using your account illegally:
- Always use at least 8 characters in your password, at least two of which are numeric.
- Use a mixture of both uppercase and lowercase letters
- Includee a mixture of letters and numbers
- Include of at least one special character for example, ! @ # ? % *
- Do not use personal information in your password that someone else is likely to be able to figure out.
- Never use a password that is the same as your account number.
- Do not use passwords that are easy to spot while you’re typing them in. Passwords like 12345, qwerty (i.e., all keys right next to each other), or nnnnnn should be avoided.
ACCESS RIGHTS
This was discussed in the Chapter on Networks. Most networks are set up with ‘access rights’. This means the administrator has created accounts for all users, with the right to access certain files and folders. For instance, you may have a personal folder in which you have the right to open, read, write, create and delete files. This will restrict unauthorised access to certain files and folders.
FIREWALLS AND ANTI-VIRUS
FIREWALL
A firewall is hardware, software or a combination of both, that monitors incoming and outgoing traffic on a network. The firewall decides whether to stop the traffic based on a set of predefined security rules. Its purpose is to create a barrier between an internal network and incoming traffic from external sources to block potentially malicious traffic.
ANTI-VIRUS
Antivirus software is system software designed to prevent, detect and remove malware infections on computing devices.
Antivirus software can protect against a wide variety of threats including keyloggers, Trojan horses, worms, rootkits, spyware and ransomware.
All antivirus programs perform some important tasks:
- Scan specific files for malware or known malicious patterns
- Allow you to schedule scans to automatically run for you
- Allow you to initiate a scan of a particular file or your entire computer, or an external storage device at any time.
- Remove any malicious code that it detects. Depending on the settings, you will be notified of an infection and asked if you want to clean the file, or the program will automatically do this.
VALIDATION
To prevent theft of data and personal details, computer systems must be programmed to validate whether the user that is logging into the computer is an authentic user or not.
 Activity 5.3
Activity 5.3
5.3.1 In small groups, add to your mind map, from the previous activity, the remedies for each threat you identified.
CONSOLIDATION ACTIVITY Chapter 5: Computer management
1. Choose the correct answer.
a. A collection of programs designed to infiltrate a computer and gain the highest level of privileges:
A. Rootkit
B. Trojan horse
C. Worm
D. Virus
b. Attempt from people using an e-mail to try to convince someone to provide security-related information is called ...
A. Phishing
B. Pharming
C. Scamming
D. Snooping
c. Social engineering is associated with
i) Designing social networks
ii) Maintaining social media records for clients
iii) Manipulating individuals to give personal information
A. (i) and (ii) are correct
B. (ii) and (iii) are correct
C. Only (ii) is correct
D. Only (iii) is correct
d. Shop owners are making good use of the Internet and all its services. Viruses are always a problem.
i) List THREE ways in which a user’s actions could result in a virus getting onto their computer system via a network.
e. One of the shop owners has been advised that once he is connected to the internet, his chances of receiving unsolicited mail increases. He also plans to be doing online banking.
i) What is this unsolicited mail called?
ii) Is it possible to stop unsolicited mail from getting into your mailbox? Motivate your answer.
iii) Give THREE measures he can take to protect himself from someone trying to get his banking details.
|
Previous
Chapter 4: Social implications
|
Table of Contents |
Next
Chapter 6: Electronic communications
|

