4.1 The social implications of location-based computing
|
Previous
Chapter 3: Networks
|
Next
Chapter 5: Computer management
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 4.1 | The social implications of location-based computing |
| Unit 4.2 | Ethical and legal issues of network use policies and practices |
| Unit 4.3 | Capabilities and limitations of ICTs |
 Learning outcomes
Learning outcomes
At the end of this chapter you should be able to:
- discuss the social implications of location-based computing
- explain the ethical and legal issues of network use policies and practices
- understand the capabilities and limitations of ICTs.
INTRODUCTION
The introduction of computers in our daily lives has created various issues in our society. These include, legal, ethical, economical issues as well as issues with regard to the digital divide. In this unit, we will be looking at the social issues applicable to all content that we have covered thus far in Term 1.
SOCIAL IMPLICATIONS IN A NUTSHELL
For the first time in history, it is possible for a person to live their entire life without ever leaving home. They can buy everything they need using online shopping services, go to school on the internet, attend an online university or teach themselves how to programme from the internet, find a remote or internet-based job, and even build friendships and relationships on the internet.
In fact, in Japan, so many people (mostly men) have started doing this that they have a name: Hikikomori. According to the Japanese psychiatrist, Tamaki Saito, hikikomori refers to ‘cooping oneself up in one’s own home and not participating in society for six months or longer ...[without] another psychological problem as its principal source.’ A 2010 study found that more than 700 000 people in Japan were living as hikikomori.
Just because it is possible does not mean it is a good idea! Studies have shown that hikikomori tend to be more unhappy, insecure and have fewer friends than the average person. However, it does show how dramatically computers and the internet have changed the world. Computers have become integrated in every part of society, from entertainment to work. Computers have even become integrated with love, with a 2018 study finding that 40% of Americans use online dating and 20% of new long-term relationships start with online dating!
UNIT
4.1 The social implications of location-based computing
Location-based computing (LBC) services are applications that use the position of a device and its user in the provision of a value-added service. Examples of these applications include services such as Tinder, Meetup or Windy, which use the geographic location of their users to provide or augment an activity. These applications monitor a user’s location either willingly or covertly (by others).
Because users often carry their mobile devices with them, location data may be collected everywhere and at any time, often without user interaction. The mobile device may keep track of what a person is doing and their location. It can reveal visits to potentially sensitive destinations, like medical clinics, courts, political rallies, and union meetings.
LBCs introduce a set of challenges from a social perspective. Although these applications have benefits such as an increased sense of community, connectivity and access to information and place knowledge, they bring with them many negatives as well. These negatives are loss of personal privacy, objective access to knowledge, and the application’s influence on our relationship to physical places.
The extent of location information has also increased the risks of stalking and domestic violence because perpetrators are able to use or abuse location-based services to gain access to location information about their victims. LBCs make it easy for predators to locate potential victims, and they give the criminal more than enough information to manipulate their target. Additionally, because an increasing number of minors carry location-enabled cell phones and devices, location privacy will also become a child safety issue.
 Case Study Location-based computing
Case Study Location-based computing
A few years ago, some soldiers posted a picture of helicopters arriving in Iraq on a social network. The geotag attached to the photo gave insurgents the location of where the picture was taken, and they launched a mortar attack that destroyed four of the newly-arrived helicopters.
 Activity 4.1
Activity 4.1
4.1.1Read the below article, then debate the use of location-based computing.
8 realities about location-based apps: Use your common sense before buying into the hype of location-based apps
By IRA WINKLE
The desire to be cool and embrace new technologies definitely overtook the desire to be safe with the very buzzy mobile, location-based apps. You’ve got to love a smartphone app that broadcasts all sorts of information about you - your likes, your age, your job - to everyone within sight who has the same app. Because it reduces friction, right? It makes it easier to meet that good-looking guy or girl right over there who shares your love of kiteboarding and Gorillaz. You can cut down lame conversations about things you have no interest in at all. Cool. Right?
The hype says these apps are all about possibility. But when reality sets in, you start to think about probability. For example, the probability that a certain percentage of the people who look appealing to you when apps like Glancee or Highlight bring them to your attention are going to be, well, creeps - or worse. The probability that apps like these are putting out more information about you than you’re really comfortable with. The probability that your privacy, once compromised, will never be whole again.
I have put together a list of eight things everyone should know about location-based services and social networks in general.
No. 1 - Stalkers and paedophiles will like these apps
Location-based services are a dream for sexual predators and other criminals. They make it easy for predators to locate potential victims, and then they give the criminal more than enough information to manipulate his target.
No. 2 - If it is anywhere on the internet, consider it public
If you think you can put something on the internet, mark it as private, and then not worry about it becoming public, you are wrong. There really is no such thing as private data. Let’s say you post something on a social network. Your privacy settings make you feel confident that the post is going to be seen by no one but your friends. There is really nothing to keep that social network from changing its privacy policy so that such friends-only restrictions just disappear.
No. 3 - Your circle of friends is much bigger than you think
Do you really know all of the people you have friended on Facebook? Many people have hundreds of ‘friends’ on Facebook, and not a few have thousands. That means the friends of your friends could number in the hundreds of thousands.
Considering that you likely are not true friends with your Facebook friends, it’s safe to assume that at least some of them are less than trustworthy. And when you consider ‘friends’ of ‘friends,’ the chances that some are reprobates, sickos or perverts are much larger.
No. 4 - We all make mistakes
You might decide to give these apps a try and just be careful with them. You’ll turn them on only when you are surrounded by friends and actively seeking to contact people. Inevitably, though, because we all make mistakes, you will forget to turn the service off from time to time, or you will set the parameters incorrectly.
No. 5 - People lie
Some lies might be considered harmless enough, but the thing that worries me about location-based social apps is that they can expose you to sociopaths and criminals. A sociopath who wants to meet you would have no qualms about checking out your interests and then going to Facebook to revise his own to bring them in line with yours. Then he’s back in your vicinity with a prof le that Highlight or Glancee is all excited about. Hey, nice to meet you!
No. 6 - Small pieces of information add up
Cisco Systems’ Lance Hayden, who is a part-time faculty member at the University of Texas and a former CIA operative, told me about an exercise he conducts with his students – most of whom tend to have that same idea that they control the information about them on the internet. He asks them to put together an intelligence dossier on themselves, using information available only on public internet sites. Invariably, he said, as soon as the students start their projects, they show up early for the next class to ask him how they can get all of the information about them off of the internet. So who’s in control?
No. 7 - No, you can’t have separate online and offline lives
Another comment from those SXSW attendees was that they protect their lives by having separate personas - one for online one and one for offline. They believe that what they do on social media can be kept completely separate from what they do in the workplace and other venues. Sorry to break it to them, but social network monitoring is a thriving business. Companies use such services to screen potential employees.
Similarly, it’s foolish to believe that you’re protected because you’ve shut down location-based apps. If you have had them turned on, you have sent out information about yourself. If you have a stalker, he could well know where you live and might be waiting for you there.
No. 8 - You can’t predict all the ways these things can work against you
Suppose you go into a car dealership today with your smartphone in your pocket. The salesperson could use Highlight or Glancee to find out your marital status and how many kids you have. He can discover where you work and your job title. He can see whether you have checked in at other dealerships via Foursquare. He might be able to learn that you have asked your Facebook friends for car recommendations. In short, he can arm himself with a lot of information that will be useful in any negotiation. I think I would rather have them just pull my credit report.
The price of ignorance
The interesting thing about that car-buying example is that the advantage seems to go not to the person broadcasting the information, but to the one receiving it. Like so many other things on the internet, these new location-based apps are ‘free’ services. The big problem with location-based services is that they can place you at the whim of anyone who chooses to abuse you. Criminals are early adopters, and they never miss an opening. Is your need to be cool worth the risk of being a crime victim?
[To read the full article: Source: www.computerworld.com/article/2503019/8-realities-about-location-based-apps.html, accessed 13 June 2019]
4.1.2Read the below article about a location-based app that is used to locate missing persons.
How to Locate a Missing Person by Tracking Their Cell Phone
Tracking a cell phone can help to obtain a lost or stolen device, but it can also be used to find a person of interest or someone who is missing. Today there are two primary ways with which traces can be performed.
The first is the most common used by law enforcement and that is a call trace. A call trace functions by waiting for a call to be placed from the phone in question. If someone uses their cell phone to call 911, emergency call centers now have the ability to pinpoint the call within a 25-100 meter radius. Law enforcement authorities are able to use the same technology to ‘ping’ a cell phone and find its position. This is how authorities are able to find children who are victims of kidnappings or those who have run away. However, a different set of circumstances arise when the phone belongs to an adult. In this case, the tracer should expect an array of red tape and jurisdictional issues.
Privacy, consumer protection and wireless protection acts that are put in place disallow any indiscriminate tracing. In certain cases, however, a simple signing of a waiver will allow either the cell phone service provider or the authorities to track the phone in this manner. In other instances it is not so easy. Law enforcement and investigators have to entertain the idea that the person in question wanted to disappear. It is within their rights to do so.
The second way, which is easier and used by non-law enforcement, taps into a phone’s GPS chip or SIM Card. In nearly all cases, the phone in question will need to have a GPS chip already installed before any type of tracking can be accomplished. Many phones on the market today are already sold with this technology. If the phone does not have GPS capabilities, the chip can be bought through a service provider or online. Order according to phone model and install according to the manufacturer’s instructions.
Once a chip has been discovered or installed, the tracking can commence. Software downloaded to a computer can then trace the phone at all times. Many people are not comfortable with having their whereabouts tracked on a daily basis in the off chance that they might get lost or abducted. Still, signals sent from a phone to a tower can aid in finding the person’s location. Overlapping signals work to triangulate the location via global positioning system (GPS) coordinates.
If no access to a constant tracing program is possible. There are companies out like I.C.U. Inc., uLocate.com, and AccuTracking that will charge a fee to perform this type of search for you, but you may want to try using Google Latitude or the My iPhone app (if they have an iPhone) to find them first.
If the cell number you are trying to track is one belonging to a family member that is on a plan with you as the administrator, a new set of options are open to you. There are also services that can be purchased through your service provider to locate devices using certain SIM cards. AT&T offers what they call FamilyMap, and Sprint and Verizon both call their service Family Locator. Both of these come with a monthly fee but can be used to trace the whereabouts of a cell phone.
[Source: http://cellphonenumber.phonebooks.com/tracking-cell-phones.html, accessed on 13June 2019]
a.Think about all the adults and children who are being reported as going missing in South Africa. How do you think an app like this could help police to locate these missing adults and children?
b.Do you think there are any negatives to this app. Think about what could happen if this app was hacked.
UNIT
4.2 Ethical and legal issues of network use policies and practices
Individuals are going to great lengths to locate unsecured wireless access points either for their own benefit or the benefit of others.
 Activity 4.2
Activity 4.2
In a recent case, an individual found an unsecured wireless network at a Lowe’s home improvement store. After documenting the location, he went back with a friend. Together, they hacked into the Lowe’s system with the goal of stealing credit card numbers of the store’s customers. The men were caught after they had managed to get six credit card numbers, but the damage could have been far worse.
When an individual accesses another person’s network and uses their resources without their permission, it can be considered stealing. It is illegal to use someone else’s bandwidth. In addition, the owner can lose their network access if the provider finds any unauthorised actions via their connection, illegal or in excess of allotments.
The use of wireless networks to conduct confidential business is now standard practice. Highly confidential work like legal matters are often done on unsecured networks using mobile devices. Anyone can hack the devices that are connected to an unsecured network and take information from these devices. These networks range from coffee shops to public spaces, such as airports, to home networks that are often not password-protected and can be connected to free Wi-Fi.
With these scenarios in mind, discuss the following questions in small groups.
4.2.1Should the average person be concerned about privacy?
4.2.2By entering your interests on a search engine, do you give a company the right to sell that information?
4.2.3By entering your private information on a social network, does that give the company the right to sell your information?
4.2.4What about the information entered on a smartphone?
4.2.5Should companies be allowed to sell this information if they inform you?
4.2.6Is it good or bad that you receive advertisements that match your browser history?
4.2.7Would you allow data collection if it allowed complex services (such as Google Maps) to remain free?
UNIT
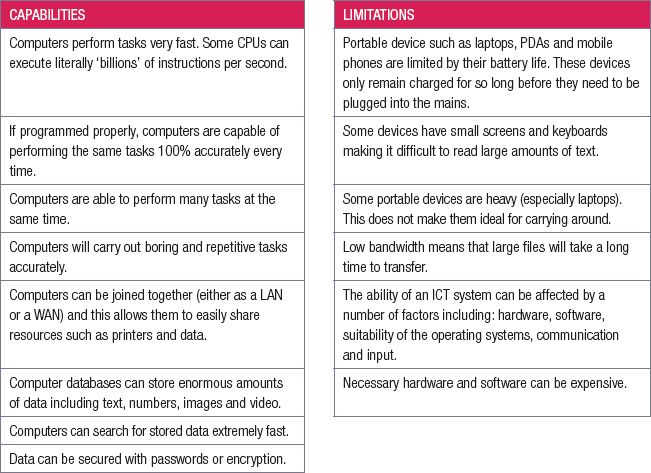
4.3 Capabilities and limitations of ICTs
In the previous chapters we discussed information and communications technology (ICT) and the role it plays in our everyday life. We also discussed some of the limitations of ICT.
Work through the table below to revise the capabilities and limitations of ICTs.
 Activity 4.3
Activity 4.3
For each factor explain why it is a limitation of ICT and how it could affect a business:
- hardware
- software
- suitability of the operating systems
- communication
- input.
CONSOLIDATION ACTIVITY Chapter 4: Social implications
Read the following information about location-based social networking sites and answer the questions that follows for each app.
- Plazes allows its users to create a calendar of what’s going to happen and where it is going to happen in their current area. Users can then notify their friends by hitting the ‘spread it’ button. This is a great way for friends to connect.
- Citysense displays a map of where people are transmitting a cell signal from so you can see where your friends are and get up to date information of local events.
- Whrrl lets friends share reviews, photos, the latest specials, deals, and so on,of restaurants, hotels, bars, clubs, malls, movie theaters with one another. This app uses Google maps so you can specify a location to read reviews of businesses in a particular area and what they all have to offer in order to choose which one is best suited to what you are looking for.
- Brightkite is similar to Twitter and has a Facebook-like friend feed so that users can comment, upload and share pictures on the location of where they are.
- Loopt turns your mobile device into a compass that allows a map to be populated showing the locations of your friends and where they’ve visited. Comments and suggestions are easily left for others to see and the application also has built-in support for instant messaging services.
1.What are the social implications for the location-based app?
2.What ethical and legal issues could happen due to the policies of the app?
3.What is the advantage and disadvantage of the app?
|
Previous
Chapter 3: Networks
|
Table of Contents |
Next
Chapter 5: Computer management
|

