11.1 Computers provide solutions to issues of national and international importance
|
Previous
Chapter 10: E-communications
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 11.1 | Computers provide solutions to issues of national and international importance |
| Unit 11.2 | The evolution of social networking and the effect on society |
| Unit 11.3 | Privacy and information sharing |
 Learning outcomes
Learning outcomes
At the end of this chapter you should be able to:
- explain how distributed computing power and decision making provide solutions to issues of national and international importance
- describe the evolution of social networking (information overload and availability of personal information) and the effect on society
- list and discuss issues regarding privacy and information sharing
INTRODUCTION
Social Implications looks at the effect of computers and ICT on the world, your community and yourself. Before continuing with the rest of the chapter, carefully think about the effect of computers and ICT on your privacy and answer the following questions:
- How can ICT invade your privacy?
- Why do people share their information on Facebook or Instagram, for example?
- What are the benefits of social networking?
- What are the disadvantages to social networking?
SOCIAL IMPLICATIONS IN A NUTSHELL
According to the United Nations, globalisation can be defined as an increase in the rate and ease with which people, companies and governments from different countries interact.
Globalisation has been made possible due to two technologies: transportation and improvements in computers and computer networks.
Globalisation has made the world richer, smarter, more connected and more culturally aware than ever before.
Computers make global communication easy and affordable. This has several advantages, including:
- allowing families to keep in touch, even over large distances.
- helping people to keep and maintain larger social networks.
- increasing people’s social and romantic opportunities.
- improving job opportunities, with many young South Africans finding opportunities overseas.
- helping people understand different points of view, with research showing how communicating with different people can increase empathy.
One communication technology that has already had a significant impact and will continue to grow in popularity as internet speeds increase, is video conferencing. Video conferencing allows two or more people to connect to the same video call. This has significant advantages over a typical phone call or teleconference call, including:
- a large part of communication is through facial expressions and body language
- video conferences allow users to visually show what they are talking about.
The benefits of global communication are not just personal. Companies have their own advantages including:
- selling their products to a global (international) audience.
- managing larger, international businesses using video conferences.
- sending critical documents across the world immediately using email.
- quickly transferring and receiving funds between countries and from international customers through online banking.
ACTIVITY 11.1 Revision Activity
11.1.1List three more advantages of video conferencing.
11.1.2Debate for or against globalisation.
UNIT
11.1 Computers provide solutions to issues of national and international importance
INTRODUCTION
In Grade 11, you saw how computers can be used to solve real world problems. This included specific case studies on the weather, elections and censuses, but also included a more general discussion of new technologies, including Als that can diagnose cancer and create legal briefs and self-driving cars.
In this section, you will look at two new techniques that programmers use to solve problems:
- Distributed computing
- Decision making
DISTRIBUTED COMPUTING POWER
Distributed computing refers to computer projects where hundreds, or even thousands, of computers across the world work together to solve a problem, for example, the free, online game called Phylo.
In this game, players could use coloured blocks to build DNA and were asked to compare DNA sequences between different species. The closer the match, the higher score players would receive.
While the game itself was interesting, it was a distributed computing project. The goal of Phylo was not just to entertain people, but also to help align DNA sequences correctly and to recognise patterns that computers struggle to recognise. By playing the game, the gamers helped researchers to better understand several different diseases.
Similar distributed computing power has been used to:
- Find a solution for the Ebola virus
- Find a solution for certain strains of childhood cancer
- Find new prime numbers
- Categorise galaxies
- Search for alien life
- Fight AIDS

Did you know
GIMPS, or the Great internet Mersenne Prime Search, is a distributed computing project to find large prime numbers. Anyone who runs the software and finds a new, undiscovered prime number receives a cash prize of roughly R50 000. Anyone finding a prime with more than 100 million digits will receive a prize of almost R2 400 000! The largest prime number discovered by 2018 has 23,25 million digits.
By allowing people who care about a topic to pool their resources, the creators of these projects gain access to an incredible amount of resources that they might not have had on their own.
DECISION MAKING
Computers have changed, and is continuing to change, human decision making. For thousands of years, people have seen human intelligence and the ability of humans to make decisions as the primary difference between humans from animals. Over the last 30 years, and especially the last 10 years, humans are giving up more and more of their decision-making responsibility to computers. This ranges from decisions as simple as when to do exercise or which road to take to work, to potentially life changing decisions such as which romantic partners would suit you and what job occupations would suit you.
As computers become more intelligent and learn more about us, they will undoubtedly play an even bigger role in human decision making.
 Activity 11.2 Decision-making
Activity 11.2 Decision-making
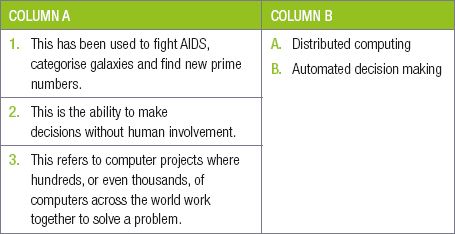
11.1.1Match the COLUMN with the correct answer in COLUMN B. Write down only the question number and the matching letter in COLUMN B in your answer book.
11.1.2This activity can either be a discussion in class or learners can answer the questions individually in their homework books.
a.Do your own research and write a paragraph either agreeing or disagreeing with the statements below:
i.Humans will always be able to make better complex decisions than computers.
ii.Soon, computers will be able to do most jobs, including knowledge jobs such as doctors, lawyers and accountants, better than humans.
iii.Soon, your computer and smartphone will be able to analyse all the information It has recorded about you and your friends and provide you with concrete social suggestions such as “You need to spend more time with Mark” or “You and Relebohile would make an excellent couple.”
iv.The more decisions computers can make; the easier life will be for humans.
v.When you allow computers to make too many decisions, you place too much power in the hands of computer programmers.
UNIT
11.2 The evolution of social networking and the effect on society
INTRODUCTION
Using computers, the internet and social websites have made significant improvements to the world. They have made it easier for people to be more social, made it easier to connect with people who are far away, made communication more affordable, made it easier to find a community of similar people, and allowed people to begin building databases of the world’s knowledge. At the same time, it is important to stay aware of the potential risks and problems linked to these improvements.
INFORMATION OVERLOAD
While social networks do allow people to stay connected to their friends, they can also lead to social media information overload. This occurs when there is too much information available, with new messages, photos and notifications demanding your attention every minute of the day. Rather than spend their time productively, people can spend every free minute they have reading social media posts making them less productive, less able to obtain new information, more stressed and can even cause depression!

If you find yourself spending too much time on social media, you can try the following:
- Limit the time you spend on social networks to five minutes, three times a day
- Do not save your username and password, so that you are forced to enter these each time
- Unfollow or mute people who fill your social media page with useless information
- Disable social media notifications on your phone
- Uninstall or stop using any services that do not improve your life

Animation
Animation showing five techniques to prevent social media overload:
1.Limit time you spend to 5 minutes
2.Do not save username and password
3.Unfollow or mute people
4.Disable notifications on phone
5.Stop using services that do not improve life.

 Activity 11.3 Social media overload
Activity 11.3 Social media overload
This activity can either be a discussion in class or learners can answer the questions individually in their homework books.
11.3.1How you feel about social media overload.
11.3.2What is social media overload?
11.3.3Do you use social networks websites or applications on most days?
11.3.4Do you enjoy using social networks or do you see it as a chore?
11.3.5Do you occasionally feel stressed after using social networks?
11.3.6Do you think, in general, that social networks make people happier?
11.3.7How easy would it be for you to stop using all social networks?
11.3.8What can you do if you find yourself spending too much time on social media? List at least THREE things to do.
AVAILABILITY OF PERSONAL INFORMATION
PERSONAL INFORMATION
Social networks like Facebook and Twitter are a great way to keep in touch with friends and acquaintances. They can also be used to meet new people with common interests and talk about the things you have in common. At the same time, unless you specifically change it, most social networks share a lot of the information that you place on their website publicly. This means that anyone on the internet can see this information.
This can result in uncomfortable family moments when your parents see exactly what you did during the holiday with your friends! It can also have more permanent, long-term consequences, such as costing you a job. In today’s competitive job market, there is a growing trend for employers to look at the social media profiles of applicants before making any hiring decisions
Publicly available online information has also been used to commit crimes. Burglars have used tweets or public photos to see when families are away from home or on vacation. This allowed them to burgle houses at a time they knew the houses would be empty. Stalkers have also used publicly posted information (such as tweets or photos on Instagram) to stalk their victims.
 Case Study Stalking and social media
Case Study Stalking and social media
SEARCH ENGINES AND GROUP COMMUNICATIONS
Consequences of search engines
Every search engine consists of some algorithm that determines how the engine searches the database and shows the results of the search. Web sites hope to make a profit on their business enterprises at some point. If you understand the significant role search engines play in the web surfing behavior of internet users, you can see the value a corporation might place in having its web site be returned as the first and ‘most appropriate’ result of a search engine’s search. ‘Ask google’: results in people having poor recall of knowledge if they knew where answers to questions were easily found.
Consequences of group communications
Many people go through their lives feeling like they do not fit in. They might have different interests or different beliefs from the people around them, or they may feel awkward in social contexts.
One of the big advantages of social websites is that it allows users to find like-minded people who share their interests and beliefs. For many people, the internet is a place where they can show a part of themselves that they feel the need to hide in real life.
The downside of finding like-minded individuals is that it allows people to create a context in which their ideas are never challenged. Today, you can go online and speak with thousands of people who share your beliefs, reinforcing your (incorrect) beliefs.
As a result, rather than using the internet to expand their horizons and encounter new people with new ideas, people often surround themselves with too many similar people, strengthening their existing (and often bad) ideas. This is particularly problematic with racist social network groups where users can surround themselves with people sharing and speaking about their racism, rather than surrounding themselves with people who will challenge these views.
 Case Study Alt-right
Case Study Alt-right
Social, political, environmental
Social
Recent research found that almost a quarter of the world’s population is now on Facebook. Social networks grow more powerful with the increase in interactions among people on social platforms. People can find others like them, with their beliefs through social media. People can also create memes (an image, video, piece of text, etc., typically humorous in nature, that is copied and spread rapidly by Internet users), publications, Virtual online worlds, and so on.
Some people believe that social media encourages people to use mobile devices to express their concerns on social issues without engaging actively with real life campaigns. Their support is limited to pressing the ‘Like’ button or sharing content.
Political
Social networks play an increasingly important role in electoral politics. Social networks are helping to fundamentally rewire human society. Social media lets people freely communicate with one another and they are helping to create influential social organisations among once-marginalised groups.
Environmental
Social media increasingly supports environmental campaigns and connects people on major environmental issues such as climate change. It also provides people with the ability to track the quality of the air and water around them and then share this data with others. Social media has propelled the rise of the independent activist. For example, when Cape Town went through water restrictions, many people shared their personal views and tips on saving water on social media. This brings about an awareness that otherwise might have gone unnoticed.
 Activity 11.4 Social websites
Activity 11.4 Social websites
This activity can either be a discussion in class or learners can answer the questions individually in their homework books.
11.4.1How do you feel about social, political and environmental communities?
11.4.2Do you belong to any of these communities?
11.4.3Do the people in this community share most of your opinions?
11.4.4How likely are you to encounter people with different opinions?
11.4.5Do you think the internet is making it easier or harder to become an activist?
GLOBAL COMMUNITY – CULTURAL EFFECTS
Globalisation allows people from across the world to form part of a global community where everyone can share and enjoy other people’s cultures. For example, most people today watch international movies and listen to international music. There are also many people who are interested in and follow international news.
The risk with the global community is that smaller cultures may disappear. In South Africa, especially among young people who rely on the internet for entertainment, many people rarely watch South African television shows or listen to South African music. Many people are also more interested in international than local affairs, and more interested in international celebrities than local celebrities. This constant focus on international entertainment, news and people can increase the cultural attraction to countries with a large cultural impact (such as the United States) while decreasing the power of smaller cultures.
For many people, culture is an important part of a person’s identity, so losing your own culture, or seeing your culture as second to an international culture attacks that identity.
Groups consisting of people with different cultures can improve the groups’ performance.
If all small cultures are swallowed by larger, more dominant cultures, some unique ideas and perspectives on the world could disappear.
 Activity 11.5 Group communication
Activity 11.5 Group communication
This activity can either be a discussion in class or learners can answer the questions individually in their homework books.
11.5.1How you feel about a global community? Give reasons for your answers where applicable.
11.5.2How does a global community differ from an online community?
11.5.3Are you more likely to follow local or international entertainment?
11.5.4Do you see yourself as a South African citizen or as a citizen of the world?
11.5.5Do you think it is important for countries to protect their local cultures?
11.5.6How do you think smaller countries can protect their local cultures?
11.5.7South Africa is a country with a lot of different cultures. Do you think this makes it easier or harder to maintain our culture?
SOCIAL WEBSITES AND SOCIAL ENGINEERING
A few examples ways In whichh social engineering is practiced include:
- Baiting: This depends on a victim taking the bait, similar to a fish reacting to a worm on a hook. The person dangling the bait wants to entice the target into taking action e.g. unknowingly downloading malware on a server.
- Phishing: This grabs information from an unwitting victim to seek information that might help with a more significant crime.
- Email hacking and contact spamming
- Pretexting: Is a trick to get someone’s attention so the fraudster can trick the would-be victim into providing something of value.
- Quid pro quo: This scam involves an exchange, I give you this, and you give me that. Fraudsters make the victim believe it’s a fair exchange, but that’s far from the case, as the cheat always comes out on top.

New words
Social website - an online platform that allows users to create a public profile and interact with other users on the website
Social engineering - the act of tricking someone into giving information or taking action they usually wouldn’t take
 Activity 11.6 Social websites and social engineering
Activity 11.6 Social websites and social engineering
This activity can either be a discussion in class or learners can answer the questions individually in their homework books.
11.6.1How you feel about social engineering? Give reasons for your answers where applicable.
11.6.2What type of information is the fraudster looking for and why?
11.6.3How can you not fall for social engineering?
WIKIS
Wikis are encyclopaedias that can be edited by anyone. They can be general encyclopaedias (like Wikipedia) which allows users to create entries for any topic, or they can be very specific, such as the esports Wiki called Liquipedia, which only allows users to add information on the esports-related topics.
Because anyone can contribute information to the wiki, these encyclopaedias can grow incredibly quickly. For example, Wikipedia contributors have written and edited more than 27 billion words across 40 million articles! If the average professional author can write 100 000 words in a year, it would have taken a team of 1 000 professional authors 270 years and hundreds of billions of Rand to create an encyclopaedia as large as Wikipedia. Instead, the information on Wikipedia was written and edited in less than 18 years for free!
Since anyone can update a wiki, they are also easier to maintain and keep up to date. Whenever a large event occurs, hundreds of contributors are ready to update the wiki with the newest information.
This does not, however, suggest that wikis are perfect. Instead wikis are faced with several challenges, including:
- Quality of information: Because anyone can edit the information, many people doubt the quality of information stored on wikis. However, several studies have shown the quality of information on Wikipedia is comparable to that of top encyclopaedias written by experts.
- Bias of editors: Since anyone can edit an article, rather than those with a neutral view of the topic, are most likely to edit the pages. This means that there are often edit wars about controversial topics, with one group of editors writing the article so that the information is positive, and another group so that the information is negative.
While these criticisms have mostly looked at Wikipedia, this is because Wikipedia is by far the largest and best moderated wiki. These issues become even more significant on smaller wikis, where a small number of contributors can have a large impact on the quality of the wiki.
 Activity 11.7 Wikis
Activity 11.7 Wikis
This activity can either be a discussion in class or learners can answer the questions individually in their homework books.
11.7.1How do you feel about wikis?
11.7.2What is a Wiki?
11.7.3Do you ever use wikis? Have you used wikis outside of Wikipedia?
11.7.4Do you think people can trust the information they read on Wikipedia?
11.7.5Do you think Wikipedia should be used as a research tool for school projects?
11.7.6Do you think it is a problem that most Wikipedia articles are written by men?
11.7.7Do you think bias on Wikipedia is a significant problem? How can you know if an article is biased?

Did you know
- Non-diverse editors: The bias of the information may not always be intentional. A 2013 study found that 90% of Wikipedia’s editors were men. As a result, the information on Wikipedia may be biased towards men.
- Vandalism: Vandalism occurs when the information on a page is purposely changed to be incorrect or misleading. For example, after South African swimmer Chad Le Clos received a silver medal at the 2016 Olympics, his Wikipedia page was edited to state that he “died at the hands of Michael Phelps, being literally blown out of the water by the greatest American since Abraham Lincoln.”
- Privacy: Privacy concerns have been raised when relatively unknown people receive Wikipedia pages containing personal information about them against their wishes.
UNIT
11.3 Privacy and Information sharing
INTRODUCTION
Privacy is defined as a person’s ability to control how information about them is shared with other people or institutions.
In South Africa, the privacy of all individuals is protected in Section 14 of the constitution. Furthermore, the Protection of Personal Information Act (or POPI Act) ensures that citizens’ personal information (such as ID numbers, addresses and telephone numbers) may only be used in very specific circumstances.
Privacy becomes a very complicated issue on the internet. Companies who provide services to you for free (like Facebook and Google) often collect information about you when you use these services and sell that information to advertisers.

Did you know
If you have ever received a telemarketing call, then you know that one of the companies you pay (like your bank, cellphone provider or satellite television subscription) sold your contact information to a telemarketing company.
These companies do not break the law, but rather make sure they follow the letter of the law exactly. They may include a section on how your personal information will be used in the 30-page terms and conditions agreement you sign when you sign-up for their service, or they may ask you who to share information with any time you make a post. However, by using their services, you allow them to sell your information.
In the following section, you will learn more about issues related to privacy and anonymity. Specifically, you will learn how cookies can be used to invade your privacy and the impact of online anonymity.
COOKIES
This has been explained in detail in Chapter 1. Let’s revise this topic briefly. A cookie is a small amount of data generated by a website and saved by your web browser. Its purpose is to remember information about you, similar to a preference file created by a software application.

QR CODE
ANONYMITY
As you know, most websites allow people to use them anonymously. Even when they require people to create accounts, very few websites require people to prove their identity. As a result, people can create accounts with any name or surname they want. This allows greater freedom of expression, but also less accountability for any comments made.
Anonymity offers the following advantages to internet users:
- It allows people to be more honest and have more honest conversations.
- It allows people to give and receive more honest feedback.
- It allows people to seek help and support on personal or embarrassing issues.
- It allows people to have more balanced conversations with all anonymous users being treated equally.
- It allows people to anonymously whistle blow on illegal activities.

Did you know
In 1999, companies realised that each document created in Microsoft Office contained a global unique identifier (or GUID) which could be linked to specific computers. As a result, employees across the world who believed they had anonymously shared private information or had revealed how their companies were breaking the law, lost their jobs as their identities were revealed.
However, due to a lack of accountability, anonymity also has several disadvantages:
- It can protect people committing crimes or gathering information about illegal activities.
- It can be used for legal but unethical activities.
- It can be used to make statements that are not socially acceptable, without fear of censure.
- It can be used to target and bully specific people.
In 2011, Google implemented a “real names only” policy on Google+ (its social network). This name would then be used across the range of Google’s services, including Gmail and YouTube. The internet was furious and campaigned against the policy for months. After almost a year, Google softened the policy before removing it completely in 2014.
 Activity 11.8
Activity 11.8
11.8.1In your opinion, are cookies beneficial or not? Explain.
11.8.2In 2014, the game developer Zoë Quinn was the target of intense online harassment in a controversy known as Gamergate. As part of the harassment, Zoë’s personal information (including her home address) was posted publicly on the internet while she was receiving thousands of death threats.
Zoë was targeted for harassment because she created a game called Depression Quest which helped people to understand depression. This was not a “proper” game according to some internet users. The harassment then became significantly worse when Zoë’s ex-boyfriend falsely accused her of having a relationship with a gaming journalist to get a positive review for Depression Quest.
Gamergate highlights many of the problems with online anonymity, including bullying and harassment by anonymous online users. However, it also shows how removing anonymity can cause problems, with the harassment becoming personal and threatening once Zoë’s personal relationships and home address were placed on the internet. Answer the following questions:
a.Do you think it is important to keep the internet anonymous?
b.Do you think cyberbullying is something that occurs within your school or community?
c.Would you feel comfortable linking everything you have done on the internet to your real name and surname?
d.Are there any kinds of websites that should force people to use their real name?
e.How would they ensure that users use their real name and surname?
GLOBAL UNIQUE IDENTIFIERS
A GUID (global unique identifier) is a term used by Microsoft. It is a number that its programming generates to create a unique identity for an entity such as a Word document.
GUIDs are widely used in Microsoft products to identify interfaces, replica sets, records, and other objects.
One concern is that an author of a document can be traced by the GUID in the document, even in circumstances where the author has taken care to maintain their anonymity.
FILE SHARING (MOVIES, MUSIC)
The internet is quickly becoming many users preferred source of music, films and other forms of entertainment.
File-sharing sites can cause problems in three ways:
- The free-to-use ones are probably breaching copyright laws (either downloading or uploading is illegal).
- Some sites are used to distribute pornography, racist or other inappropriate or unlawful material, often masked as respectable content.
- These services also enable strangers to gain access to areas of your or your child’s computer, leaving it open to viruses, spyware and ‘botnet’ software.
CONSOLIDATION ACTIVITY Chapter 11: Social implications
Debate one of the following topics:
1.The evolution of social networking has benefitted us globally and personally.
2.Computers can provide solutions to real-world problems.
Role play the following scenario:
Explain to your peer how and why you need to keep your personal information safe. Provide examples to convince your peer to be more cautious when going online on social media sites.
|
Previous
Chapter 10: E-communications
|
Table of Contents |


