8.2 Network security
|
Previous
Chapter 7: Networks and internet technologies
|
Next
Chapter 9: Errors and bugs
|
 CHAPTER OVERVIEW
CHAPTER OVERVIEW
| Unit 8.1 | Social issues for networks |
| Unit 8.2 | Network security |
| Unit 8.3 | Databases and big data |
| Unit 8.4 | Normal currency vs cryptocurrency |
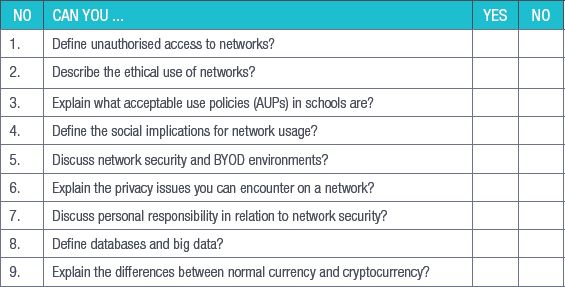
 By the end of this chapter, you will be able to:
By the end of this chapter, you will be able to:
- Define unauthorised access to networks
- Describe the ethical use of networks
- Explain what acceptable use policies (AUPs) in schools are
- Define the social implications for network usage
- Discuss network security and BYOD environments
- Explain the privacy issues you can encounter on a network
- Discuss personal responsibility in relation to network security
- Define databases and big data
- Explain the differences between normal currency and cryptocurrency
INTRODUCTION
We live in a digital world where everything about us, from our holiday pictures to our names and ID numbers, is somewhere on a computer. Companies are storing more of their private information on networks and people are using cloud storage to save more of their personal information online. With the click of a button, you can find out more about strangers on the other side of the world than you ever could before.
This is why network security is more important than ever. In this world, where all the information you need about someone is so easily available, attackers want to get their hands on this information and use it.
UNIT
8.1 Social issues for networks
UNAUTHORISED ACCESS
Unauthorised access on a network is when someone gains access to a network using someone else’s credentials or through other illegal methods. Accessing a network, website, account or service that you do not have permission to access is illegal.
This is why having usernames and passwords and setting up access rights for routers and other connection devices are important. Access to secure data on the network should also be controlled.
Authentication works to protect your personal information from unwanted access. You can protect your computer by setting up a username and password that you will need to enter each time you start it up.
You can also set up authentication for your smartphone and tablet. New types of authentication, beyond usernames and passwords, have made it possible for you to easily secure your devices and access them yourself. New types of authentication include biometrics (fingerprint-unlock or face-unlock) screen-lock patterns and PINs.
In this unit, you will build on your knowledge of authentication by looking at what unauthorised network access is and its negative consequences, how networks must be used ethically and why AUPs (in schools and other environments) are drawn up. We will also discuss network safety and security issues, especially when it comes to BYOD environments and the privacy issues surrounding networks.
ETHICAL USE OF NETWORKS
Since networks are used by a wide range of people, they must be used responsibly and ethically. Anything negative that any user does on a network can reflect negatively on the company, school or organisation whose network they are using. This is why most organisations set up acceptable use policies (AUPs) for those people who will be using their networks, especially when it comes to what users can and cannot do on the internet.
The chances are very high that your school has an AUP that you had to read and then sign or acknowledge in some way. This section will look at the basics of AUPs for schools and what guidelines they should contain. The AUP is there to protect the users (and the organisation) when they use ICT facilities and when they are online.
ACCEPTABLE USE POLICIES OF SCHOOLS
In a school, an AUP can cover a wide range of computing devices and networks and is a contract between the user (learner) and the organisation (school) that outlines what the user can and cannot do on a particular network.
Below are some guidelines that should be in AUPs:
- A list of basic netiquette rules, including not sending spam or hoax emails and how users should communicate using email or social media websites
- What may or may not be accessed online using the school’s ICT facilities. This could include restricting access to social media websites
- How much information users may download from the internet (for example, no live streaming or downloads larger than a certain file size)
- Guidelines on respecting copyright, intellectual property laws and privacy, as well as how to avoid plagiarism
- When and how portable storage devices can be used
- Restrictions on what software can be installed on the school’s computing devices
- What to do if users find that they have become the victims of identity theft, cyber-stalking and cyber-bullying, and what to do if their devices become infected with viruses or malware
- Clear descriptions of what will happen to a user who breaks the rules outlined in the AUP
Each school will have its own AUP depending on the computing devices, services and access they provide.
 Activity 8.1
Activity 8.1
Answer the following questions:
1.How does authentication work?
2.What is an acceptable use policy?
3.Compare your school’s acceptable use policy with the list of guidelines given above. Make a suggestion on how to improve your school’s AUP.
UNIT
8.2 Network security
All networks can be the target of an attack, especially those that connect to the internet. This is why it is extremely important to understand and implement basic network security. In this section you will look at basic things that you can use or do to keep the network secure, for example:
- firewall
- antivirus software
- use passwords and usernames where necessary
- understanding BYOD environments and applying all relevant safety requirements

FIREWALLS
The first and most important is security software for your devices. Firewalls are built into most routers and computers to stop unwanted traffic getting onto your network. Firewalls are basically the security guards of a network. Everything that comes into your network from the internet should be going through a firewall.
All the computers in a network should also have anti-virus software installed to protect them from being infected with malware, viruses and other harmful programs. Anti-virus software constantly scans the programs on a computer and destroys any threats.
Most organisations have network security policies that outline the rules that are in place to protect the network. One of the most common policies is to give staff a username that they can use to log into the network and have them choose a password. When you need to choose a password, there are a few things you must keep in mind:
- The longer your password, the more difficult it is to crack. Make sure your password is at least 10 characters long or use a passphrase that is at least 15 characters long.
- Make sure that your password is something you can remember without needing to write it down. If you need to write your password down, make sure that you keep it hidden and mixed in with other notes, so it is not clear which one is your password. Keep these notes away from your computer.
- Do not use your name, a family member’s name or the name of a pet. A password that cannot be linked to your personal information is the best kind.
- Your password should not be something easy to guess, such as “password” or “12345”.
- Make sure that your passwords are a mix of uppercase and lowercase letters, numbers and special characters.
- Make sure that your passwords do not follow a pattern on the keyboard (such as “asdfgj”).
- Never give out your password to anyone and try not to share your account details with anyone.
- You are responsible for keeping your password safe. Anything that is done on a network using your password and username will be your responsibility. To make sure your passwords are safe, you should change them every two months or so and you should never use the same password for different websites and networks.
 Case study The 2018 Facebook data breach
Case study The 2018 Facebook data breach
Read the case study below and answer the questions that follow.
On the 25th of September 2018, Facebook announced that a security flaw in its website allowed hackers to access the personal data of roughly 90 million users of the social network. The attackers used a vulnerability in Facebook’s “View As” tool, which allows users to see what their profile looks like to other people. By using this vulnerability, the attackers stole Facebook access tokens that they could use to take over almost 50 million user profiles.
An access token is a short line of code stored in your browser or device that keeps you logged into your account without you needing to log in each time you want to access the website that issued it. Facebook quickly patched the bugs in the code that gave the attackers access and logged 90 million users out of their accounts (the 50 million that were compromised and 40 million that were potentially compromised) on the web and on their mobile devices. Users who were logged out were greeted with a message explaining what had happened when they logged back in and a link to more details about the breach. Facebook also temporarily disabled the “View As” feature while they worked to patch up the code.
According to later reports, Facebook security personnel first noticed that something was wrong when they spotted a spike in unusual activity on the 16th of September 2018 and began investigating. The vulnerability had been in place since July 2017, which means that attackers could potentially have had access to the accounts for a long time.
The attack also left vulnerable users’ other accounts where they had used Facebook to login to those sites. Facebook advised users to change their passwords and use their accounts’ security and login page to see where they had been logged in with their Facebook credentials.
This data breach came hot on the heels of another scandal involving Facebook and a company called Cambridge Analytica, where it was found that Cambridge Analytica used the data from 50 million Facebook accounts, kept the data and used it to influence the 2016 American Presidential Campaign.
1.Do you think that Facebook did the right thing by logging users out before informing them of the data breach?
2.How do you think Facebook’s security team could have handled the vulnerabilities better?
3.Do you think that Facebook is doing everything it possibly can to protect its users’ privacy following the two major scandals?
4.What advice would you give to users whose accounts were affected by the data breach?

2018 FACEBOOK DATA BREACH

Cambridge Analytica Scandal: https://www.wired.com/story/wired-facebook-cambridge-analytica-coverage/

BASIC COMPUTER SECURITY PRINCIPLES
NETWORK SECURITY
Any time a network becomes accessible, it becomes vulnerable to attack. This is especially true of networks that connect to the internet. Another security concern for networks is making sure that the devices that connect to them are not making them open to attacks.
When it comes to BYOD environments, this could be difficult, since the network administrator does not have full control over what is done with those devices when they are taken home at the end of the day,
This section therefore looks at network and safety issues related to BYOD and privacy, and how they can be prevented.

Something to know
Microsoft Intune is a cloud service from Microsoft that helps organisations to manage the mobile devices that employees use to access the organisation’s data and applications, thereby protecting their mail and data.
NETWORK SECURITY AND BYOD
The main concern with personal devices that are used for work is how to keep the company’s private data separate from a user’s personal data and how to make sure that an employee does not accidentally share that private data. One way to avoid this is to set up a data loss prevention policy and using data loss prevention tools. Organisations can also use mobile device management software, such as Microsoft Intune, to manage the devices on their networks.
Another concern is that most mobile devices, such as smartphones and tablets, might not have anti-virus software installed, or, if there is anti-virus software, it is not up to date. This becomes a problem when users accidentally download applications that contain malware, adware or spyware. Mobile devices can also become infected with viruses. When these devices connect to the network, they can spread the infection, making the network unsecured.
The last issue with BYOD environments is that employers cannot control what employees install on their devices. Employees may be able to install games or other media that can become a distraction at work.
Because of these issues, companies that use a BYOD policy must set up a clear AUP for their staff regarding what they can and cannot do with their devices.
PRIVACY ISSUES
With so much of what you do every day taking place on computers and online, privacy and who has access to your information has become a major issue. Networks have become powerful tools to access, collect, store and share personal data. Very often this data is used to provide a company’s customers with a better service, or to make it easier and quicker for your doctor to access your medical history, for example. But this data can also be used by cyber-criminals to commit fraud or to steal.
It is the network owner’s responsibility to make sure that the data their network stores and shares is accessed legally and that this data is only used for what they say its use will be. It is also their responsibility to make sure that this data is secure and safe.
PERSONAL RESPONSIBILITY
While it is true that network administrators must make sure that their networks are secure, you also have a responsibility to make sure that you do not expose a network you are using to attacks.
You do this by keeping the following tips in mind when using a network:
- Make sure that your devices have up-to-date antivirus software installed and that you never click on suspicious links or reply with personal information to suspicious emails.
- Respect others’ privacy and products. Do not download or share content that has been obtained illegally (such as pirated movies or music) or content that violates someone else’s copyright.
- Be careful what your share about yourself on the internet.
- Follow the AUPs of any network you are using.
If you keep these tips in mind, you can help make the networks you use more secure for everyone else.
 Activity 8.2
Activity 8.2
1.What are the main concerns with BYOD policies in the workplace?
2.How can companies avoid security and usage issues in a BYOD environment?
3.List two tips you should keep in mind when using a network.
UNIT
8.3 Databases and Big data
DATABASES
Networks must be protected to safeguard the personal information stored on them. This is especially true of networks that have databases, since these are where personal information is stored. Databases are often the targets of cybercrimes, so database security is extremely important.
The foundation of database security is the confidentiality, integrity and availability (CIA) triad:
- Confidentiality is the most important aspect of database security. People should be able to trust that any information about them that is stored is safe and secure. Databases should be encrypted to make sure that this is the case.
- Integrity is another important aspect of database security. Integrity means that the data can only be accessed by people who have the correct permissions to view it. This can be done by making sure that access to the data is controlled.
- Availability means that the databases should be up and running when users need to access them. This means that any downtime should be scheduled and if there is unexpected downtime, database administrators should check that this is not due to a security breach.

BIG DATA EXPLAINED

What is big data and how is it used? https://www.bernardmarr.com/default.asp?contentID=766
BIG DATA
Big data, a term that describes the massive amounts of data that are generated every day by every single person, plays a major role in privacy concerns. More and more companies are collecting this data and storing it on databases to use in marketing or product development. Big data is used in online services like:
- Online banking: Proper analysis of big data can help detect any and all the illegal activities that are being carried out, like the misuse of credit cards, misuse of debit cards, customer statistics alteration and money laundering.
- Booking reservations: Big data from several sources has helped travel agencies, hotels and the tourism industry better understand what customers are looking for and this has led to more direct reservations.
- E-learning: Big data that is being collected is related to the students, faculties, courses and results. This can provide insights to improve the effectiveness of educational institutes.
- Social websites: Users of social websites share photographs, personal data and make comments on posts by other users. This information is used by social websites to provides users with personalised content and also to assist advertisers to hyper-target users.
Companies also capture big data on consumer habits for targeted marketing. This has raised concerns about privacy because every time you click on a website, post on social media, use a mobile app and comment via email or to call centres, your data is collected for future use. People have a right to their privacy but, without their knowledge or consent, this right is being eroded.
As big data increases, it exposes more of our data to potential security breaches. For example, if you have approved a company to analyse your data, how certain are you that they will not fall prey to a cyber-attack or that they will not sell your data. This could result in your private data being in unsafe hands.
 Activity 8.3
Activity 8.3
In small groups discuss if and how big data has social implications for:
- Online banking
- Booking reservations
- E-learning
- Video conferencing
- Social websites
UNIT
8.4 Normal currency vs cryptocurrency
In the past few years, cryptocurrencies such as Bitcoin and Etherium have captured the general public’s attention, but what is a cryptocurrency and how is it different from the normal currency you can get from a bank?
Simply put, cryptocurrency is a digital currency that can be bought, sold and traded online using cryptography. Cryptography takes the identifying data of the people buying and selling cryptocurrency and transforms it into something that is not readable unless it is deciphered. Cryptocurrencies are completely digital and have no physical form, unlike the money you get from the bank.
Normal currency is also usually backed by something physical that gives it value, like gold, and is usually issued and supported by a country’s central authority or bank (in South Africa, that would be the Reserve Bank and the government). Normal, or fiat, currency is usually referred to as legal tender and has a value on the world’s stock markets as well.
Cryptocurrencies are not backed by a single country’s central authority and their value is not tied to anything physical. This means that they are decentralised and global.
Cryptocurrencies, however, are finite. There is only so much of it to go around.

Something to know
Bitcoin, the most popular cryptocurrency, was created in 2008 and remained mostly unknown. A few years later, Bitcoin mining became a popular pastime for computer enthusiasts and the popularity of Bitcoin grew. The value of Bitcoin in real world currency began to grow exponentially. In January 2017, a single Bitcoin would cost you $800 (about R11 104 in 2018). By the end of 2017, however, the price had skyrocketed until one Bitcoin cost $13 000 (about R180 000 in 2018)!
 Activity 8.4
Activity 8.4
1.What does the term “Big data” mean?
2.Distinguish between normal currency and cryptocurrency.
REVISION ACTIVITY
QUESTION 1: MULTIPLE CHOICE
1.1Which of the following is NOT used to authenticate a user? (1)
A.Username
B.Password
C.PIN
D.BYOD
1.2Which of the following techniques cannot be used to authenticate user access to your smartphone? (1)
A.Fingerprint scanner
B.Identity card
C.Screen-lock pattern
D.PIN
1.3Which of the following scenarios will need an AUP? (1)
A.A person wants to sell goods online.
B.A person wants to open an internet café.
C.A person buys car insurance.
D.A person browses an online website.
1.4What does BYOD mean? (1)
A.Bring your own device
B.Buy your online device
C.Bring your device
D.Bypass online detection
1.5What is the purpose of a firewall? (1)
A.It removes malware from your computer.
B.It uninstalls programs from your computer.
C.It updates your computer’s software.
D.It prevents outside devices or programs from accessing your network.
QUESTION 2: TRUE OR FALSE
2.Write True or False next to the question number. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word NOT to change the statement.)
a.Authentication is the process of working out whether something or someone is, in fact, what or who they claim to be. (1)
b.Using a network in an unethical manner can improve the reputation of an institution. (1)
c.On a network you must protect the privacy of others and yourself. (1)
d.Unauthorised access on a network is when someone legally gains access with another user’s password. (1)
e.There are two main types of unauthorised access, internal and external threats. (1)
QUESTION 3: MATCHING ITEMS
Choose a term/concept from Column B that matches a description in Column A. Write only the letter next to the question number (e.g. 1J). (5)
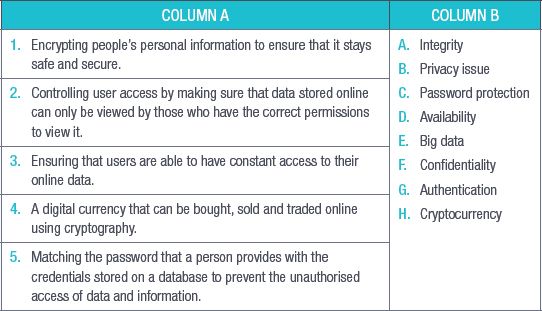
QUESTION 4: MEDIUM QUESTIONS
4.1Name three types of institutions that would benefit from AUPs. (3)
4.2List three AUP guidelines that should be used by schools. (3)
4.3Name three advantages of cryptocurrencies over normal currencies. (3)
QUESTION 5: SCENARIO-BASED QUESTIONS
Stacy has recently had a friend of hers install a network in her house. Since she has a four-year-old daughter and a 14-year-old son who will eventually have access to this network, she needs to work out what safety precautions she must implement.
5.1What type of network should Stacy install? Give a reason for your answer. (2)
5.2What three things can Stacy do to keep her network secure? (3)
5.3What two things can Stacy do to control what her children can access on their home’s network? (2)
5.4Stacy’s son has created a Facebook account. What three safety tips can Stacy give him about his use of this online platform. (3)
5.5Stacy’s son comes to her and tells her that he thinks that someone has hacked into his Facebook account. What three things should they do? (3)
5.6Give three guidelines that Stacy can use when choosing a password that will be difficult to crack. (3)
TOTAL: [40]
AT THE END OF THE CHAPTER
|
Previous
Chapter 7: Networks and internet technologies
|
Table of Contents |
Next
Chapter 9: Errors and bugs
|



